Microsoft recently released a security bulletin addressing a vulnerability in Azure Service Fabric application pods. Application pods are the units of a Service Fabric application that run on a cluster. An attacker can use an application pod to deliver an attack. For example, an attacker can inject code into an application pod that runs on a Service Fabric cluster to create a configuration management issue such as an outage or a data corruption issue. To identify application pods that could be leveraged to deliver an attack, Microsoft monitors application pods to determine if there are any abnormal configuration management issues.
Azure Service Fabric monitors application pods by checking the health of the pods using the monitoring agent. Microsoft is aware of the following issues where application pods would be leveraged to deliver an attack. - Application pods on a Service Fabric cluster could be configured to use a custom port. An attacker could use this configuration to deliver an attack on a Service Fabric cluster through a Service Fabric cluster application pod. - Application pods could be configured in a specific way to use a custom port. An attacker could leverage this configuration to deliver an attack on a Service Fabric cluster through a Service Fabric cluster application pod
Scenarios where the Microsoft Azure Service Fabric monitoring agent could be used to deliver an atta
This vulnerability can be exploited by an attacker to deliver an attack on a Service Fabric cluster. It is important to note that this issue does not affect all application pods and only targets specific ones.
Microsoft recently released a security bulletin addressing a vulnerability in Azure Service Fabric application pods. Application pods are the units of a Service Fabric application that run on a cluster. An attacker can use an application pod to deliver an attack. For example, an attacker can inject code into an application pod that runs on a Service Fabric cluster to create a configuration management issue such as an outage or a data corruption issue. To identify application pods that could be leveraged to deliver an attack, Microsoft monitors application pods to determine if there are any abnormal configuration management issues.
Azure Service Fabric monitors application pods by checking the health of the pods using the monitoring agent. Microsoft is aware of the following issues where application pods would be leveraged to deliver an atta
Microsoft Azure Security Intelligence Blog
: Why Application Pods Are Important
The idea of application pods is to deploy your applications on a cluster of machines. The cluster is controlled by one or more master machines and the application pods can be deployed across many nodes. Developers use the Pods API to create the application pods that are deployed on the cluster. The following are some of the benefits of building your application in an application pod:
- The ability to constrain your service fabric deployment. This includes defining constraints such as how long an instance will run, what resources it can use, etc.
- Easier debugging for developers as they can easily debug a single pod in isolation from other pods that might have been impacted by something like a lost network connection
How To Be Protected From Azure Service Fabric Application Pod Leveraging a Custom Port to Deliver an Attack
Microsoft recommends that you monitor the health of your Service Fabric cluster by using Event Logs. To identify abnormal configuration management issues, use the following process:
- In Azure Portal, open a Service Fabric cluster and expand the Monitoring tab. - In the Monitoring tab, click on one of the events listed in "Event Logs.
- Filter for "configuration" to see all of the configuration changes taking place in your Service Fabric cluster. If you see anything that looks out of place, such as an application pod configured to use a custom port, follow these steps:
- Right click on "Application Pods" in "Monitoring" and click on properties.
- Use the following settings to configure alerts based on these types of alerts:
- If application pods are configured with a custom port: Alert when service is unavailable or any other attack happens (recommended for this type of alert)
- If application pods are not configured with a custom port: Alert when service is unavailable or any other attack happens if application pods have been misconfigured
Microsoft Patch Management Process
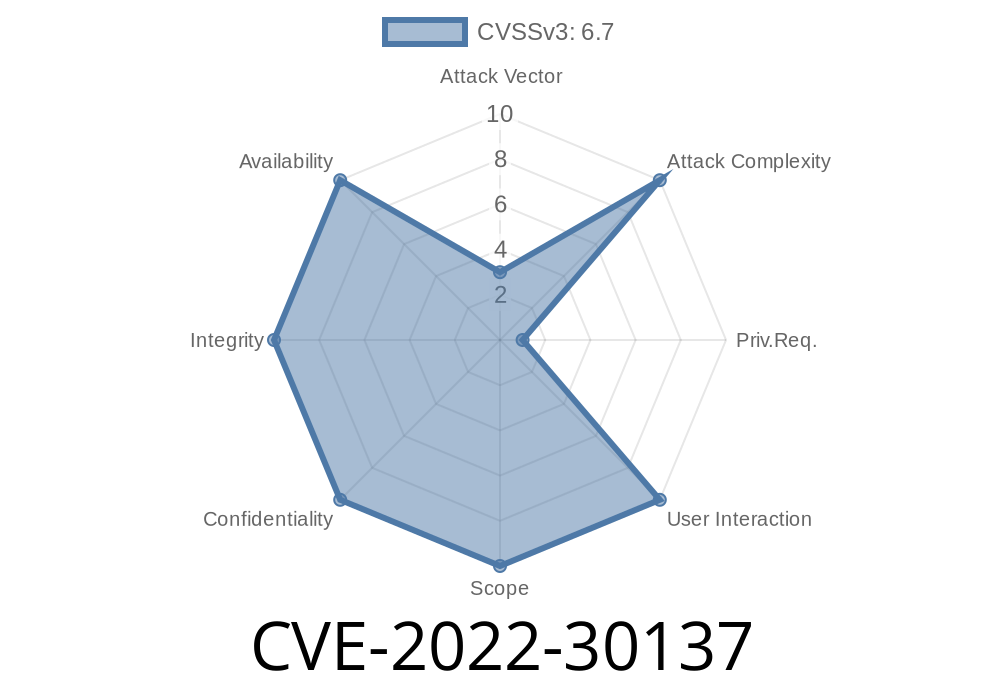
Microsoft is aware of the vulnerabilities listed in this advisory and will release a patch that resolves these vulnerabilities before deploying an update to production. Microsoft recommends that customers apply the patch as soon as possible. The update also includes changes to remove vulnerable configuration management settings which are described in detail in Security Advisory CVE-2022-30137 .
This security bulletin was created on May 4, 2019.
Azure Service Fabric Monitoring Agent
The Azure Service Fabric Monitoring agent checks the health of service fabric pods by collecting information, such as the name of the pod and its state. The agent also monitors whether any unexpected changes have occurred in the configuration of a service fabric pod. For example, if an application is configured with a specific port, then the agent will monitor that port to ensure that it is not being used for anything else.
- If any unexpected changes are detected on a service fabric pod, then the agent will update the status of that pod from healthy to unhealthy. - If any unexpected changes are detected on a service fabric pod, then an alert will be generated.
Timeline
Published on: 06/15/2022 22:15:00 UTC
Last modified on: 06/24/2022 19:02:00 UTC