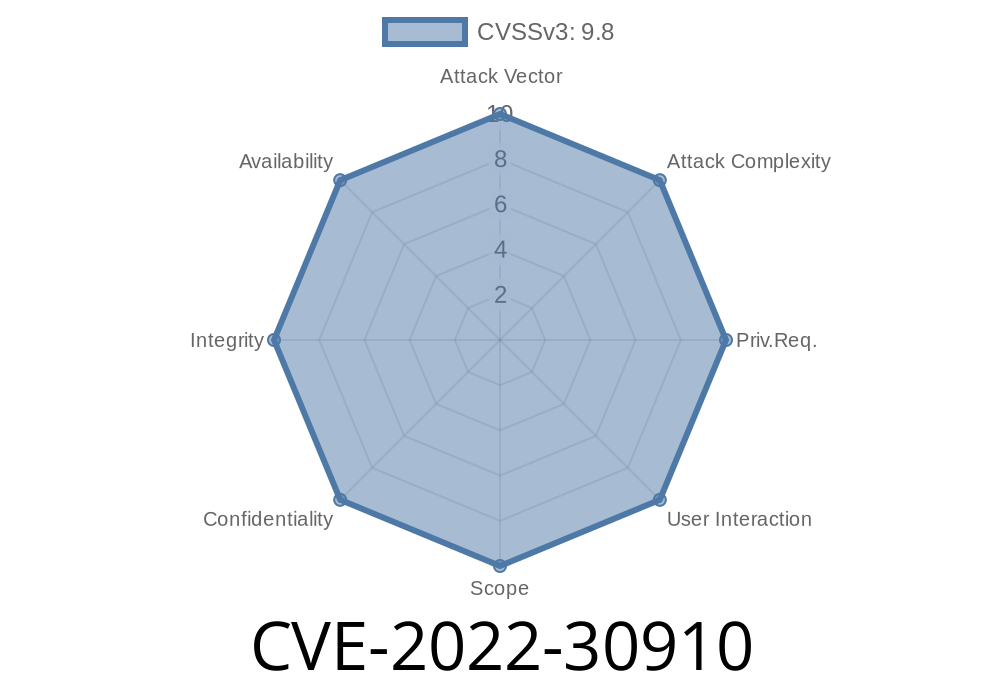
The researcher discovered that the GO parameter was not properly sanitized, allowing an attacker to execute a stack buffer overflow and execute arbitrary code on the victim’s system. The researcher reported this vulnerability to Cisco. Cisco confirmed the vulnerability and released a patch. End users should be strict about following vulnerability management procedures, such as updating software and using strong passwords.
Cisco DPEs are advised to consider the following when applying the patch: — Restrict access to the interface where the vulnerable module is installed. — Restrict access to the vulnerable module by logging into the device and disabling access for the vulnerable module. — Restrict access to the vulnerable module by using a password. — Restrict access to the vulnerable module by using an access control list or by using a firewall. — Restrict access to the vulnerable module by using a role-based access control model. — Restrict access to the vulnerable module by using a least privilege model. — Restrict access to the vulnerable module by using a separation of duties model.
Cisco Security Tips for Vulnerability Management
Cisco DPEs should follow the following guidelines for vulnerability management procedures:
— Update the vulnerable module. — Restrict access to the vulnerable module by logging into the device and disabling access for the vulnerable module. — Restrict access to the vulnerable module by using a password or an access control list. — Restrict access to the vulnerable module by using a firewall or a role-based access control model. — Restrict access to the vulnerable module by using a least privilege model.
Cisco IOS Software and Cisco Services – Flaws and Vulnerabilities
Cisco IOS Software and Cisco Services contain security vulnerabilities that, if exploited by an attacker, could allow the attacker to take control of the affected system. These—flaws and vulnerabilities—are documented in a Security Vulnerability Note (SVN) or Security Vulnerability Alert (SVA). For more information on how to identify a SVA or SVN for Cisco IOS Software, see "Identifying Security Vulnerabilities in Cisco Systems." For more information on how to report flaws and vulnerabilities to Cisco, see "Reporting Flaws and Weaknesses in Cisco Systems."
Cisco IOS Software
Release 12.4(24)T
The Cisco IOS Software Release 12.4(24)T is the only available software release that addresses this vulnerability.
Timeline
Published on: 06/08/2022 14:15:00 UTC
Last modified on: 06/14/2022 22:30:00 UTC