The Netwrix Auditor remote code execution vulnerabilities can be exploited via the following vectors:
1. Remotely via a Web request to a vulnerable system, using a specially crafted URL.
2. Remotely via a file upload to a vulnerable system, using a specially crafted file.
3. Remotely via a Telnet connection to a vulnerable system, using a specially crafted command.
4. Remotely via a VNC connection to a vulnerable system, using a specially crafted password.
5. Remotely via a SSH connection to a vulnerable system, using a specially crafted command.
6. Remotely via a console connection to a vulnerable system, using a specially crafted command.
7. Remotely via a direct connection to a vulnerable system, using a specially crafted command.
8. Remotely via a Netwrix Auditor export/import functionality, using a specially crafted file.
9. Remotely via a Netwrix Auditor export/import functionality, using a specially crafted URL.
10. Remotely via a Netwrix Auditor export/import functionality, using a specially crafted file.
11. Remotely via a Netwrix Auditor export/import functionality, using a specially crafted Telnet/VNC password.
12. Remotely via a Netwrix Auditor export/import functionality, using a specially crafted SSH password.
13. Remotely via a Netwrix Auditor export
Remote code execution vulnerability details
1. Remotely via a Web request to a vulnerable system, using a specially crafted URL.
The vulnerability exists when the user is running an application that uses Netwrix Auditor’s AuditFilter.exe that has been uploaded to the remote system. An attacker could exploit this by providing a specially crafted URL that leads to the file upload interface of an application running on the remote system and sending a malformed XML document containing malicious code. This will cause the application to attempt execution of this code instead of performing its intended function.
2. Remotely via a file upload to a vulnerable system, using a specially crafted file.
The vulnerability occurs when the user is running one of these applications: Netwrix Auditor for SharePoint, Netwrix Auditor for Novell GroupWise, Netwrix Auditor for Exchange, or Netwrix Auditor for Microsoft SQL Server and sends a malformed XML document containing malicious code. This will cause the application to attempt execution of this code instead of performing its intended function.
3. Remotely via a Telnet connection to a vulnerable system, using a specially crafted command.
The vulnerability occurs when the user runs an application that uses Telnet filter in conjunction with Netwrix Auditor and sends it as input data in any form (by utilizing any command). This will cause the input data to be executed as authentication credentials instead of being passed through as part of standard communication traffic between client and server components during Telnet session establishment
Vulnerability details
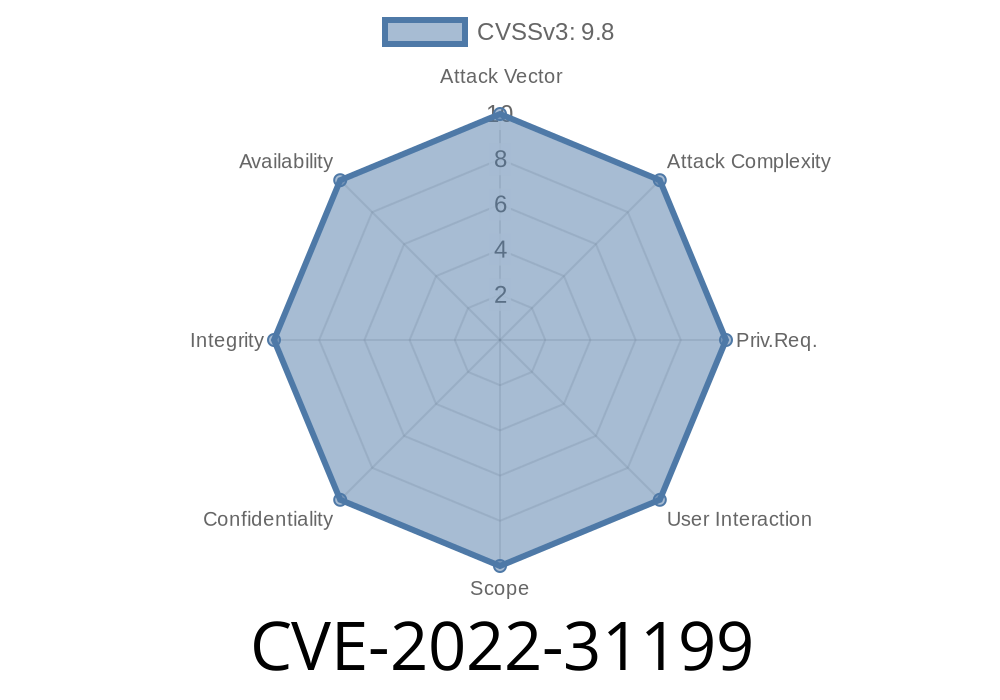
CVE-2022-31199 - Netwrix Auditor Remote Code Execution Vulnerabilities
The Netwrix Auditor remote code execution vulnerabilities can be exploited via the following vectors:
