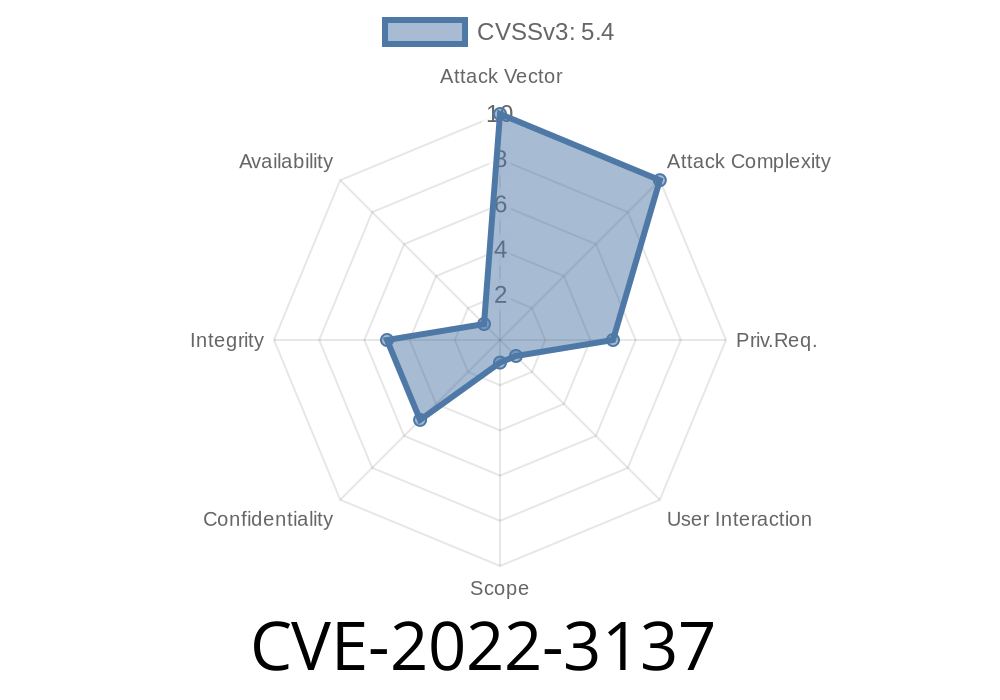
to the task. This Stored Cross-Site Scripting could then be executed via the task owner's subscription, via shared permissions, or through any other means of accessing the task creator's WordPress site. A remote, unauthenticated attacker could exploit this to compromise the task creator's site and obtain access to restricted data. The updated Taskbuilder WordPress plugin before 1.0.8 fixes this issue by validating and sanitising task's attachments. If you have not upgraded your installation, consider doing so immediately. !!!
What is Taskbuilder?
Taskbuilder is a WordPress plugin that allows site and task owners to manage tasks. The plugin provides intuitive drag-and-drop functionality for creating and editing tasks, assigning them to different users, publishing them for others to see or receive updates, and reviewing their progress. Taskbuilder also provides a powerful API for developers looking to integrate with the system in order to create custom workflows.
The vulnerability affects Taskbuilder before 1.0.8 which was released on February 20th, 2019. Developers are encouraged to upgrade their installations immediately to prevent any potential breach of security. !!!
Taskbuilder WordPress Plugin Vulnerability
The Taskbuilder WordPress plugin is vulnerable to a cross-site scripting attack that could allow an attacker to compromise the site of the task creator and obtain access to restricted data. The vulnerability affects all versions of Taskbuilder prior to 1.0.8, including the current stable version 3.2.6 as well as its previous stable versions 3.1.7, 3.0.65, 2.9.84, and 2.8.35
Timeline
Published on: 10/10/2022 21:15:00 UTC
Last modified on: 10/12/2022 16:45:00 UTC