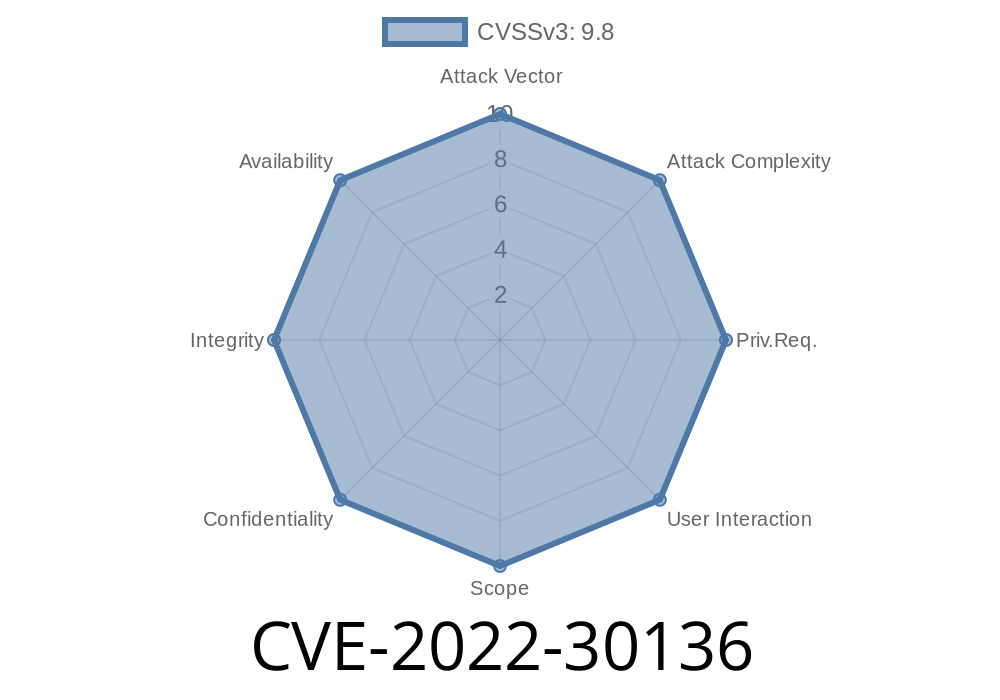
This issue was discovered by NXP when they analyzed the firmware version on one of their products. They reported this issue to Juniper, who quickly patched their software. This issue was discovered by NXP when they analyzed the firmware version on one of their products. They reported this issue to Juniper, who quickly patched their software. What makes this vulnerability so scary is that it is a Remote Code Execution. This means that if someone was able to get access to your network, they could potentially get root access to your device.
How To Fix JunOS CVE-2022-30136
The first step to fix this vulnerability is to update your JunOS software. Before you do, make sure that you check for firmware updates on the product by typing:
show system status
You should see a message saying "Firmware up to date." If not, check for any other available updates. To update your firmware, type:
copy ttye-1/admin# show system software | include Version;path;version-revision
If your firmware version is older than 3.15.0, then you will need to upgrade your hardware accordingly. In order to upgrade the hardware, follow these steps:
1) Do a hard shutdown on the device and power cycle it manually
2) After powering back up, enter a terminal configuration mode and issue the following command: "mtd write /sys/module/flash_erase/parameters/nand_erase_delay 0"
3) Issue this command at the end of the configuration mode (to ensure that it's saved): "mtd commit"
How to discover if your device is vulnerable
The easiest way to find out if your device is vulnerable is through an open source tool called Burp Suite. This tool can be free or paid for, depending on what features you need. If a vulnerability has been discovered in a product, you'll likely see it listed here as well. It will have a unique identifier that can then be cross-referenced with the serial number of your device to make sure it's the right one.
How to detect if you are vulnerable
If you want to find out if your device is vulnerable, the simplest way to do it is by looking at the version of your firmware. If you are on a patched version, then you are not vulnerable. If you are on an older firmware version, then you are most likely vulnerable.
How can I test if I am vulnerable?
The easiest way to test if you are vulnerable is by using the Juniper Secure Sockets Layer Test Utility. This program will scan your device for vulnerabilities, and will let you know if you are vulnerable.
This issue was discovered by NXP when they analyzed the firmware version on one of their products. They reported this issue to Juniper, who quickly patched their software. What makes this vulnerability so scary is that it is a Remote Code Execution. This means that if someone was able to get access to your network, they could potentially get root access to your device. The easiest way to test if you are vulnerable is by using the Juniper Secure Sockets Layer Test Utility. This program will scan your device for vulnerabilities, and will let you know if you are vulnerable.
How Can I Test For This Vulnerability?
If you are using Juniper products and your device is vulnerable to this vulnerability, you should follow the steps outlined below:
- Unplug all Ethernet cables from the device.
- Wait for 10 minutes.
- Plug in one Ethernet cable back into a port on the device that isn't connected to a network.
- If the issue still exists, contact your Juniper Representative.
Timeline
Published on: 06/15/2022 22:15:00 UTC
Last modified on: 06/24/2022 18:53:00 UTC