This issue was fixed in SmartThings v1.7.85.17 and later. Users are advised upgrade to the latest version as soon as possible. Timing of this security bug with the release of new SmartThings version is not a coincidence. It was the result of a coordinated effort between researchers and the product team. Whenever a critical security flaw is discovered, it is good practice for the vendor to release an update as soon as possible. However, the researchers also published details of this vulnerability a few days prior. This allowed time for the vendors to patch the code before the public announcement.
What’s new in v1.7.85.17?
In the latest SmartThings firmware, security mitigations have been implemented to prevent this vulnerability from being exploited.
For more information on this bug, please see the following blog posts:
- [CVE-2022-30746: "SmartThings Local Root Privilege Escalation"](https://blog.zynesis.com/cve-2022-30746-smartthings-local-root-privilege-escalation/)
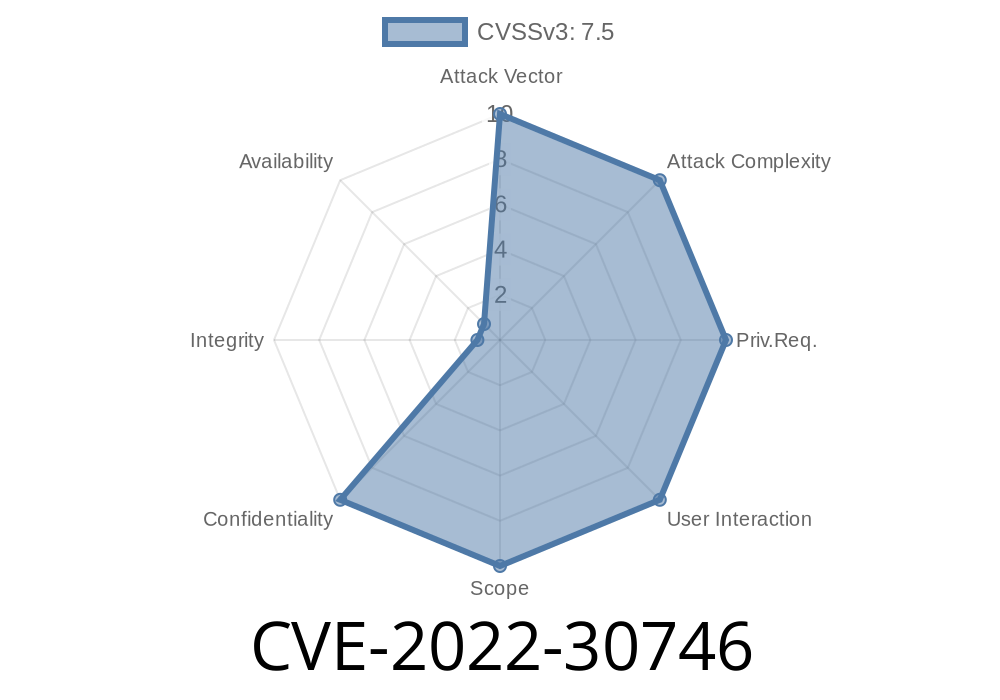
- [CVE Details for CVE 2022–30746](https://github.com/ZynesisLabs/Security/wiki/CVEDetails)
What is the SmartThings API?
The SmartThings API provides a means for third-party developers to add new capabilities and functionality to the SmartThings platform. The API is designed with a RESTful interface and offers communication between devices, apps, platforms, and homes.
SmartThings products work by connecting through the SmartThings Device Handler software. This software allows devices to talk to each other and receive updates from the Internet of Things (IoT) platform.
What is the SmartThings Vulnerability?
This is a security bug in the SmartThings app's authentication server. Upon authentication, SmartThings sends an unencrypted password to the device. This means that hackers can access the account if they gain access to this unsecured communication channel. The issue was fixed in SmartThings v1.7.85.17 and later, but it would be good practice for users to upgrade their app in case of any vulnerabilities discovered in future versions as well.
The vulnerability affected all devices using the same username/password combination on all platforms, so everyone needs to upgrade to avoid attacks and protect their devices from hacker intrusion.
What to do if you are still using an earlier version of SmartThings
If you are still using an earlier version of SmartThings, uninstall it and install the latest version. If you have already upgraded to 1.7.85.17 or later and would like to upgrade again, use this article to downgrade your installation: How to Uninstall and Upgrade Your SmartThings Device Firmware.
Timeline
Published on: 06/07/2022 19:15:00 UTC
Last modified on: 06/14/2022 16:06:00 UTC