This can be exploited to hijack admin privileges or obtain sensitive information from the database. The severity of this vulnerability depends on the nature of the application and the data that is stored in the database. Some applications are quite sensitive and keep personal data of users. By injecting a SQL query with backticks, an attacker can access and modify these data sources. Another important factor that can influence the risk of exposure of the application data is the patch level of the application. By choosing a specific language and adding a special character, the application can be exploited to inject a SQL query with backticks. If the application is patched at a specific patch level, then the application is likely to be patched at the same level, making the application quite secure.
Impact : An attacker can inject a time-based blind SQL injection to access the database and manipulate data.
CVE: N/A EFFECTIVE DATE: As of version 2.3.4, the vendor has released a fixed version.
Summary
This vulnerability is time-based and can allow an attacker to access the database. The severity of this vulnerability depends on the nature of the application. Some applications store personal data of users, so it is important to keep patch levels updated.
SQL Injection in MySQL
There are a few ways SQL injection can occur. One of the most common is through time-based blind SQL injection. This exploit is possible because of the way MySQL handles character set restrictions. By injecting a special character (in this case the backtick, `) and choosing a specific language setting, an attacker may be able to inject a SQL query with backticks into a MySQL database.
Impact : An attacker can access data from the database through time-based blind SQL injection.
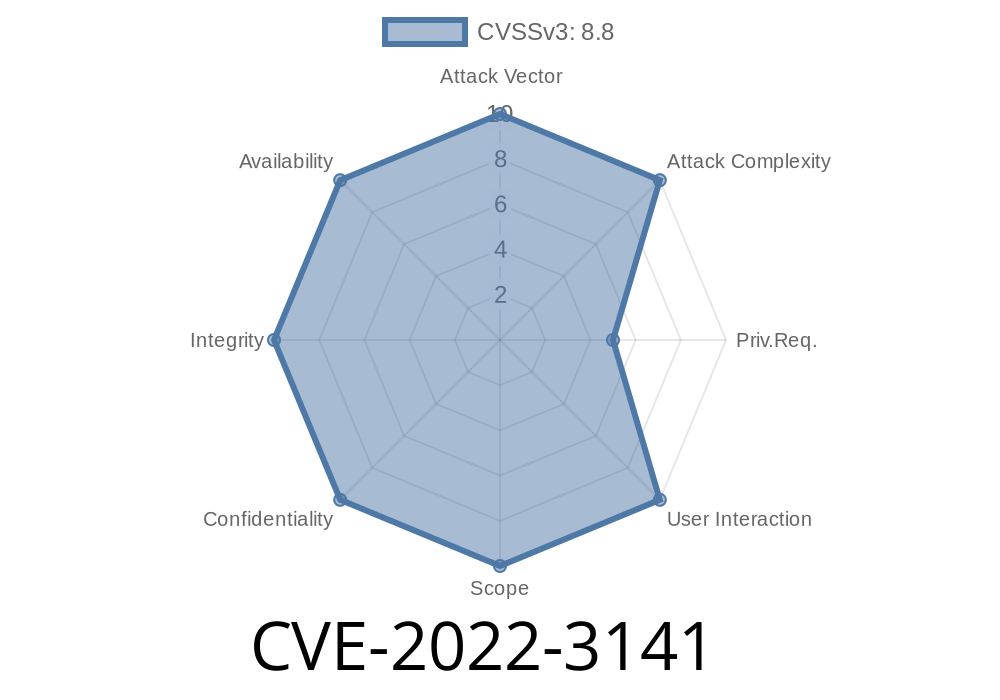
CVE: CVE-2022-3141 EFFECTIVE DATE: As of version 2.3.4, the vendor has released a fixed version."
Overview of the vulnerability
The CVE-2022-3141 vulnerability can be exploited to hijack admin privileges or obtain sensitive information from the database. The severity of this vulnerability depends on the nature of the application and the data that is stored in the database. Some applications are quite sensitive and keep personal data of users. By injecting a SQL query with backticks, an attacker can access and modify these data sources. Another important factor that can influence the risk of exposure of the application data is the patch level of the application. By choosing a specific language and adding a special character, the application can be exploited to inject a SQL query with backticks. If you want to protect your app from this vulnerability, make sure that you have version 2.3.4 or higher installed and ensure that your patch levels are up to date (starting at 2.2)
Timeline
Published on: 09/19/2022 14:15:00 UTC
Last modified on: 09/21/2022 13:18:00 UTC