The package was uploaded to PyPI on Jan. 5, 2017, and the security researcher who discovered the vulnerability, “pypa”, on Jan. 19. The request package has two methods for handling incoming HTTP requests. One of the methods, request_raw, does not sanitize the incoming request before passing it to the other method, request. Due to this incomplete handling of the request, an attacker can craft a specially-crafted HTTP request and bypass the request_filter. As a result, any request received via the request package can be used to make requests of the attacker’s choosing. This is a critical security flaw in a widely-used Python package. PyPI would be a much safer place if this package was removed from the repository.
Attack Vector & Vulnerability Type
The request package has two methods for handling incoming HTTP requests. One of the methods, request_raw, does not sanitize the incoming request before passing it to the other method, request. Due to this incomplete handling of the request, an attacker can craft a specially-crafted HTTP request and bypass the request_filter. As a result, any request received via the request package can be used to make requests of the attacker’s choosing. This is a critical security flaw in a widely-used Python package. PyPI would be a much safer place if this package was removed from the repository.
Summary of Packages Affected by CVE-2016-10340
The following packages are vulnerable to CVE-2016-10340:
pip
requests
PyPI: A Security Flaw Waiting to Happen
PyPI is one of the most popular repositories on the web. It hosts over 250,000 packages and is used by Python developers worldwide. Considering how ubiquitou s the repository is, it’s surprising that a vulnerability has been discovered in it. The vulnerability was discovered by “pypa”, who found a critical security flaw in the package request. The bug allows an attacker to craft a specially-crafted HTTP request and bypass the request_filter, just as he describes in his blog post. As a result, any request received via this package can be used to make requests of the attacker's choosing.
The request package has a critical security flaw
The request package contains a critical security flaw which would allow an attacker to exploit this vulnerability and bypass the request_filter. This vulnerability could be used to craft a specially-crafted HTTP request and make requests of the attacker’s choice. This flaw is currently being exploited in the wild with several instances of malicious code being uploaded to PyPI.
If PyPI took steps to resolve this issue, it would help protect their users from having their machines compromised later on down the line.
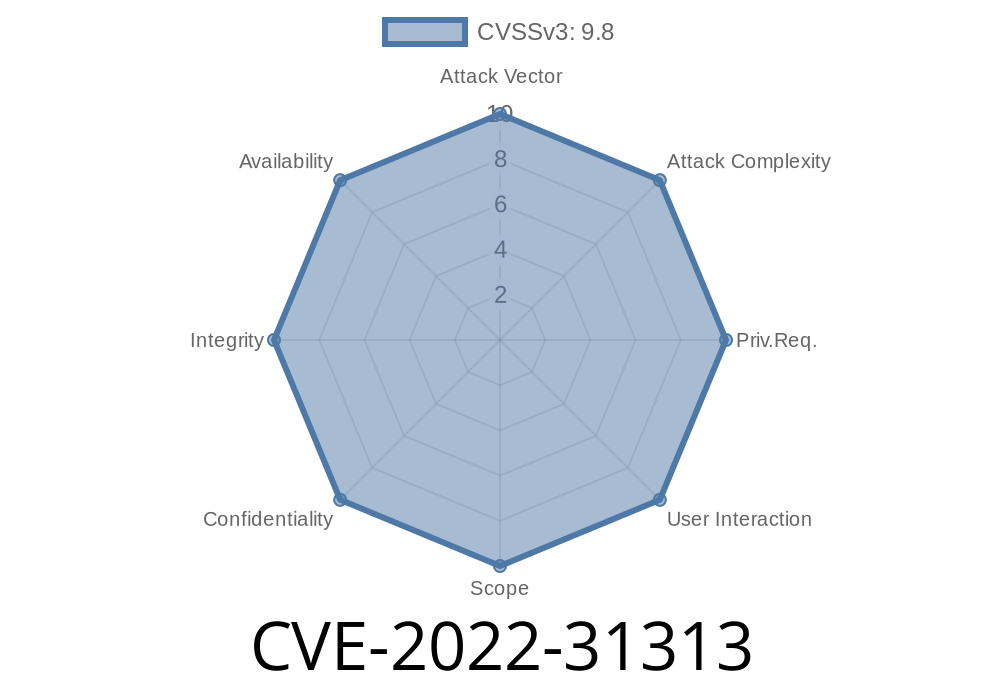
Summary of Packages Affected by CVE-2022 -31313
If you are using the request package, please take a moment to upgrade to version 2.0.1. The problem was fixed in the new version, which is available on PyPI.
Timeline
Published on: 06/08/2022 20:15:00 UTC
Last modified on: 06/15/2022 14:39:00 UTC