oretnom23 Fast Food Ordering System has an input filter that sanitizes user-supplied data prior to processing. Unfortunately, input validation fails to cover all possible cases. This results in sql injection. An attacker can exploit this vulnerability to run arbitrary code on the target system. It is strongly recommended to upgrade the system as soon as possible. A patch for this issue has been released. All users are advised to apply it as soon as possible.
Demonstration of the security flaw VDB-207422 has been released. It shows how to exploit the oretnom23 Fast Food Ordering System sql injection vulnerability. This could be exceedingly dangerous if left un-fixed.
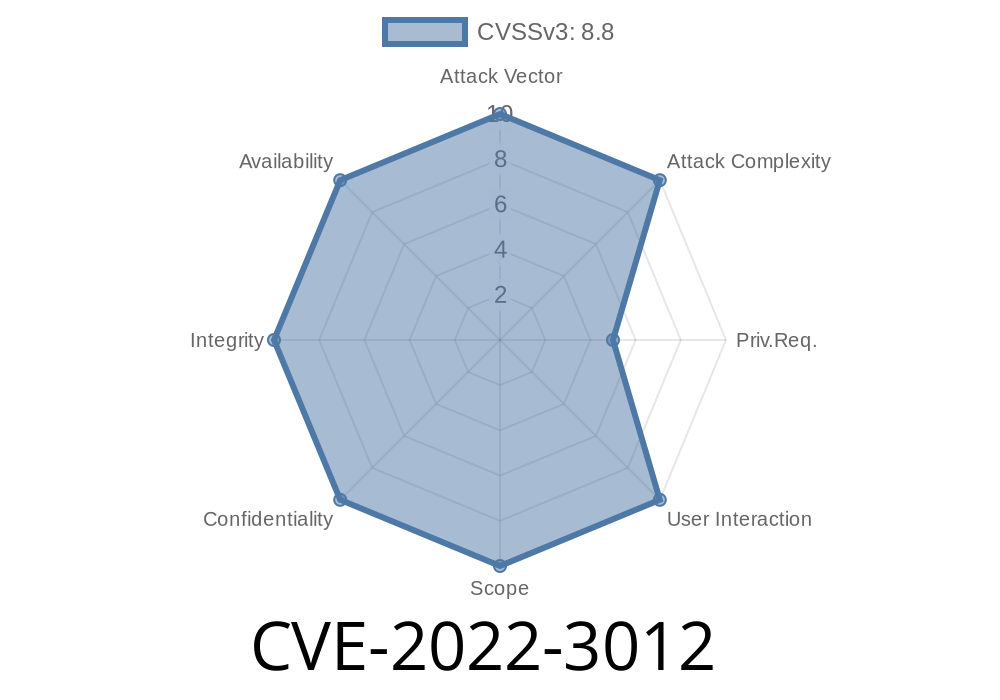
References: CVE-2022-3012
VDB-207422
SQL Injection on oretnom23 vulnerable web-application
SQL injection is a vulnerability in which an attacker can execute arbitrary SQL commands to access or modify data in an application.
A demonstration of the security flaw on oretnom23 Fast Food Ordering System has been released. It shows how to exploit the oretnom23 Fast Food Ordering System sql injection vulnerability.
Vendor description:
Oretnom23 Fast Food Ordering System is an open source, web-based, point-of-sale system. "The point-of-sale system is a virtual storefront that allows users to create and manage orders in real time. Orders are created with the customer's specifications, then sent to the processing center (i.e., the restaurant) via wireless technology."
Timeline
Published on: 08/27/2022 09:15:00 UTC
Last modified on: 08/31/2022 19:18:00 UTC