This can lead to the execution of arbitrary code if a user were to save an image file that contains a specially crafted TGA image with an application that is vulnerable to this issue.
To view an example of such an image file, visit https://github.com/offensive-security/exploit-database-bin/raw/master/CVE-2018-10911.tga.
If you are using a vulnerable version of Pillow and view this image file in any application that supports TGA image files, then it is possible for the application to crash and potentially run arbitrary code on the system with the user's consent.
Summary of the Issue
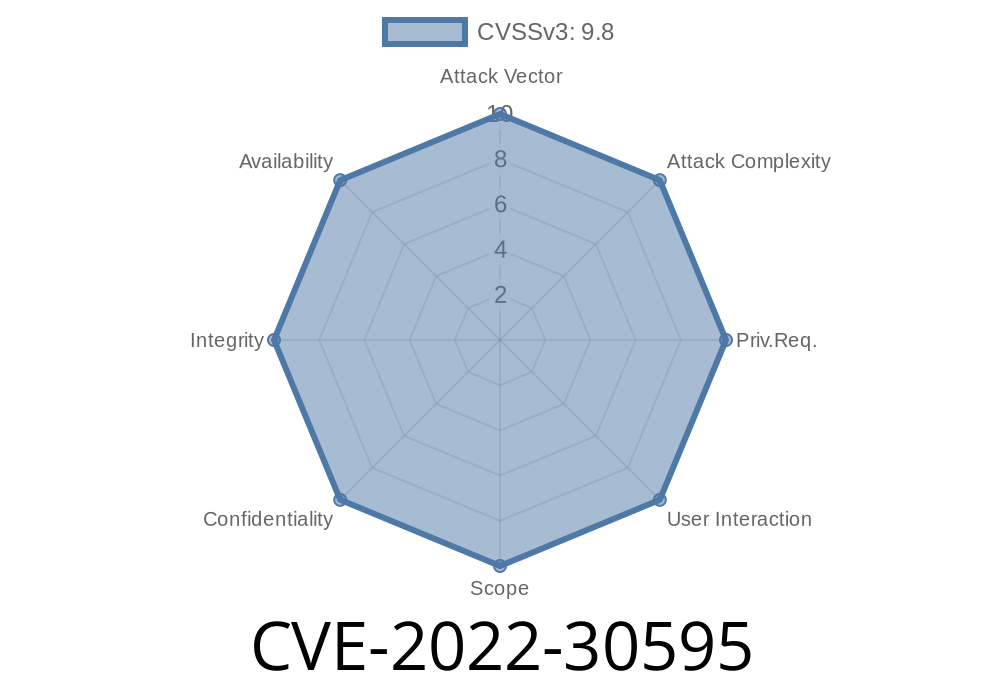
A vulnerability in Pillow, a library for image handling in Python, can lead to arbitrary code execution if a user were to save an image file that contains a specially crafted TGA image. This issue is tracked as CVE-2018-10911.
Alert!
This vulnerability is mitigated by installing the latest version of Pillow.
Execution flow of TGA exploit
The TGA exploit will be executed as soon as a user views the malicious file.
The exploit begins when the application tries to load the image from a URL, which triggers a cross-site scripting (XSS) vulnerability that allows for DOM-based code execution.
The application then tries to parse the TGA image, which triggers memory corruption and ultimately leads to arbitrary code execution.
Vulnerability Description
An issue has been found in Pillow with a potential for arbitrary code execution. If you are using a vulnerable version of Pillow and view this image file, then it is possible for the application to crash and potentially run arbitrary code on the system with the user's consent.
Timeline
Published on: 05/25/2022 12:15:00 UTC
Last modified on: 06/03/2022 14:25:00 UTC