It is a critical remote code execution vulnerability in the Node.js-based server for the development of software. It affects all the versions of the server from v0.12.11 up to the latest v10.14.2.
The vulnerability was discovered by Alibaba, the Chinese e-commerce giant. The company is responsible for developing the software to power the online shopping sites like Taobao, Tmall and Alibaba Cloud.
The remote code execution vulnerability can be exploited by an attacker by sending a specially crafted HTTP request. It can be done by injecting a malicious script into the context of a target application.
In order to exploit this vulnerability, the attacker needs to send a specially crafted HTTP request to the targeted server. The request should include one or more HTML tags that are used to control the flow of execution.
By injecting this sort of request into the server’s response, the attacker can control the flow of execution and can do anything he wants.
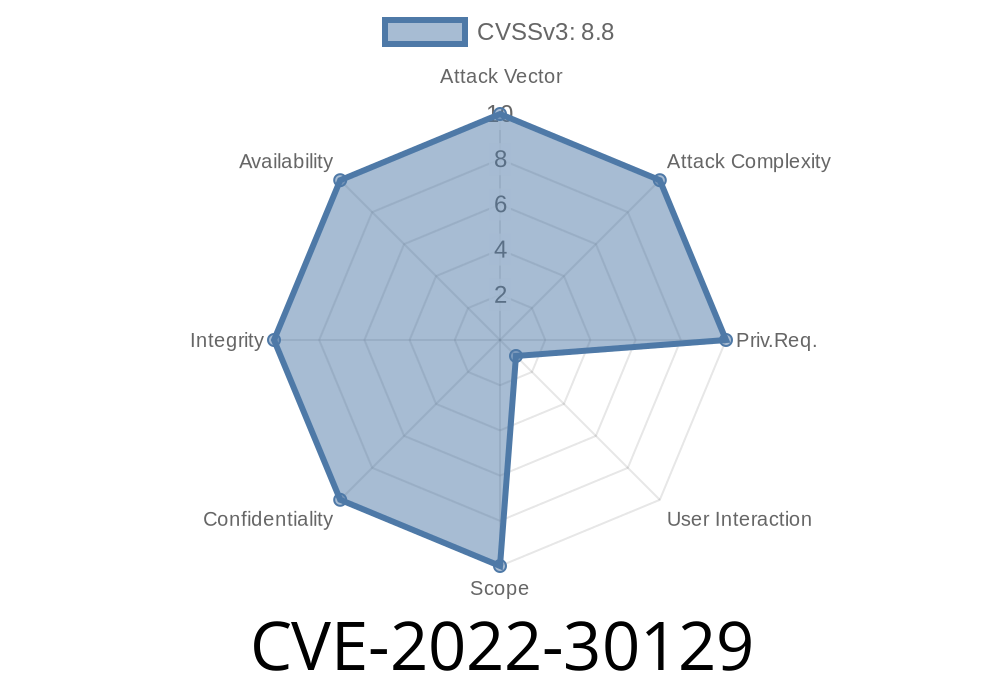
Vulnerability details
The vulnerability has been assigned the CVE-2022-30129 identifier.
The vulnerability was discovered by Alibaba, the Chinese e-commerce giant. The company is responsible for developing the software to power the online shopping sites like Taobao, Tmall and Alibaba Cloud.
The remote code execution vulnerability can be exploited by an attacker by sending a specially crafted HTTP request. It can be done by injecting a malicious script into the context of a target application.
In order to exploit this vulnerability, the attacker needs to send a specially crafted HTTP request to the targeted server. The request should include one or more HTML tags that are used to control the flow of execution.
By injecting this sort of request into the server’s response, the attacker can control the flow of execution and can do anything he wants.
Node.js Remote Code Execution Vulnerability
A remote code execution vulnerability in Node.js, the popular JavaScript-based server runtime engine, has been discovered by Alibaba. This vulnerability affects a wide range of server versions including v0.12.11 to the latest v10.14.2 and can be exploited by sending a specially crafted HTTP request that will result in arbitrary code execution on the target system. The vulnerability is being actively exploited by hackers due to zero day exploits not yet available for patching and can be triggered via malicious HTML tags which can be used to hijack the flow of execution and execute arbitrary code on the target system with low privileges as well as other resources like user input or data storage like databases.
Node.js is an open-source cross-platform JavaScript runtime environment that is currently used in many web servers and has been found vulnerable to this type of attack since it was first discovered in 2014. The vulnerability is being actively exploited by hackers due to no fixes for patching them yet, but should provide enough information for people and software developers to create patches for stopping this vulnerability from being exploited going forward with new updates coming out soon according to Alibaba themselves
How Does Node.js Remote Code Execution Vulnerability Work?
This vulnerability affects all the versions of the Node.js-based server. The vulnerability is present when a program which is written in JavaScript (Node.js) and hosted on the server executes an HTTP request that includes one or more HTML tags that are used to control the flow of execution.
The attacker needs to send a specially crafted HTTP request with this flaw, which will cause such JavaScript code to execute without any restrictions. The attacker can then use this flaw to do anything he wants with the permissions of this code, such as stealing information and reading files from the server or even installing malware on it.
How Does Node.js-Based Server Vulnerability Work?
A remote code execution vulnerability in the Node.js-based server for the development of software was discovered by Alibaba, the Chinese e-commerce giant. The company is responsible for developing the software to power the online shopping sites like Taobao, Tmall and Alibaba Cloud.
The vulnerability affects all versions of this server from v0.12.11 up to the latest v10.14.2 and can be exploited by an attacker by sending a specially crafted HTTP request with one or more HTML tags that are used to control the flow of execution.
To exploit this vulnerability, the attacker needs to send a specially crafted HTTP request to the targeted server and should include one or more HTML tags that are used to control the flow of execution. By injecting this sort of request into the server’s response, it allows him to control the flow of execution and do anything he wants.
What is Node.js?
Node.js is a JavaScript runtime environment that is built on Chrome's V8 JavaScript engine. Node.js provides an event-driven, non-blocking I/O model that makes it lightweight and efficient to develop network applications using JavaScript. It uses an event loop with long-lived I/O threads.
Node provides a platform for writing scalable network applications in server and client sides.
Timeline
Published on: 05/10/2022 21:15:00 UTC
Last modified on: 08/25/2022 13:15:00 UTC