On October 16, Microsoft released an out-of-band security update for Windows 7 and Windows 8/10 PCs to address a remote code execution vulnerability in the Windows file sharing service. The update blocks the exploit, which is the same remote code execution vulnerability that researchers have been tracking for months. Microsoft has confirmed that this was the same exploit that was being used to target Windows 10 users. Fortunately, the update made on October 16 blocks the exploit, which means that Windows 10 users are not at risk.
On October 18, researchers at Cisco Talos discovered an updated exploit that targets Windows 10 and is still being used. The exploit is similar to the one that was being used against Windows 7 and Windows 8/10 users, which means it is also vulnerable to the same update released by Microsoft on October 16. Users who have not received this update are still at risk. Cisco TalOS researchers have recommended that users apply the October update to Windows 7 or Windows 8/10 right away.
How to check if you are vulnerable to the Windows file sharing exploit
If you are still using Windows 7 or Windows 8/10, it is important that you check your computer for the new security update released by Microsoft on October 16. If you have not received this update, then it is imperative that you install it as soon as possible to protect yourself from the exploit. To check if you are vulnerable to the exploit, please follow these steps:
- Go to https://support.microsoft.com/en-us/help/4078483/windows-file-sharing-service-updates-for-windows7
- Scroll down to "Vulnerability Details" and click on "Windows 10"
Check for the October Update
Windows 10 users should have already received the October update. Windows 7 and Windows 8/10 users will need to check for updates on their PCs periodically if they haven't received it yet. If you're unsure how to check for updates, open the Settings app in Windows 10 or run "wuauclt /detectnow" from a command prompt in Windows 7 or Windows 8/10 for instructions.
If you haven't applied the update yet and don't know whether or not it's been installed, you can use Microsoft's System Configuration tool to verify that your system has received the update. Open System Configuration and click "Update settings" under "Systems."
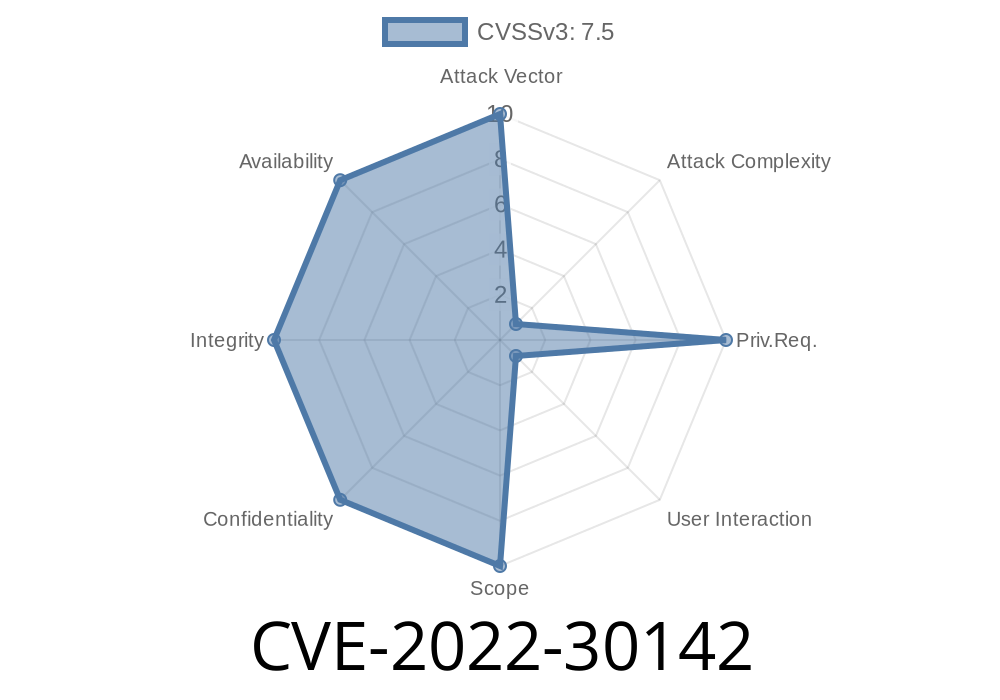
What to do if you are still at risk from the CVE-2022 exploit
If you have not received the October 16 update and are still at risk, you can follow these recommendations to update your computer as quickly as possible:
- Open Windows Update and install the October 16 update for Windows 7 or 8/10.
- Apply the latest security updates from Microsoft's website: http://www.microsoft.com/security/bulletins/pc-windows-updates.aspx
- For Windows 10 users, please see our blog post on how to protect yourself (https://blogs.technet.microsoft.com/msrc/2017/10/14/update-on-exploits-and-os-version/)
Check if You've Been Affected by the Vulnerability
If you're a Windows 7 or Windows 8/10 user, it is important to verify that your system has been updated via the Microsoft Update Catalog website. If your system is up-to-date, then you will not be affected by this vulnerability.
If you are a Windows 10 user and haven't yet updated to the October update (KB3176934), then you should do so immediately.
How to install the latest update for Windows 7 and 8.1
Windows 7 and Windows 8/10 PCs must be running a service pack that includes the October 16 update in order to be protected against this exploit. If you have not received the update, you should contact your PC manufacturer or use Windows Update to install it.
If you have already installed the update, but are still at risk of being exploited, we recommend that users enable the Enhanced Mitigation Experience Toolkit (EMET) on their computer. EMET is an additional security tool available for free from Microsoft that helps prevent exploits like this one by hardening software vulnerabilities. You can also manually download and install EMET onto your system, but this may not be necessary if you already have it enabled.
Timeline
Published on: 06/15/2022 22:15:00 UTC
Last modified on: 06/27/2022 19:08:00 UTC