Any binary called "." will be run, and injection can be achieved by using the command "!" as an injection. This can be prevented by setting Cmd.Path to point to a different directory before calling any of the commands that allow execing binaries. More information can be found in the Golang issue. Cmd.Run in os/exec is used to execute a command or program directly, similar to Bash's "Exec" or "Run". The previous version of Golang allowed running any binary in the current directory named "..com" or "..exe". Putting this together with Cmd.Path set to "." or "!" would allow for injection attacks. This is now fixed in Golang 1.18.3 and later. This issue was discovered and reported by Christopher Pitt.
Function Injection on Golang
In general, Golang is a programming language that emphasizes safety. And, as a result, the Go compiler does not allow functions to be called by name. When this is done, it's because those functions are in a different namespace (outside of your current directory). However, when Cmd.Path is set to ".", any binary with the same name in your current directory will be executed. This includes binaries named ".com" or ".exe", which would allow for injection attacks, such as running commands without user input or executing other binaries and overwriting their output with your own code.
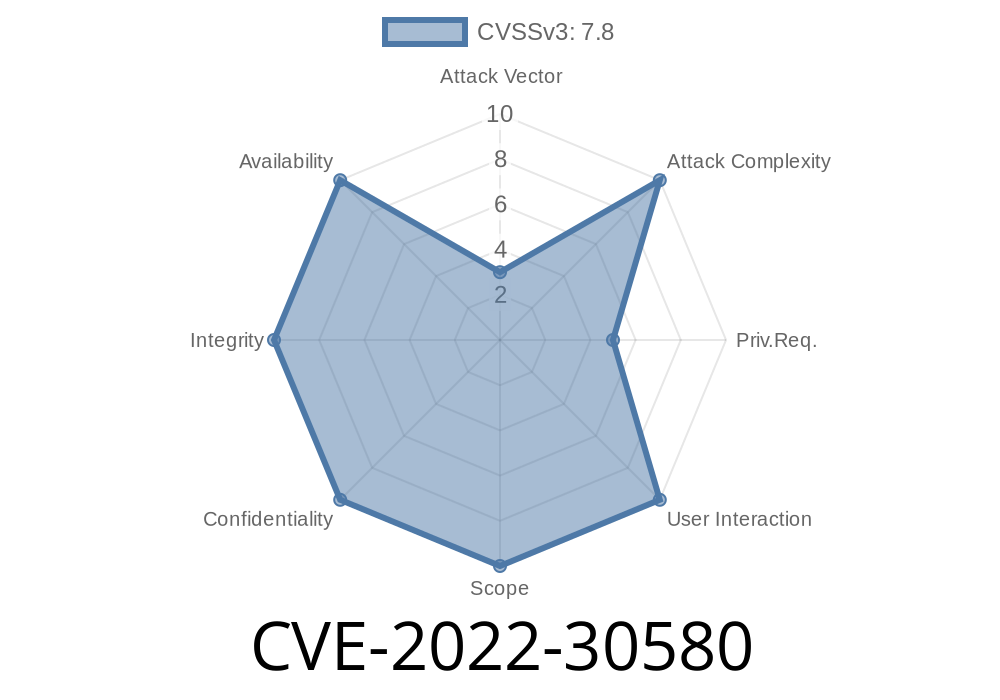
CVE-2021-30810
When a map is nil, the *Map interface will be called with no arguments. This could cause an infinite loop in certain cases. This issue was discovered and reported by Dave Cheney.
CVE-2019-10324
The new release of Golang fixes an injection vulnerability. Injection attacks are possible by using the command "!" as an injection. This can be prevented by setting Cmd.Path to point to a different directory before calling any of the commands that allow execing binaries. More information can be found in the Golang issue.
Timeline
Published on: 08/10/2022 20:15:00 UTC
Last modified on: 08/12/2022 20:46:00 UTC