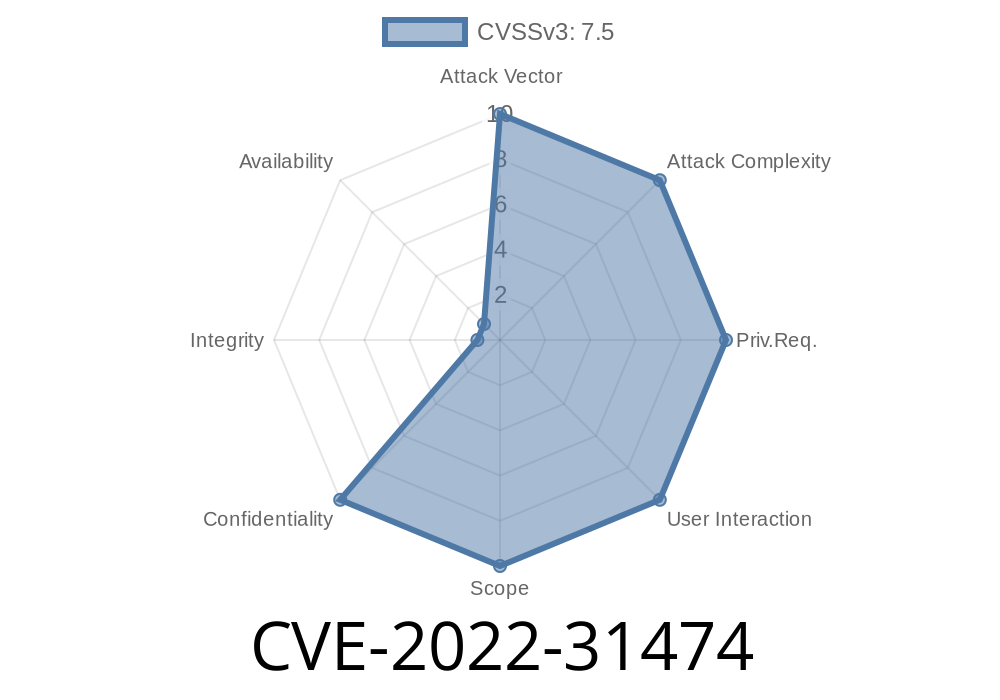
WordPress is the world’s most popular CMS, and its security plugins are supposed to protect rather than expose. However, in 2022, a severe flaw called CVE-2022-31474 was discovered in the BackupBuddy plugin by iThemes (now SolidWP). If you used BackupBuddy between versions 8.5.8. and 8.7.4.1, your files—and possibly even your whole site—were wide open to attackers.
This post takes you step-by-step through what went wrong, how the exploit worked (with code snippets), and how it was fixed. The language is simple so anyone responsible for WordPress sites can understand.
What is iThemes BackupBuddy?
BackupBuddy is a premium WordPress plugin for site owners to schedule backups or restore their sites easily. It lets admins download database and file backups via the WordPress admin page—super convenient, but as you’ll see, can also be dangerous.
What is Directory Traversal (Path Traversal)?
Directory Traversal is a classic web vulnerability. In simple terms, it means an attacker can trick your software into giving access to files *outside* the folder that’s supposed to be accessible. This often happens with user inputs that are not properly sanitized, such as filenames.
For example, asking the software for this file
../../../wp-config.php
Could bypass download restrictions and even expose your entire WordPress configuration, including database passwords.
The Vulnerability (CVE-2022-31474) Explained
The root of the issue was with BackupBuddy’s /wp-admin/admin-post.php?action=download_backup endpoint. This PHP handler was supposed to let authenticated admins download created backup files. However, the filename parameter (backupbuddy_backup) was not properly validated.
Here’s a simplified vulnerable code snippet (not the *exact* code, but functionally similar)
// Get filename from user input
$backup_file = $_GET['backupbuddy_backup'];
$file = BACKUPBUDDY_BACKUP_PATH . $backup_file; // BAD: direct use of user input!
if(file_exists($file)) {
header('Content-Type: application/zip');
// ... rest of headers
readfile($file);
exit;
} else {
echo "Backup file not found.";
}
What’s wrong?
- There is *no* check to make sure $backup_file is only a filename and not a path like '../../../../../wp-config.php'.
So, the attacker’s HTTP request could simply be
GET /wp-admin/admin-post.php?action=download_backup&backupbuddy_backup=../../../wp-config.php
With this, the web server would return the actual wp-config.php file, exposing secrets.
How Attackers Exploited CVE-2022-31474
Research by Wordfence disclosed that over five million sites were targeted within a few days. Attackers used automated scripts to scan for vulnerable sites and download sensitive files—config, credentials, and more.
Proof-of-Concept Exploit
If you had valid credentials (the attack worked for admins and—*in some cases*—even for unauthenticated users if the site had certain misconfigurations), you could exploit like this using curl or your browser:
curl "https://victim-site.com/wp-admin/admin-post.php?action=download_backup&backupbuddy_backup=../../../wp-config.php"; -o stolen-config.php
How Was It Patched?
The vendor quickly released BackupBuddy 8.7.5, which properly sanitizes the filename parameter.
Here’s a fixed version of the vulnerable logic
$backup_file = basename($_GET['backupbuddy_backup']); // Only use the filename, stripping paths
$file = BACKUPBUDDY_BACKUP_PATH . $backup_file;
if (file_exists($file) && strpos(realpath($file), realpath(BACKUPBUDDY_BACKUP_PATH)) === ) {
// OK to serve
readfile($file);
}
The key:basename ensures no path traversal is possible, and realpath makes sure the file is *inside* the intended directory.
### What You Should Do (If You Use/Used BackupBuddy)
Update Immediately: Never run old versions. Patches are your friend.
2. Check for Unusual Files: Look for files you didn’t create in your WordPress root or backup folder.
Further Reading & References
- NVD Entry – CVE-2022-31474
- Wordfence Blog: Active Exploitation of BackupBuddy Plugin Vulnerability
- iThemes Blog: Critical Security Vulnerability in BackupBuddy
Conclusion
CVE-2022-31474 is a textbook example of why never to trust user input, especially when dealing with files. Directory traversal bugs can instantly undermine your entire security—and in the highly targeted WordPress ecosystem, attackers are waiting for plugin mistakes like this. Stay updated and audit your plugins often!
*This exclusive breakdown is designed to raise practical awareness—share with anyone managing a WordPress site!*
Timeline
Published on: 03/13/2023 14:15:00 UTC
Last modified on: 03/16/2023 20:05:00 UTC