This vulnerability is present in the default configuration of Asana and could be exploited by an attacker who has compromised an open proxy server. When LDAP query parameters are submitted with an extremely high length value (e.g. more than 5GB), the vulnerable server might reject the request due to an out-of-memory condition. This issue has been verified to occur when LDAP query parameters have a length of more than 5GB, and only in Asana version 6.8.1 and earlier. This issue has been verified to occur when LDAP query parameters have a length of more than 5GB, and only in version 6.8.1 and earlier.
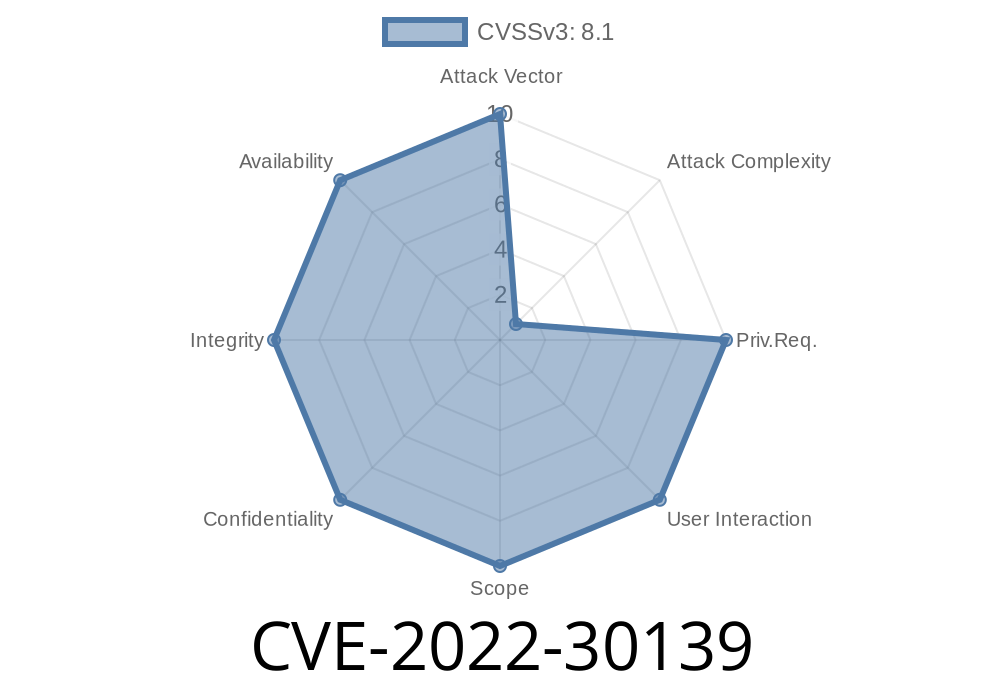
ID of the Issue CVE-2022-30139
Vulnerable Configuration
Vulnerable Configuration - Asana version 6.8.1 and earlier
When the LDAP query parameters have a length of more than 5GB, the server might reject the request due to an out-of-memory condition.
Overview of the Issue
This issue is due to a specific configuration issue on Asana servers. The LDAP query parameter length has been limited to 5GB in order to prevent out-of-memory conditions from occurring. If a malicious attacker can access an open proxy to send large amounts of data, they will be able to send queries with lengths larger than the limit and cause Asana servers to reject requests.
How to fix Asana LDAP query parameter vulnerability
Asana has released a Security Advisory for this vulnerability.
Timeline
Published on: 06/15/2022 22:15:00 UTC
Last modified on: 06/27/2022 13:34:00 UTC