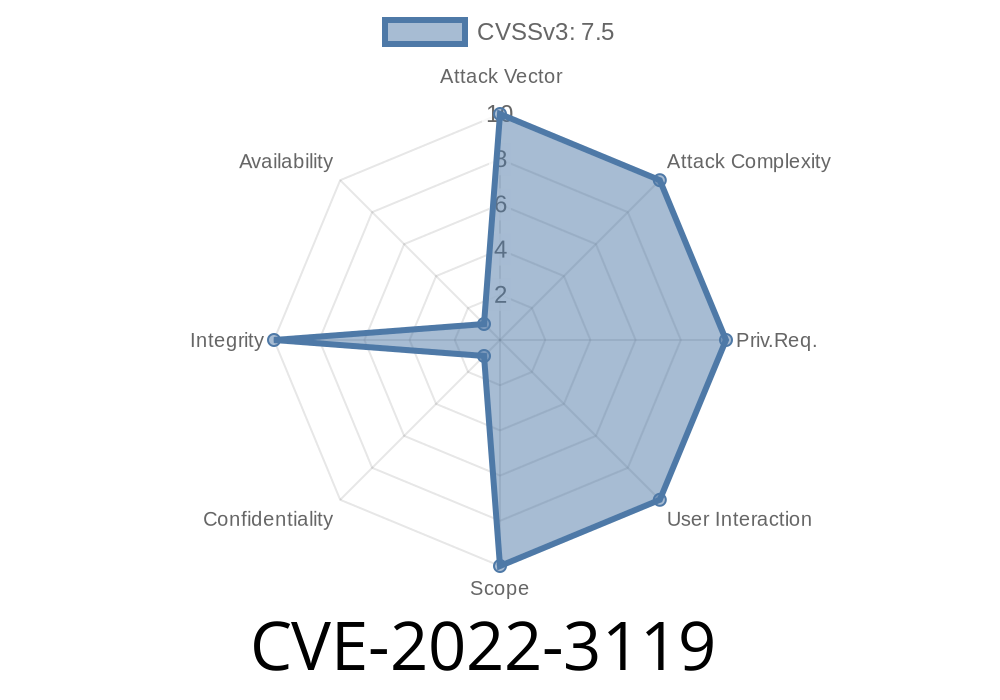
when updating its settings, which could allow unauthenticated attackers to update them and change the OAuth endpoints to ones they controls, allowing them to then be authenticated as admin if they know the correct email address Unauthenticated attackers could inject malicious code into the update process that would then be executed by the plugin if the update setting was enabled. This could lead to unauthorised plugin updates being downloaded and installed.
Unauthenticated attackers could also create malicious plugins that would be enabled by the plugin and then be approved by the plugin’s administrators.
Unauthenticated attackers could also create malicious plugins that would be enabled by the plugin and then be approved by the plugin’s administrators. Unauthorised attackers could create a new plugin that would use the plugin’s code but would then have different settings to the real plugin.
Unauthorised attackers could create a new plugin that would use the plugin’s code but would then have different settings to the real plugin. Unauthorised attackers could create a new plugin that would have the same name as the real plugin and then have different settings.
Unauthorised attackers could create a new plugin that would have the same name as the real plugin and then have different settings. Unauthenticated attackers could create a new plugin that would have the same name as the real plugin and then have different settings.
Mitigation Strategies
A thorough review of the issue would be required to identify possible alternative solutions.
A thorough review of the issue would be required to identify possible alternative solutions. A thorough review of the issue would be required to identify possible alternative solutions
Recommendation:
A solution to this vulnerability is to restrict the plugin’s admin functionality to only those who have been given permission to use it.
A solution to this vulnerability is to restrict the plugin’s admin functionality to only those who have been given permission to use it.
What does Jenkins plugin security look like?
Jenkins plugin security looks like the following:
-Authenticated attackers could create a new plugin that would have the same name as the real plugin and then have different settings.
-Unauthenticated attackers could create a new plugin that would have the same name as the real plugin and then have different settings.
-Unauthenticated attackers could create a new plugin that would have the same name as the real plugin and then have different settings.
-Unauthenticated attackers could create a new plugin that would use the plugin’s code but would then have different settings to the real plugin.
-Unauthenticated attackers could inject malicious code into the update process that would then be executed by the plugin if the update setting was enabled. This could lead to unauthorised plugin updates being downloaded and installed.
How do I know if my site is vulnerable?
If your site is vulnerable, a security notification will be emailed to you.
How do I find out if my site is vulnerable?
To check to see if your site is vulnerable, click the "Check if you are vulnerable" button on our website. If all of the settings are not configured, it will display a green message saying that you are not vulnerable. If any one of the settings is configured as malicious, it will display a red message saying that you are vulnerable and need to fix the security issue by changing the settings back to their original values.
Timeline
Published on: 09/26/2022 13:15:00 UTC
Last modified on: 09/28/2022 16:28:00 UTC