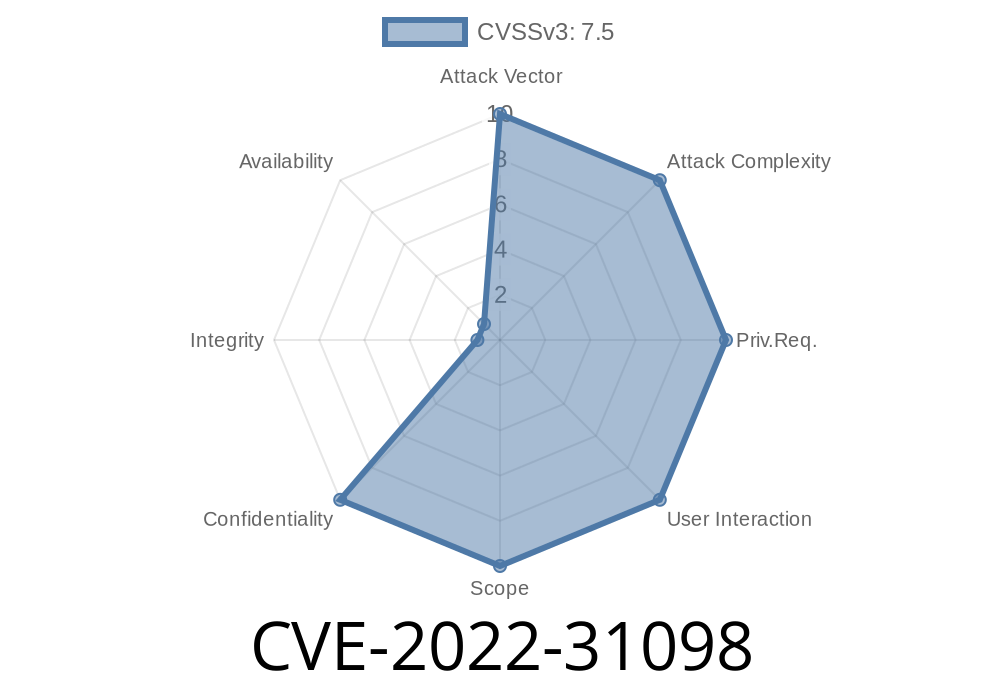
and their service account tokens. An attacker could then use these credentials to either view sensitive configurations of a cluster, for example, the KubeConfg, or start a pod of a Weave application. Depending on the potential impact of the vulnerability, the severity would be determined by the type and impact of the action taken by the attacker. An authenticated remote attacker could cause a denial of service (DoS) or potentially cause data exfiltration from the cluster, for example, by reading sensitive configurations from the KubeConfg, or start a pod on a Weave application. Furthermore, an attacker could also potentially exploit this vulnerability to start a pod of a Weave application. A remote attacker could potentially exploit this vulnerability to view sensitive configurations of a cluster, for example, the KubeConfg, or start a pod of a Weave application. An attacker could then use these credentials to either view sensitive configurations of a cluster, for example, the KubeConfg, or start a pod of a Weave application. Depending on the potential impact of the vulnerability, the severity would be determined by the type and impact of the action taken by the attacker. An authenticated remote attacker could cause a denial of service (DoS) or potentially cause data exfiltration from the cluster, for example, by reading sensitive configurations from the KubeConfg, or start a pod on a Weave application
Affected Pods Weave
Cluster: master-2
KubeConfig:
$ kubectl get configmap -n weave --all-namespaces | grep weave.master.name
weave.master.name=master-2
Timeline
Published on: 06/27/2022 22:15:00 UTC
Last modified on: 07/11/2022 13:54:00 UTC