This function reads the entire file into memory, so an attacker can use it to inject malicious code into the application. The attacker needs only to set the input path to the application to inject malicious code. For example, an attacker can add the following code to an application’s settings.py file, and then the application will use this input path when the application sends data to the logstash management API: input_file = ‘/path/to/malicious/code’. After this vulnerability is found, it needs to be fixed as soon as possible. To ensure that the vulnerability is fixed as quickly as possible, the following steps are recommended: Find a developer who can fix the vulnerability as soon as possible.
Inspect the Application Environment
An important step in fixing this vulnerability is to inspect the application’s environment. If the application is running on a server, then it should be possible to inspect the logs of the server. If not, then an attacker may use a tool like curl or wget to download files from the server and inspect them for malicious code.
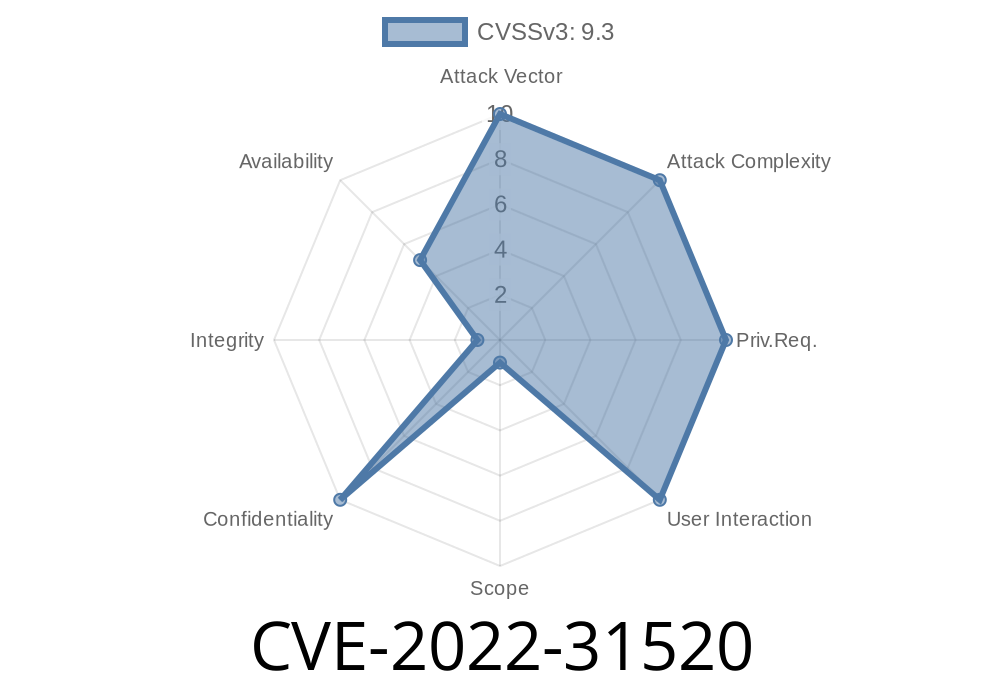
Detect if your installation is vulnerable to CVE-2022-31520
The easiest way to detect if your installation is vulnerable to this vulnerability is to use a script that checks the version of logstash. If the version of logstash doesn’t have a fix for this vulnerability, then it’s probably time to upgrade.
Is Logstash Vulnerable to CVE-2022-31520?
Timeline
Published on: 07/11/2022 01:15:00 UTC
Last modified on: 07/15/2022 11:27:00 UTC