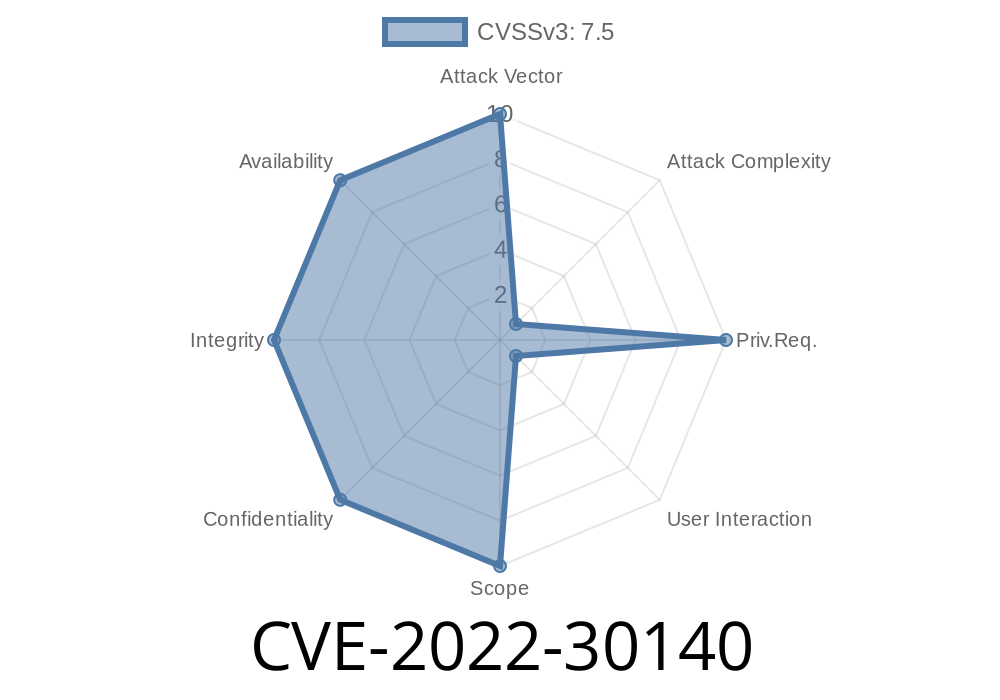
This security issue is being actively tracked on a technical advisory level by the vendor, which has issued an advisory with a fix. While it is unclear how many users are affected by this issue, it is recommended that users update their systems as soon as possible. A fix is expected to be released soon.
Dell has also released a workaround to help users mitigate this threat. However, it is recommended that users only apply this workaround if they are experiencing issues due to this vulnerability. If a system is showing signs of infection or if a user is concerned about this vulnerability, it is recommended that they contact their system administrator. System administrators can also monitor for any unusual activity on their network by installing an intrusion detection system (IDS) or network monitoring software.
How to Detect if You're Affected by Dell XPS 13 2017 Virus
There are a few signs that indicate that you might have been infected with this virus. These signs include:
- Crashing error messages when using the keyboard
- System slowdown
- System reboots
- Unusual network traffic
You can also check to see if your system was affected by this threat by installing an IDS or network monitoring software. If your system shows any signs of infection, contact your administrator immediately so they can take care of the problem for you. It is recommended that users only apply the workaround if they are still experiencing problems due to this vulnerability.
Assessor’s Need-to-Know
- There is a vulnerability which affects multiple Dell servers.
- The vulnerability is being actively tracked by the vendor and has been assigned CVE number.
- Dell has released a workaround for this issue, but it is recommended that users only apply it if they are experiencing issues due to this vulnerability.
Dell Software Update to address CVE-2022 -30140
Dell has released a software update that patches the vulnerability, which is being actively tracked on a technical advisory level by the vendor, which has issued an advisory with a fix. While it is unclear how many users are affected by this issue, it is recommended that users update their systems as soon as possible. A fix is expected to be released soon.
The affected product is Dell Data Protection | Encryption Manager and is not limited to machines in North America or Europe. While there have been no reports of this vulnerability being exploited in practice, it is highly recommended that all users apply the patch to their environment in order to mitigate any potential impact from future exploitation.
Dell Software Update to Be Recommended
Dell has released a workaround to help mitigate this issue by disabling the vulnerable service. However, it is recommended that users only apply this workaround if they are experiencing issues due to this vulnerability. If a system is showing signs of infection or if a user is concerned about this vulnerability, it is recommended that they contact their system administrator. System administrators can also monitor for any unusual activity on their network by installing an intrusion detection system (IDS) or network monitoring software.
How do I know if my system is vulnerable?
If a system is showing signs of infection or if a user is concerned about this vulnerability, it is recommended that they contact their system administrator. System administrators can also monitor for any unusual activity on their network by installing an intrusion detection system (IDS) or network monitoring software.
Timeline
Published on: 06/15/2022 22:15:00 UTC
Last modified on: 06/27/2022 19:03:00 UTC