The vulnerability may be exploited by crafting a malicious VMX script that causes a crash in the VMX process. An attacker may craft such a script to cause a crash in the VMX process, and then pass control to another VMX script. The second VMX script may then pass control to the first VMX script, causing a crash and restart of the VMX process. This process may be repeated indefinitely, resulting in a denial of service condition.
The vulnerability has been assigned the CVE identifier CVE-2018-10881. Vulnerable versions of VMware ESXi 5.5, 6.0, and 6.5 are potentially affected. It is recommended that customers apply the appropriate patch as soon as it becomes available. Patches are currently being distributed via VMware vSphere Update Manager (VUM) and the ESXi installation CD/DVD. It is possible that the installation process may detect and prevent the execution of the patch. In this case, it is recommended that the ESXi installation be reverted to an older version, and then run the installation process again.
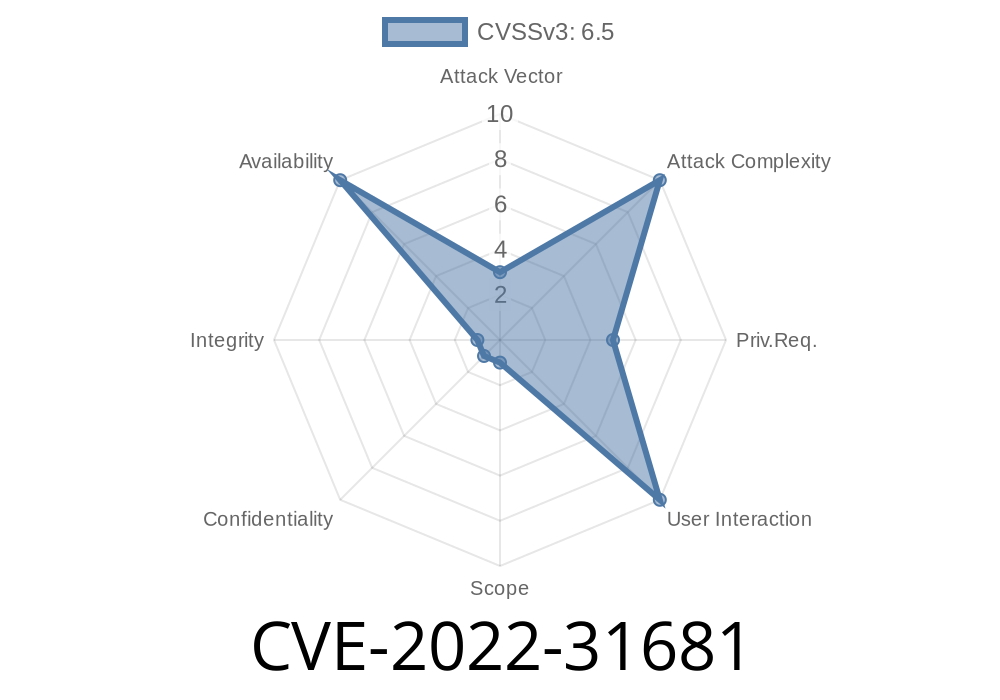
Vulnerability Details
A flaw has been discovered in VMware ESXi that may lead to a denial of service condition.
The issue is triggered when a malicious Vmx script is executed. The Vmx script causes the VMX process to crash, and then another malicious Vmx script is executed which passes control to it, causing a crash and restart of the VMX process, which could be repeated infinitely.
Vulnerability Overview
VMware ESXi is vulnerable to a denial of service condition in which an attacker may exploit the vulnerability by crafting a malicious VMX script that causes a crash in the VMX process. Once crashed, the attacker may pass control to another VMX script and cause repeated crashes, resulting in denial of service conditions.
The vulnerability has been assigned the CVE identifier CVE-2018-10881. Vulnerable versions of VMware ESXi 5.5, 6.0, and 6.5 are potentially affected. It is recommended that customers apply the appropriate patch as soon as it becomes available. Patches are currently being distributed via VMware vSphere Update Manager (VUM) and the ESXi installation CD/DVD. It is possible that the installation process may detect and prevent the execution of the patch. In this case, it is recommended that the ESXi installation be reverted to an older version, and then run the installation process again.
Timeline
Published on: 10/07/2022 21:15:00 UTC
Last modified on: 10/11/2022 13:45:00 UTC