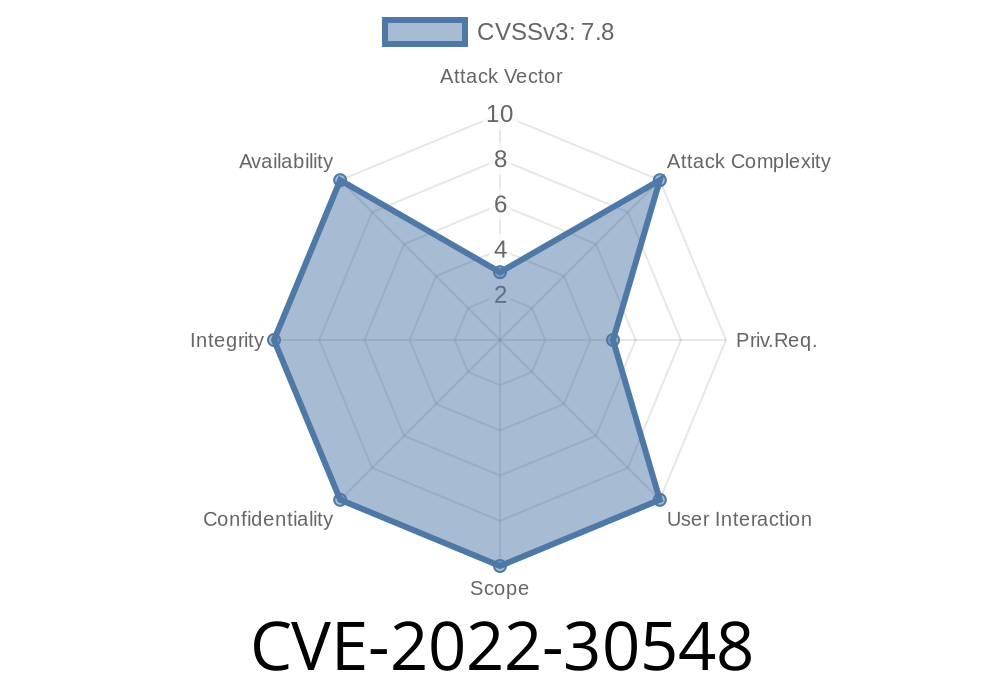
This issue may occur due to the presence of a directory traversal sequence in the Intel(R) Glorp software that allows an authenticated user to potentially enable escalation of privilege via local access. This issue has been rated as Critical due to the potential for an attacker to gain elevated privileges if an authenticated user installs a malicious component that is accessible via local access. --------------------------- This CVE is related to: Solution vendors have acknowledged this issue and provided fixes. We recommend installing the latest software updates. --------------------------- Uncontrolled search path elements can lead to a variety of security issues, including information disclosure, injection, redundancy, and logic issues. An uncontrolled search path can result from a variety of design decisions made during the software development lifecycle. A common example of an uncontrolled search path is a default value for a controlled variable that is too large. For example, a default value of the number of characters in a password would be considered an uncontrolled search path. Other examples of uncontrolled search paths include an element that is not initialized, a value that is out of range, or a value that is directly controlled by an attacker. Uncontrolled search path issues can lead to software vulnerabilities, data integrity issues, and other issues.
Overview
This advisory is related to CVE-2022-30548. It does not impact Intel(R) Glorp software, but it may result from the presence of an uncontrolled search path in the Intel(R) Glorp software that could allow elevation of privilege via local access.
Vulnerability overview
CVE-2022-30548 is a vulnerability that can be leveraged by attackers. This vulnerability allows an attacker to potentially gain elevated privileges if an authenticated user installs a malicious component that is accessible via local access. This issue has been rated as Critical due to the potential for an attacker to gain elevated privileges if an authenticated user installs a malicious component that is accessible via local access.
Timeline
Published on: 11/11/2022 16:15:00 UTC
Last modified on: 11/17/2022 15:07:00 UTC