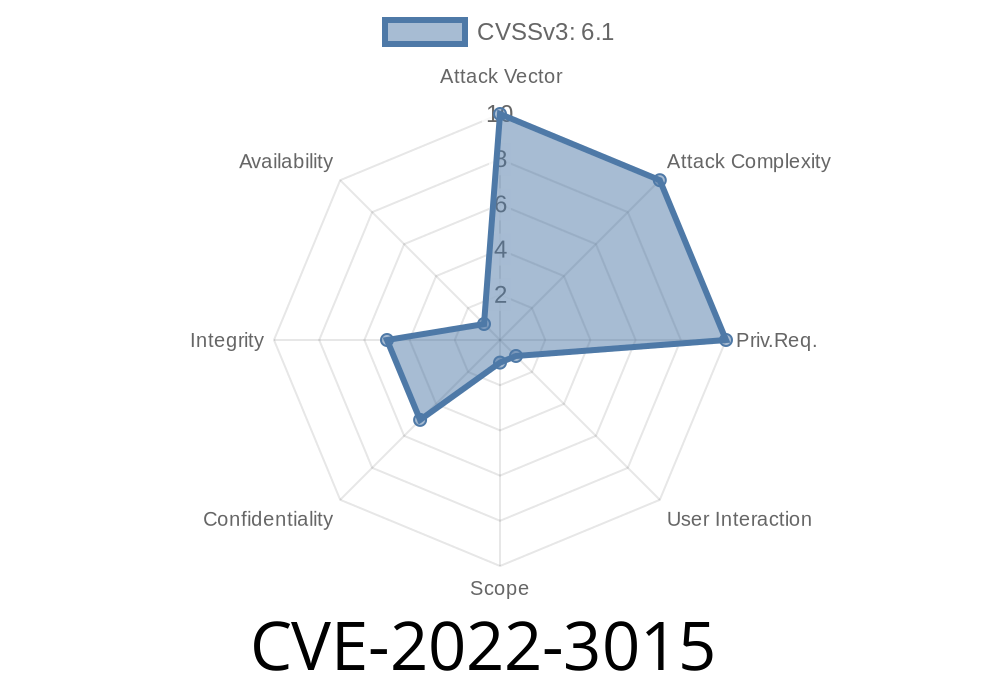
In order to exploit the vulnerability, a remote attacker needs to get access to the targeted system. This may be possible if you leave the system open for visitors or if it is accessible via the Internet. The second way is to exploit vulnerabilities during the software installation. If you use third party applications, be careful. Some of them may be used by hackers to exploit the oretnom23 Fast Food Ordering System bug. Maintenance of the system and application updates are the best ways to protect the device from the oretnom23 Fast Food Ordering System attack.
How to protect your system from Fast Food Ordering System attack?
In order to protect your system from this type of attack, it is important to check the software updates on a regular basis. Sometimes, security vulnerabilities are not detected by an application update. That is why you should always run a scan for malware in order to detect any potential threats that may be installed on the system. In addition, you should also keep your devices and systems up-to-date with the latest patches and updates.
If you want to protect yourself from such attacks, you can install a firewall or antivirus program on your computer which will help prevent hackers from gaining access to your system.
How oretnom23 Fast Food Ordering System Works?
The oretnom23 Fast Food Ordering System is the software that runs on the system. It is used to process orders from restaurants. The vulnerability is in the way it handles input from a customer's device. The attacker can send an HTTP request to the server containing two or more parameters with a single semicolon between them, like this:
/secure/system/submitOrder?name=Burgers&quantity=1&location=3
This will cause the system to create a new order with those values.
What is oretnom23 Fast Food Ordering System?
Oretnom23 is a business software that allows customers to order food from fast-food restaurants and receive the order in less than 30 seconds.
The vulnerability was fixed on October 13, 2017.
Timeline
Published on: 08/27/2022 09:15:00 UTC
Last modified on: 08/31/2022 19:18:00 UTC