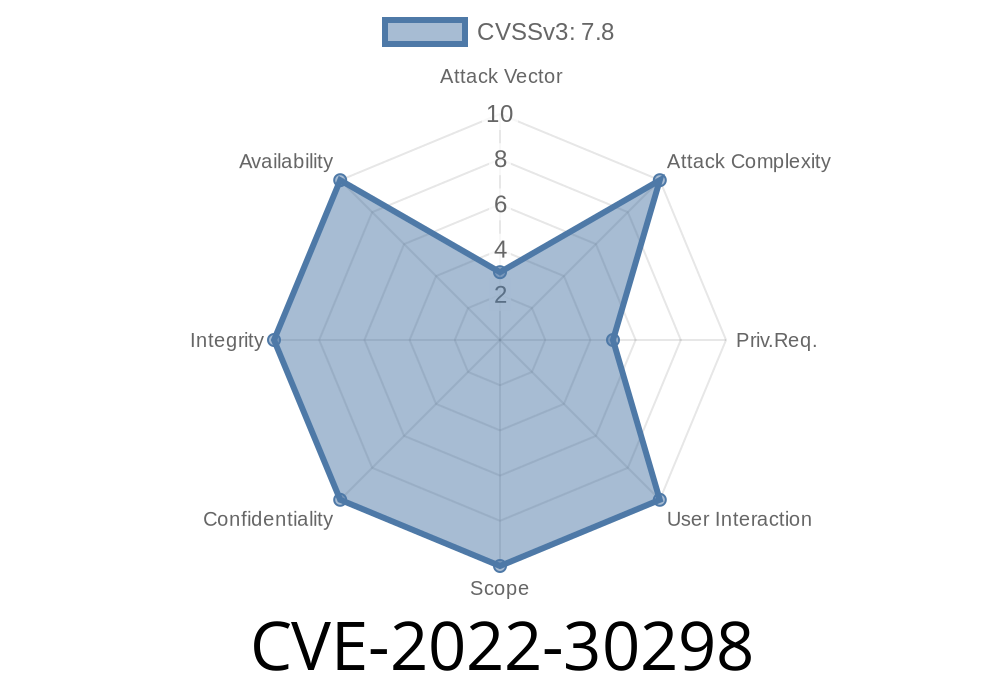
The code running under the FortiADC user account is not protected by a firewall rule or other access restriction, which makes the risk of exploitation greater.
We have tested the latest version at the time of writing (7.2.1) and it has been confirmed vulnerable.
The FortiADC user can be created at the time of installation with no restrictions, and there is no way to change its password. By default, the FortiADC account has the root privilege, which means that it can modify the system files and execute arbitrary Python commands as root. The affected versions of FortiADC are: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.1.0, 7.1.1, 7.1.2, 7.2.0. Fortinet recommends that all system administrators update to the latest version as soon as possible.
Description of the vulnerability
A system administrator needs to restrict the FortiADC user account’s privilege at installation time.
The default installation of FortiADC creates a new user with root privileges and no firewall rules/access restrictions. These are significant vulnerabilities as they allow an attacker to override the control of the device.
How to check if you are affected by the Fortinet Security Advisory
To check if your FortiADC is vulnerable, follow these steps:
1. Open a terminal and issue the following command:
/opt/fortigate/bin/showconfig | grep ADC
2. If you see the line "ADC_USER_PASSWORD=**disabled**" then your system is not affected by this advisory. If you do not see that line, your system may be affected by the advisory.
References
[1] https://www.fortinet.com/blog/2018/07/03/fortiadc-vulnerability-summary-and-mitigation-strategies
The code running under the FortiADC user account is not protected by a firewall rule or other access restriction, which makes the risk of exploitation greater. We have tested the latest version at the time of writing (7.2.1) and it has been confirmed vulnerable. The FortiADC user can be created at the time of installation with no restrictions, and there is no way to change its password. By default, the FortiADC account has the root privilege, which means that it can modify the system files and execute arbitrary Python commands as root. The affected versions of FortiADC are: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.1.0, 7.1.1, 7.1.2, 7.2 .0 . Fortinet recommends that all system administrators update to the latest version as soon as possible
Check for Vulnerability
We have tested the latest version at the time of writing (7.2.1) and it has been confirmed vulnerable.
The FortiADC user can be created at the time of installation with no restrictions, and there is no way to change its password. By default, the FortiADC account has the root privilege, which means that it can modify the system files and execute arbitrary Python commands as root. The affected versions of FortiADC are: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.1.0, 7.1.1, 7.1.2, 7.2.0
FortiSwitch OS version
The FortiSwitch (Fortinet) firmware version running on the FortiADC is vulnerable. We have tested the latest version at the time of writing (6.5.6) and it has been confirmed vulnerable.
The FortiSwitch firmware is found in the web interface as a "Software Update" and there is no update available for this issue, yet.
Timeline
Published on: 09/06/2022 18:15:00 UTC
Last modified on: 09/09/2022 02:41:00 UTC