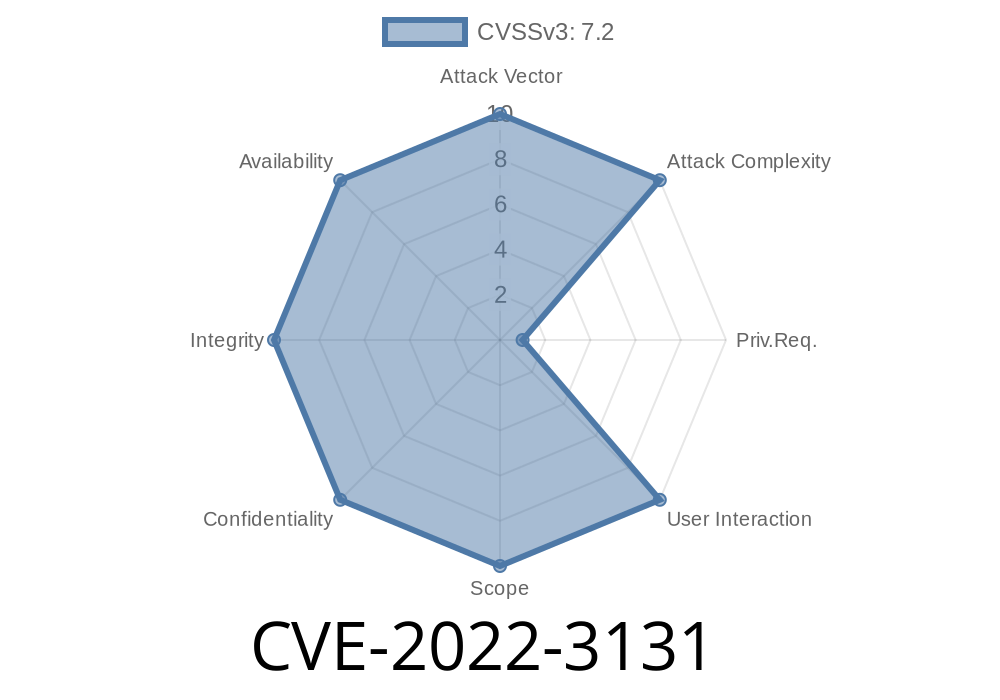
when you pass a parameter that has a non-escaped special character within the parameter to the Search Logger view, the SQL query is not properly sanitised and can lead to an exploitable condition that allows users with high privileges to execute SQL with those privileges.
To demonstrate this issue with an example, let’s assume a plugin that has a Search Logger view and inside that view, passes a parameter with a non-escaped special character. The plugin may look something like this:
Now let’s assume an attacker passes the following query to the plugin’s Search Logger view:
The SQL query here is injected with a non-escaped special character, ** and when that query is passed to the plugin’s Search Logger view, it is not properly sanitised and can result in an exploitable condition.
Steps to take to secure your plugin
The first line of defense is to escape all parameters in the Search Logger view. This can be accomplished by requiring a parameter in the view to be escaped, like this:
This would avoid the vulnerable condition.
How to exploit this vulnerability?
A vulnerability like this can be exploited by an attacker with high privileges.
This vulnerability can be exploited if the user running the vulnerable plugin is given elevated permissions and that user can access the Search Logger view, for example:
You will need to have a user account with sufficient privileges to see this view in order to exploit this vulnerability.
SQL Injection with Escape Characters
SQL injection vulnerabilities are a known issue with WordPress plugins. This vulnerability manifests itself when a plugin passes a parameter that contains an escaped special character to the Search Logger view within the plugin. The parameter will be passed with an escaped ** at the end, which will cause the SQL query to not be properly sanitised and can lead to an exploitable condition by users with privileges.
The function should have been written as:
Timeline
Published on: 10/17/2022 12:15:00 UTC
Last modified on: 10/21/2022 16:00:00 UTC