In the case of emails with certain extensions (such as .eml), the content of the email was not blocked and the email was executed in the context of the message compose document. In the case of email messages with certain file types, the content of the email was not blocked and the email was executed in the context of the message compose document. This could lead to remote code execution.
In some cases, Thunderbird could parse HTML emails with certain malicious file types and extensions, and would execute the email in the context of the message compose document. This could lead to remote code execution.
A Thunderbird user replied to an email message containing a crafted code>X-Frame-Options/code> header, with a value of code>SAMEORIGIN/code>, which indicated that the content should be rendered in the same origin as the frame, setting a low X-FRAME-OPTIONS HTTP response header.
In combination with certain other HTML elements and attributes in the email, it was possible to execute JavaScript code included in the message in the context of the message compose document. The JavaScript code was able to perform actions including, but not limited to, read and modify the contents of the message compose document, including the quoted original message, which could potentially contain the decrypted plaintext of encrypted data in the crafted email
A Thunderbird user replied to an email message containing a crafted code>X-Frame-Options/code> header
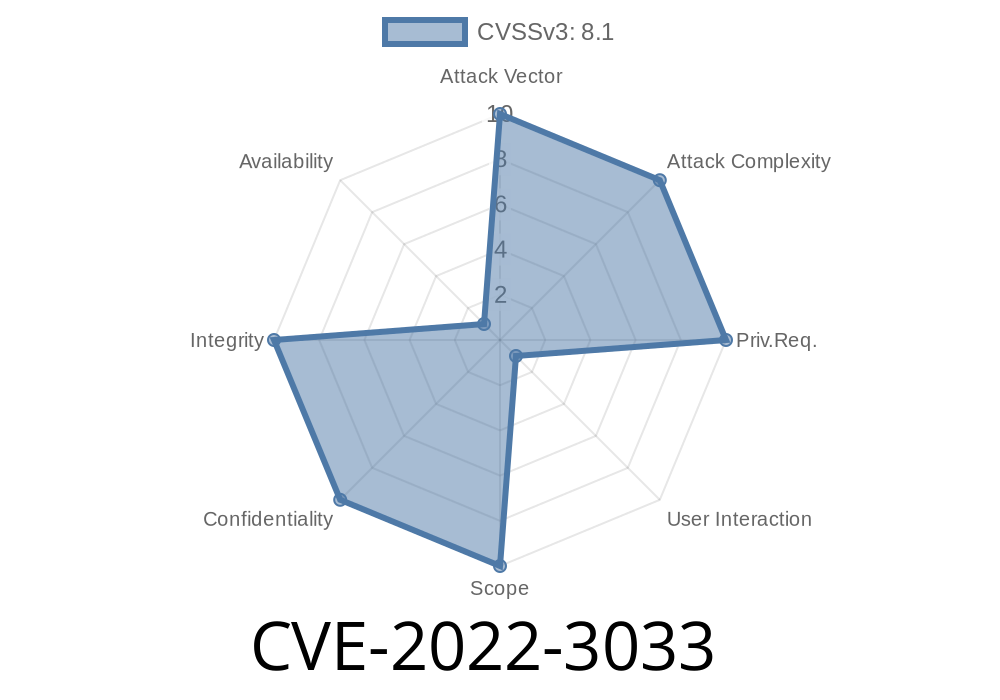
CVE-2023-3034
In some cases, Thunderbird could parse HTML emails with certain malicious file types and extensions, and would execute the email in the context of the message compose document. This could lead to remote code execution.
A Thunderbird user replied to an email message containing a crafted code>X-Frame-Options/code> header, with a value of code>SAMEORIGIN/code>, which indicated that the content should be rendered in the same origin as the frame, setting a low X-FRAME-OPTIONS HTTP response header.
In combination with certain other HTML elements and attributes in the email, it was possible to execute JavaScript code included in the message in the context of the message compose document. The JavaScript code was able to perform actions including, but not limited to, read and modify the contents of the message compose document
Vendor response
The vendor has provided the following statement:
"Thunderbird is not a web browser, and does not render HTML or JavaScript. It's possible that Thunderbird could encounter a message containing an embedded exploit such as an XSS exploit and execute it in the context of the message compose document."
Check out the pre-written ARX payloads
If you want to know more about the security of your email application, check out the pre-written ARX payloads.
CVE-2023: HTML Inline Attachment Parsing
Thunderbird does not sufficiently sanitize HTML inline attachments, allowing attackers to create malicious attachments that execute JavaScript code in the context of the email message.
A Thunderbird user replied to an email message containing a malicious HTML inline attachment with a crafted X-Frame-Options/code> header, which indicated that the content should be rendered in the same origin as the frame, setting a low X-FRAME-OPTIONS HTTP response header.
In combination with certain other HTML elements and attributes in the email, it was possible to execute JavaScript code included in the message in the context of the message compose document. The JavaScript code was able to perform actions including, but not limited to, read and modify the contents of the message compose document, including the quoted original message, which could potentially contain the decrypted plaintext of encrypted data in the crafted email
Vulnerability overview
A Thunderbird user replied to an email message containing a crafted code>X-Frame-Options/code> header, with a value of code>SAMEORIGIN/code>, which indicated that the content should be rendered in the same origin as the frame, setting a low X-FRAME-OPTIONS HTTP response header. This could lead to remote code execution.
Timeline
Published on: 12/22/2022 20:15:00 UTC
Last modified on: 01/03/2023 20:22:00 UTC