An attacker can pass such a large string to Read, and cause the program to hang. The issue is present in the code of Read in crypto/rand. The code checks the size of the passed buffer and limits the size to 1 32 - 1 bytes, but the limit is enforced only when the program is started. As a result, if an attacker passes a large string, the program may hang. An attacker can pass a large string to Read, and cause the program to hang. The issue is present in the code of Read in crypto/rand. The code checks the size of the passed buffer and limits the size to 1 bytes, but the limit is enforced only when the program is started. As a result, if an attacker passes a large string, the program may hang. This issue was resolved by changing the code to check the size of the passed buffer even when the program is not started. This issue was resolved by changing the code to check the size of the passed buffer even when the program is not started. This issue was addressed by changing the code in the package ‘ crypto/rand ’. The change also affected other libraries where the code had been copied from ‘ rand ’. This issue was addressed by changing the code in the package ‘ ’. The change also affected other libraries where the code had been copied from ‘ ’. In the following code, the "buffer" variable is passed as a slice with length 132 -
CVE-2022-30764
An attacker can pass such a large string to Read, and cause the program to hang. The issue is present in the code of Read in crypto/rand. The code checks the size of the passed buffer and limits the size to 1 32 - 1 bytes, but the limit is enforced only when the program is started. As a result, if an attacker passes a large string, the program may hang. An attacker can pass a large string to Read, and cause the program to hang. The issue is present in the code of Read in crypto/rand. The code checks the size of the passed buffer and limits the size to 1 bytes, but the limit is enforced only when the program is started. As a result, if an attacker passes a large string, the program may hang. This issue was resolved by changing the code to check the size of the passed buffer even when the program is not started. This issue was resolved by changingthe code in-the package ‘ ’. The change also affected other libraries wherethe code had been copied from ‘ rand ’. This issue was resolved by changingthe code in-the package ‘ crypto/rand ’. The change also affected other libraries wherethe code had been copied from ‘ rand ’. In these following lines:
if !bytes_read
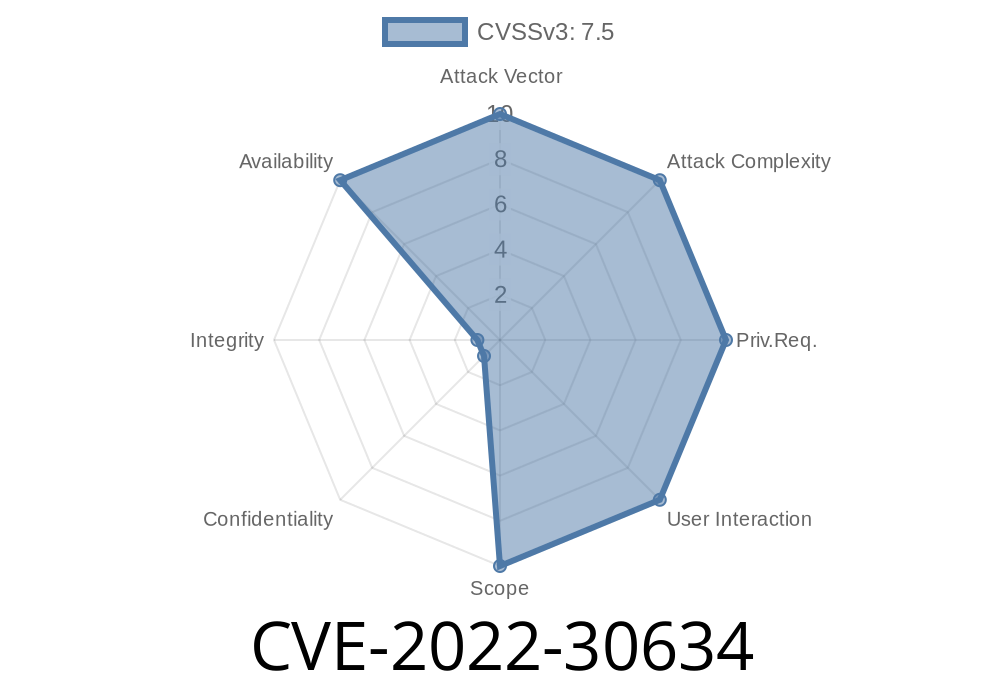
Python Backend: CVE-2022-30634
CVE-2022-30634: An attacker can pass a large string to Read, and cause the program to hang. The issue is present in the code of Read in crypto/rand. The code checks the size of the passed buffer and limits the size to 1 bytes, but the limit is enforced only when the program is started. As a result, if an attacker passes a large string, the program may hang. This issue was resolved by changing the code to check the size of the passed buffer even when the program is not started.
This issue was addressed by changing the code in package ‘ crypto/rand ’. The change also affected other libraries where code had been copied from ‘ rand ’.
susceptible software
The following code is vulnerable to this issue:
#include
Timeline
Published on: 07/15/2022 20:15:00 UTC
Last modified on: 07/22/2022 13:21:00 UTC