or purchase add-ons. In addition, the plugin does not offer any protection against CSRF on its Contact Form. The only way to fix this issue is to update to version 4.4.5.5 or higher. This issue was resolved in version 4.4.5.5. In addition, the following WordPress plugins that are integrated with Woo Billingo Plus were also affected by this issue: Integration for Billingo & Gravity Forms WordPress plugin before 1.0.4, Integration for Szamlazz.hu & Gravity Forms WordPress plugin before 1.2.7. Update to version 4.4.5.5 or higher is required to protect against this issue.
CSRF vulnerabilities in WordPress plugins
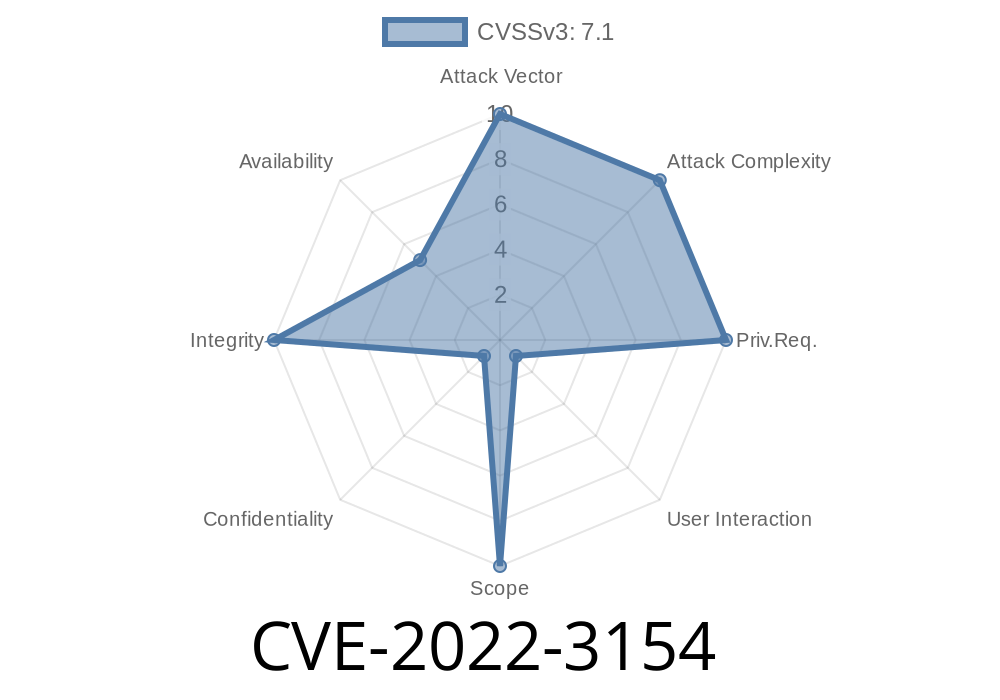
A Cross-Site Request Forgery (CSRF) vulnerability was discovered in a WordPress plugin. It allows an attacker to bypass the current security measures, allowing them to execute unauthorized actions on the targeted website. This may include creating or editing content, logging in as a different user, or deleting content.
The vulnerability exists because the plugin does not properly validate GET requests from users on certain pages that are not protected by a CAPTCHA. A CSRF vulnerability is present in both versions of the plugin and requires updating to v4.4.5.5 or higher for protection against this issue.
Summary of Severity and Importance
The severity of this vulnerability is low because there are no known attacks targeting this vulnerability. The vulnerability could allow an attacker to bypass authentication and send spam or delete content on the website. This vulnerability does not affect WooCommerce products and does not require a password for exploitation.
What is a CSRF vulnerability?
Cross-site request forgery (CSRF) is an attack that tricks a user into performing an unwanted action on a web application in which the malicious user does not have the same privileges. This happens when the malicious user sends a covert request to perform an unauthorized action on behalf of the victim, typically without the victim's knowledge and consent
This vulnerability is caused by missing input validation, with attackers being able to exploit it to gain access to confidential data or perform actions on behalf of other users.
Timeline
Published on: 10/10/2022 21:15:00 UTC
Last modified on: 10/13/2022 15:19:00 UTC