It has been discovered that the software is vulnerable to SQL injection. By manipulating certain parameters, an attacker may obtain sensitive information or execute arbitrary code. The problem appears in the medicine_details.php script. By changing the value of the argument ‘ medicine ’, an attacker may inject and execute arbitrary sql code. The vulnerability allows an attacker to inject malicious sql code via the following route: In the root of the application, the following code can be found: ? php
$_SESSION [ ‘ medicine_details ’ ] = ‘ Your medication is: ‘ . $_SESSION [ ‘ medicine ’ ];
An attacker can manipulate this code to inject malicious sql code. This issue has been assigned the identifier VDB-207854. When this issue is exploited, the attacker may obtain sensitive information or execute arbitrary code. Red Hat would like to warn users about the vulnerability, recommend applying the patch, and suggest avoiding this software. End users receiving this software in email may consider filtering the message and blocking the sender address.
Vulnerability Details
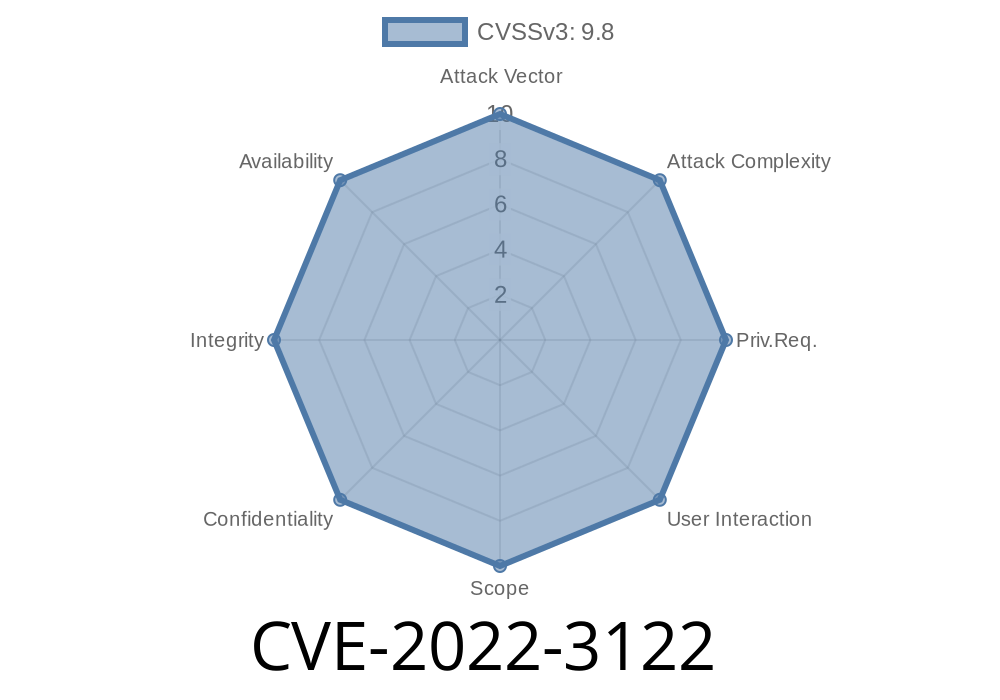
CVE: CVE-2022-3122
Vulnerability Type: SQL Injection
Vulnerability Status: Patch available
Severity: Critical
SQL Injection
SQL injection is an exploit that usually exploits input validation errors in SQL queries. Injection attacks are commonly used to compromise web applications and databases. These attacks most often take advantage of vulnerabilities in the database management system (DBMS). By injecting SQL code into queries, such as those performing input validation, attackers can manipulate data or even gain unauthorized access to the database. The vulnerability allows an attacker to inject malicious sql code via the following route: In the root of the application, the following code can be found: ? php
$_SESSION [ ‘ medicine_details ’ ] = ‘ Your medication is: ‘ . $_SESSION [ ‘ medicine ’ ];
An attacker can manipulate this code to inject malicious sql code. This issue has been assigned the identifier VDB-207854. When this issue is exploited, the attacker may obtain sensitive information or execute arbitrary code. Red Hat would like to warn users about the vulnerability, recommend applying the patch, and suggest avoiding this software. End users receiving this software in email may consider filtering the message and blocking the sender address.
Vulnerability Finding Tips
- VDB-207854 - CVE-2022-3122 - Medicine Details SQL Injection
The software is vulnerable to SQL injection. By manipulating certain parameters, an attacker may obtain sensitive information or execute arbitrary code. The problem appears in the medicine_details.php script. By changing the value of the argument ‘ medicine ’, an attacker may inject and execute arbitrary sql code. The vulnerability allows an attacker to inject malicious sql code via the following route: In the root of the application, the following code can be found: ? php
- $_SESSION[‘medication_details’] = ‘Your medication is:’.$_SESSION['medicine'];
An attacker can manipulate this code to inject malicious sql code. This issue has been assigned the identifier VDB-207854. When this issue is exploited, the attacker may obtain sensitive information or execute arbitrary code. Red Hat would like to warn users about the vulnerability, recommend applying the patch, and suggest avoiding this software.
Timeline
Published on: 09/05/2022 14:15:00 UTC
Last modified on: 09/08/2022 03:52:00 UTC