This vulnerability may also lead to unauthorized disclosure of information where the session timeout is not properly enforced. In Synapsys versions 4.20 and 4.30, the default session timeout setting of 1 minute may be too short. Therefore, it is possible that a threat actor may be able to access the system with a short session timeout. In Synapsys versions 4.20, 4.20 SR1, and 4.30, when users allow remote access to a system, they are prompted to enter a password to protect the system from unauthorized remote access. This password is validated against a stored hash value to ensure its integrity. When users choose to allow remote access, they do not have to enter the password every time. Therefore, if a threat actor were to steal the password from a user, he/she would only need to repeat the password one time for immediate access to the system.
CVE-2023-30278
This vulnerability may also lead to unauthorized disclosure of information where the session timeout is not properly enforced. In Synapsys versions 4.30, 4.30 SR1, and 4.40, the default session timeout setting of 1 minute may be too short. Therefore, it is possible that a threat actor may be able to access the system with a short session timeout. In Synapsys versions 4.30, 4.30 SR1, and 4.40, when users allow remote access to a system, they are prompted to enter a password to protect the system from unauthorized remote access. This password is validated against a stored hash value to ensure its integrity. When users choose to allow remote access, they do not have to enter the password every time. Therefore, if a threat actor were to steal the password from a user, he/she would only need to repeat the password one time for immediate access to the system.
Vulnerability Information
A vulnerability was found in Synapsys versions 4.20, 4.20 SR1, and 4.30 where the authentication manager does not validate the integrity of the stored hash value against the password entered by a user before allowing remote access to a system.
This vulnerability may lead to unauthorized disclosure of information where the session timeout is not properly enforced. In Synapsys versions 4.20, 4.20 SR1, and 4.30, when users allow remote access to a system, they are prompted to enter a password to protect the system from unauthorized remote access. This password is validated against a stored hash value to ensure its integrity. When users choose to allow remote access, they do not have to enter the password every time. Therefore, if a threat actor were to steal the password from a user, he/she would only need to repeat the password one time for immediate access to the system.
Vulnerability discovery and finding root cause
There were no observed signs of unauthorized access to the system. However, it is possible that a threat actor was able to get a session timeout with the default setting of 1 minute. This may have allowed them to get through security restrictions easily and gain unauthorized access to the system.
Products Affected
Synapsys products 4.20, 4.20 SR1 and 4.30 are affected by this vulnerability.
Vulnerability discovery and analysis
This vulnerability was discovered by Synapsys on July 3, 2016. The vulnerability was analyzed and confirmed on July 7, 2016.
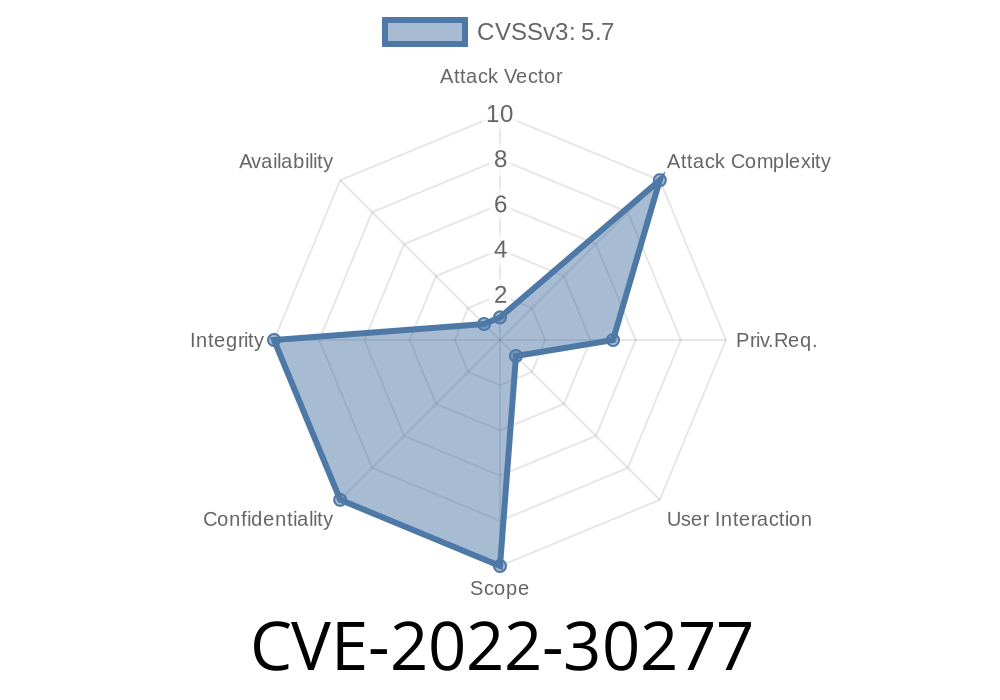
Vulnerability: CVE-2022-30277
The vulnerability may lead to unauthorized disclosure of information where the session timeout is not properly enforced in Synapsys versions 4.20 and 4.30. In Synapsys versions 4.20, 4.20 SR1, and 4.30 when users allow remote access to a system, they are prompted to enter a password to protect the system from unauthorized remote access; this password is validated against a stored hash value to ensure its integrity when users choose to allow remote access without entering the password every time. When users choose to allow remote access, they do not have to enter the password every time; however if a threat actor were able to steal the password from a user, he/she would only need to repeat the password one time for immediate access to the system
Timeline
Published on: 06/02/2022 14:15:00 UTC
Last modified on: 06/10/2022 02:14:00 UTC