This is a remote code execution vulnerability. A remote attacker could exploit this vulnerability by sending malicious request to an affected system.
The Microsoft Windows operating system supports the elevation of privilege for a process by using a Windows Advanced Local Procedure Call (ALPC).
ALPC is a Windows API that supports the launching of programs at a specified location in the operating system. It is often used for authentication, logging, and other administrative tasks.
ALPC provides a restricted set of functions that can be used by a process to perform administrative tasks. For example, a web server process in Windows can use ALPC to authenticate users and perform other administrative tasks.
It is possible for an attacker to exploit ALPC to elevate privileges and perform administrative tasks. An attacker can send malicious request to an affected system and exploit this vulnerability to run arbitrary code in the context of the affected system.
We recommend installing the updates immediately.
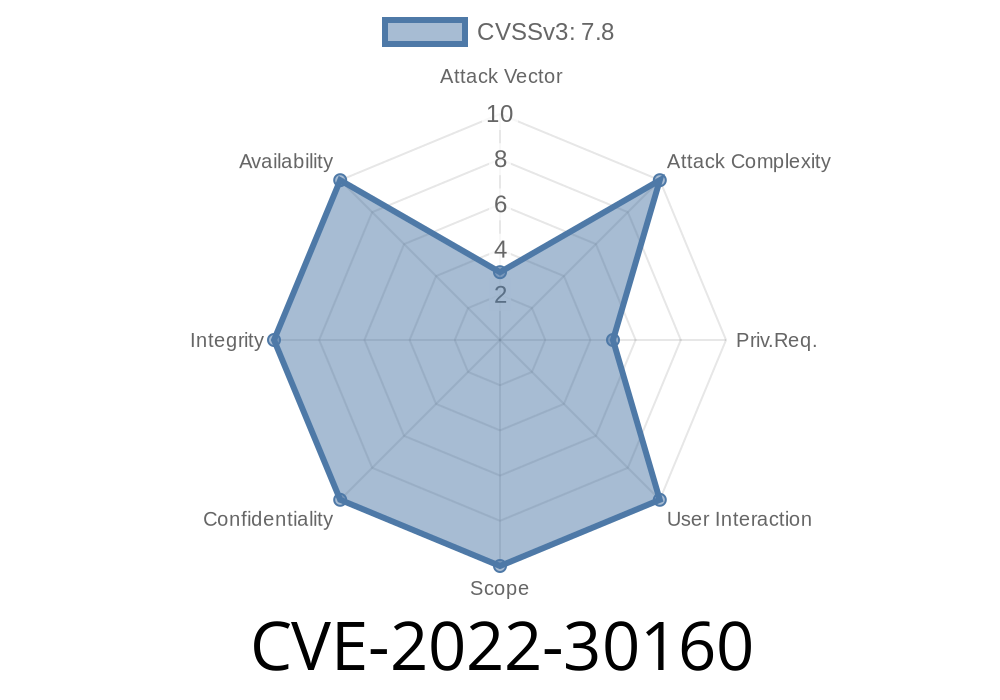
Windows ALPC Elevation of Privilege Vulnerability – CVE-2022 -30160
Microsoft has released a security advisory for a vulnerability that could enable an attacker to elevate privileges and run arbitrary code in the context of the affected system. The vulnerability, CVE-2022-30160, is a remote code execution vulnerability that could be exploited by an attacker by sending malicious request to an affected system.
References:
CERT Coordination Center: Call for Coordinated Disclosure of Vulnerabilities in Microsoft Windows
https://www.cert.org/blogs/2018/03/09/call-for-coordinated-disclosure-of-vulnerabilities-in-microsoft-windows
Microsoft Security Advisory CVE-2022-30160
https://portal.msrc.microsoft.com/en-US/security-advisories/advisory?oid=CVE%2f2022%2f30160
Microsoft Windows Software Update Detection Failed!
The Microsoft Windows Update service has failed to detect the updates required for your computer.
CVE-2022: Microsoft Windows Remote Code Execution Vulnerability
This is a remote code execution vulnerability. A remote attacker could exploit this vulnerability by sending malicious request to an affected system.
The Microsoft Windows operating system supports the elevation of privilege for a process by using a Windows Advanced Local Procedure Call (ALPC).
ALPC is a Windows API that supports the launching of programs at a specified location in the operating system. It is often used for authentication, logging, and other administrative tasks.
ALPC provides a restricted set of functions that can be used by a process to perform administrative tasks. For example, a web server process in Windows can use ALPC to authenticate users and perform other administrative tasks.
It is possible for an attacker to exploit ALPC to elevate privileges and perform administrative tasks. An attacker can send malicious request to an affected system and exploit this vulnerability to run arbitrary code in the context of the affected system.
Credit where it’s due
We at Microsoft have been working on a fix for this vulnerability with our partners.
We have completed and distributed the update to all customers who use Windows with the latest automatic updates enabled. We recommend installing the updates immediately.
The patch should be installed automatically within 48 hours of release, but if you do not see the update yet, it will install automatically once available.
Timeline
Published on: 06/15/2022 22:15:00 UTC
Last modified on: 06/25/2022 03:24:00 UTC