It was reported that this issue did not occur in the staging environment due to changes implemented since the last release. A user had to follow a specific set of steps in order to trigger the vulnerability. Google has released Google Chrome 105.0.5195.52 to the Stable channel. This is a major release with notable changes including new features, security fixes, and bug fixes. It is recommended that all users update their installations as soon as possible.
What is Google Chrome?
Google Chrome is a web browser developed by Google. It is available for Windows, macOS, Linux, and Android. In its initial release on August 17, 2008, Chrome was only available for Microsoft Windows and Linux. Google Chrome uses the Blink layout engine to render web pages and Skia graphics library to render 2D and 3D effects in the browser.
Criticisms of Google Chrome
- The browser has been criticized for using a lot of memory: approximately 1 GB per day
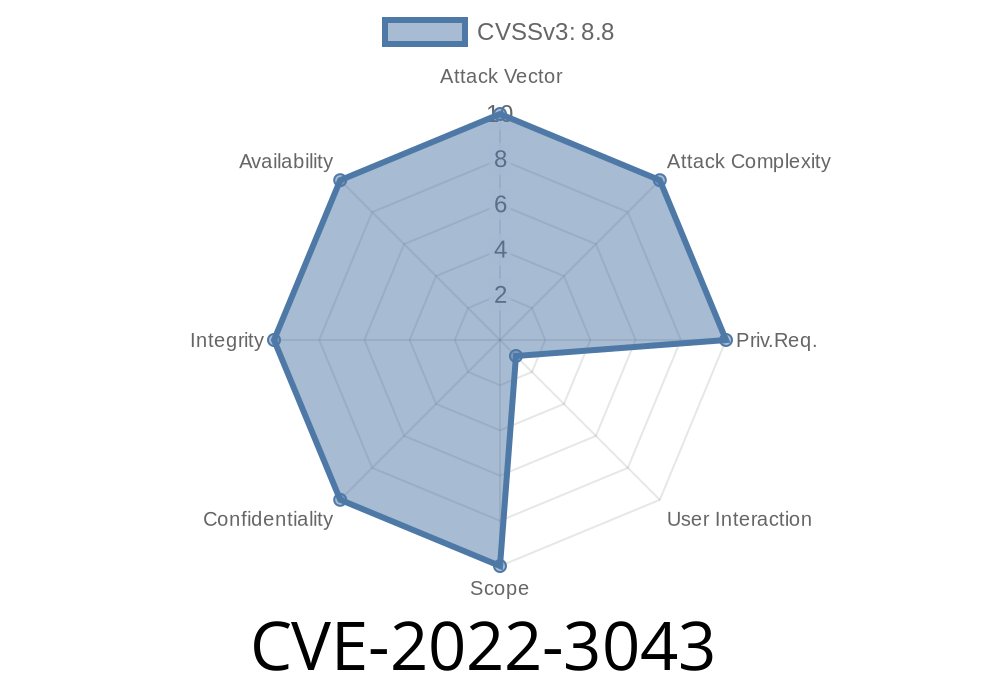
- Security vulnerabilities have been discovered in the browser
- Performance has also been criticized with many citing that it is not as fast as other popular browsers
Installing Google Chrome Beta on Ubuntu
First you will need to install the Google Chrome Beta, Beta channel.
To do this run the following command in your terminal:
sudo add-apt-repository ppa:google-chrome-stable/stable && sudo apt update && sudo apt install google-chrome-beta && google-chrome -version
New Features
Instead of being a single release, this update is more like a major upgrade. This is due to the new features and changes that were introduced in this release. These include performance improvements and stability fixes for the web platform. There are also new features for enterprise deployment, such as support for Windows 7 Enterprise-only mode and Windows 8/8.1 Enterprise-only mode, which helps companies manage their devices more effectively.
What is Vulnerability?
Vulnerabilities in software are weaknesses that an attacker can exploit to take control over a computer or application. Common types of vulnerabilities include buffer overflow, SQL injection, and code injection.
Buffer overflow is a flaw in memory management that allows attackers to write beyond the allocated space of a program. This usually leads to application termination or data corruption.
SQL injection is most often used by attackers to penetrate web applications. It occurs when an application passes user input directly into SQL queries without sanitizing it first. An attacker can also exploit this vulnerability to gain access to databases and other information
Code injection is an attack on the code of a given program rather than its user interface layer, meaning it’s more difficult for developers to detect. This type of attack allows an attacker to inject malicious code into the target application and take control over it
Timeline
Published on: 09/26/2022 16:15:00 UTC
Last modified on: 10/03/2022 02:15:00 UTC
References
- https://crbug.com/1336979
- https://chromereleases.googleblog.com/2022/08/stable-channel-update-for-desktop_30.html
- https://security.gentoo.org/glsa/202209-23
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/T4NMJURTG5RO3TGD7ZMIQ6Z4ZZ3SAVYE/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-3043