1. Remotely via a Web request to a vulnerable system, using a specially crafted URL.
2. Remotely via a file upload to a vulnerable system, using a specially crafted file.
3. Remotely via a Telnet connection to a vulnerable system, using a specially crafted command.
4. Remotely via a VNC connection to a vulnerable system, using a specially crafted password.
5. Remotely via a SSH connection to a vulnerable system, using a specially crafted command.
6. Remotely via a console connection to a vulnerable system, using a specially crafted command.
7. Remotely via a direct connection to an infected system, using the same method as in #6 above (direct connection).
8. Remotely via Netwrix Auditor export/import functionality, using an encrypted data file or URL that doesn't include the string "password" in its pathname (e.g., https://analysis-server/exportLogin?username=
Notable features of Netwrix Auditor
- Netwrix Auditor's comprehensive monitoring and reporting capabilities provide visibility into the health of your infrastructure.
- Netwrix Auditor's built-in auditing capabilities help ensure compliance with PCI DSS, HIPAA, SOX, and other regulatory mandates.
- Netwrix Auditor integrates with a variety of third-party products to offer a seamless enterprise solution.
How Could an attacker exploit the vulnerability?
The attacker can exploit the vulnerability by:
1. Sending a specially crafted URL to the victim, which will execute code on the vulnerable system and will download a malicious file that when run, will execute code remotely.
2. Sending a specially crafted file to the victim, which when run, will execute code remotely.
3. Sending a specially crafted Telnet/VNC password to the victim, which when executed locally on the vulnerable system, executes code remotely.
4. Sending a specially crafted SSH password to the victim, which when executed locally on the vulnerable system, executes code remotely.
5. Sending a specially crafted command to the victim’s console connection that will allow for remote execution of code on their machine and then executing said commands via their console connection.
6-7. Sending a specially crafted command to either Telnet or SSH that will allow for remote execution of code on their machine and then executing said commands via their SSH or Telnet connection respectively
8-9-10-11-12-13. Any method an attacker might use in order for them to exploit these vulnerabilities
CVE-2022-31199 - Netwrix Auditor Remote Code Execution Vulnerability
The Netwrix Auditor remote code execution vulnerabilities can be exploited via the following vectors:
1. Remotely via a Web request to a vulnerable system, using a specially crafted URL.
2. Remotely via a file upload to a vulnerable system, using a specially crafted file.
3. Remotely via a Telnet connection to a vulnerable system, using a specially crafted command.
4. Remotely via a VNC connection to a vulnerable system, using a specially crafted password.
5. Remotely via a SSH connection to a vulnerable system, using a specially crafted command.
6. Remotely via console connection to a vulnerable system, using specially crafted commands and commands that are not logged on the server's console window in the case of SSH or Telnet traffic; 7. Remotely from an attacker on the same LAN or WAN interface as the server used by Netwrix Auditor running as Administrator with credentials supplied by the attacker; 8. Remotely from an attacker on an external network that is directly connected to the server running Netwrix Auditor; 9-12 are related to export/import functionality within Netwrix Auditor that is prone to malicious command injection and contains hardcoded credentials which may allow for remote access; 13 is related to exporting data from Netwrix Auditor which also has hardcoded credentials which may allow for remote access
Timeline
Published on: 11/08/2022 01:15:00 UTC
Last modified on: 11/09/2022 19:33:00 UTC