This can happen when the server doesn’t have the appropriate data to answer the query, or if the data is incorrect. DNS is a stateless service, so there’s no way for the server to know if the data is outdated before it’s received. While most servers are configured to filter out invalid queries, not all of them are configured to filter out all types of invalid queries. As a result, an attacker can send a malicious query to the server, causing it to crash. A common example of this type of attack is an attacker querying the server for “ www.example.com ”, with a query that attempts to crash named.
DNS DoS Via Recursive Query
A malicious application can send a recursive query to the DNS server, causing it to crash. This is a type of DoS attack that's known as a "recursive query."
For example, an attacker could start with a single request for www.example.com, but could add more and more values to the request until the server is full and cannot process any more requests.
This may also be done in combination with other attacks such as TCP SYN Flooding or ICMP Flooding.
What’s wrong with the following request?
What's wrong with the following request?
www.example.com gooby
The server doesn't have the appropriate data to answer this query.
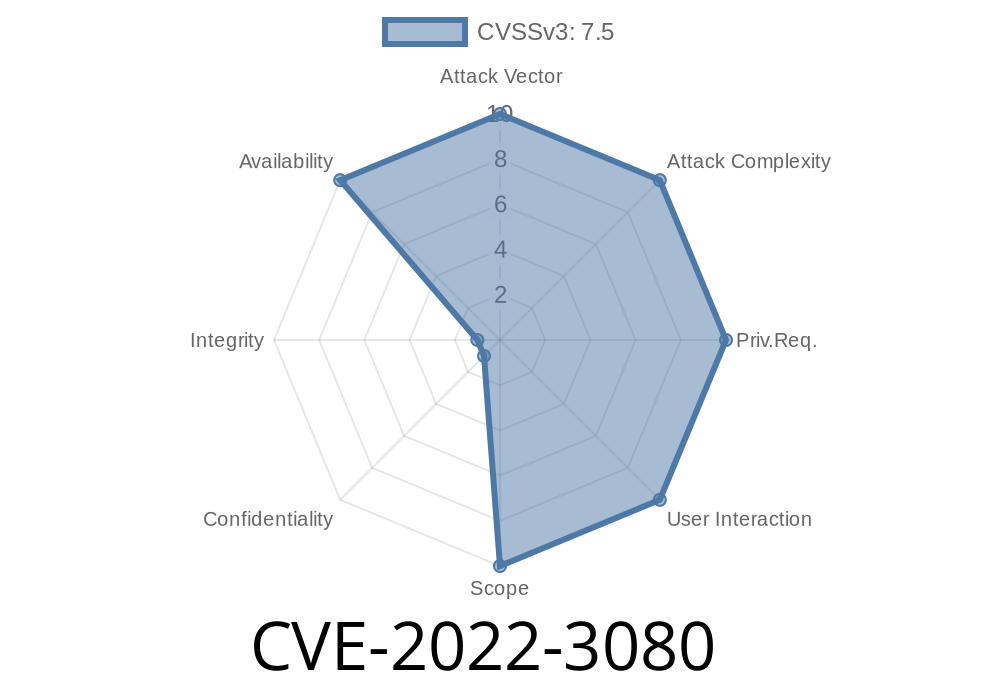
DNS Protocol Vulnerabilities
DNS is not designed to be a secure protocol. The DNS protocol was originally designed in a different time and place, and as such doesn’t have the necessary security. This means that there are some vulnerabilities installed that allow attackers to send queries to the server with malicious intent.
The most common vulnerability of the DNS protocol is an attacker querying the server for “ www.example.com ”, with a query that attempts to crash named . Another example of this type of attack is an attacker querying the server for “ www.example.com/a ” and receiving an answer back from it when querying for “ www.example.com/b ”
DNS zone transfer DoS :
A denial-of-service attack can be performed by sending a DNS query to the server containing a malicious request, such as sending a large number of queries per second that are designed to slow down the server. This type of attack is known as a zone transfer denial-of-service (DNS DoS) attack.
If the server receives an invalid response from the DNS service, it will respond with an error code. The attacker can then attempt to guess these codes and send requests for any domain name that has an error code in its response. If the attacker guesses right, they can hijack the domain name and host whatever they want there; this is known as a reflection or amplification attack. This often results in hackers being able to take control of servers on the network by manipulating their IP addresses during this process.
To prevent this type of attack, you should make sure your DNS servers are configured only to respond to valid queries and filter out invalid ones before they reach your servers.
DNA poisoning
DNA poisoning is a type of DDoS attack in which the attacker sends a malicious query to the server that is designed to crash the server.
Timeline
Published on: 09/21/2022 11:15:00 UTC
Last modified on: 09/27/2022 23:15:00 UTC
References
- https://kb.isc.org/docs/cve-2022-3080
- http://www.openwall.com/lists/oss-security/2022/09/21/3
- https://www.debian.org/security/2022/dsa-5235
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/CV4GQWBPF7Y52J2FA24U6UMHQAOXZEF7/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/MRHB6J4Z7BKH4HPEKG5D35QGRD6ANNMT/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-3080