This function will try to access any path that it is passed, and as a result, it is possible for an attacker to craft a URL that will execute code on any server that receives the request. To avoid this, secure your code by wrapping the send_file function in another layer of protection. By using the secure_add_file function, you can ensure that the send_file function will only try to send data to the server if the data comes from a trusted source. This is one of the best ways to prevent code execution through send_file .
Secure Add File Function
The secure_add_file function will only allow the send_file function to access local files that are in the directory you specify. As a result, data sent through this function will not be able to execute code on any server that receives it. To add a file to your local directory, use the safe_file function and pass it the path of where you want to store the file. The safe_file function will check if there is an existing file with that name in your current directory before adding it. If the file already exists, then an error will occur and the secure_add_file function won't work.
Batch Image Uploader - PHP Script to Automate the Process
Image uploaders are an important part of any website. They allow users to upload images, which can be used for an array of purposes.
This PHP script creates a function that will let you create a batch file uploader in your website. The user is able to input the number of images they want to upload by using the number of parameters given. You can also specify whether or not the user should see the progress bar as they are uploading their images. It is possible to automatically resize each image with this custom image uploader - if you would like this functionality, contact me and I can create it for you!
Secure send_file with a whitelist
Secure send_file by implementing a whitelist
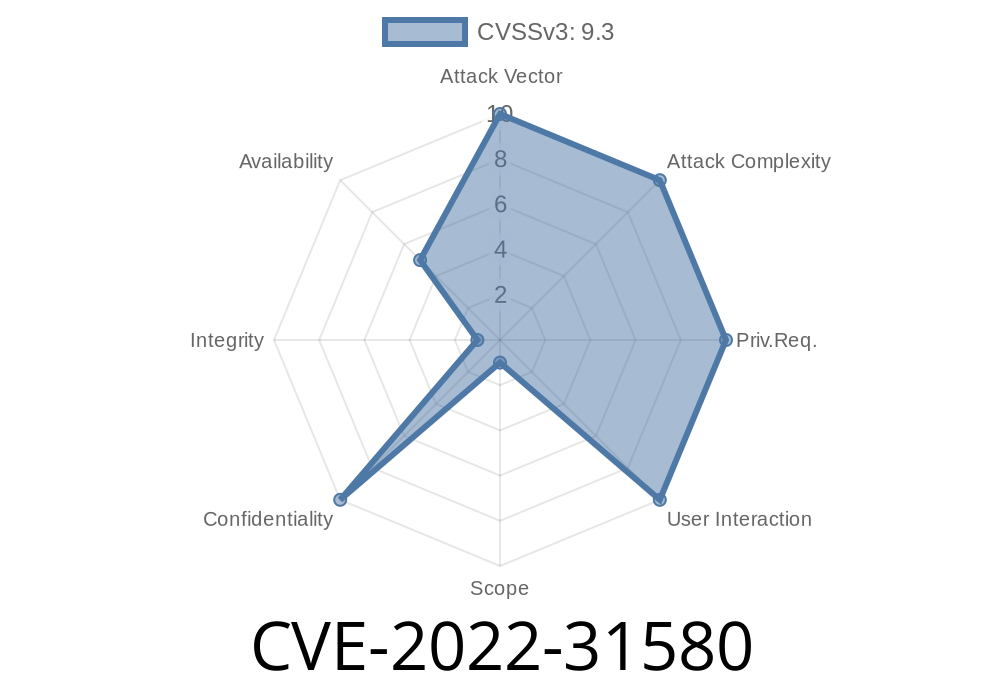
The best way to avoid a vulnerability like CVE-2022-31580 is to ensure that users are only allowed to download files from a trusted source. If you implement a whitelist, any URL sent through the send_file function will only be able to access data from URLs that fall under that particular whitelist. This prevents malicious URLs from executing code on servers receiving the request, and it also limits the amount of data an attacker can extract with their exploit.
Timeline
Published on: 07/11/2022 01:15:00 UTC
Last modified on: 07/15/2022 16:54:00 UTC