The flaw is located in the WebAccess web-application, which is accessible through a browser via HTTP or HTTPS. Once the user is authenticated, the attacker may be able to retrieve configuration data, such as usernames, passwords, or email addresses. It is recommended to patch this application as soon as possible to avoid data exposure. Aria Operations also contains a XSS flaw. A malicious actor may be able to inject a script into the WebAccess web-application to steal data from the user.
Aria Operations Vulnerability
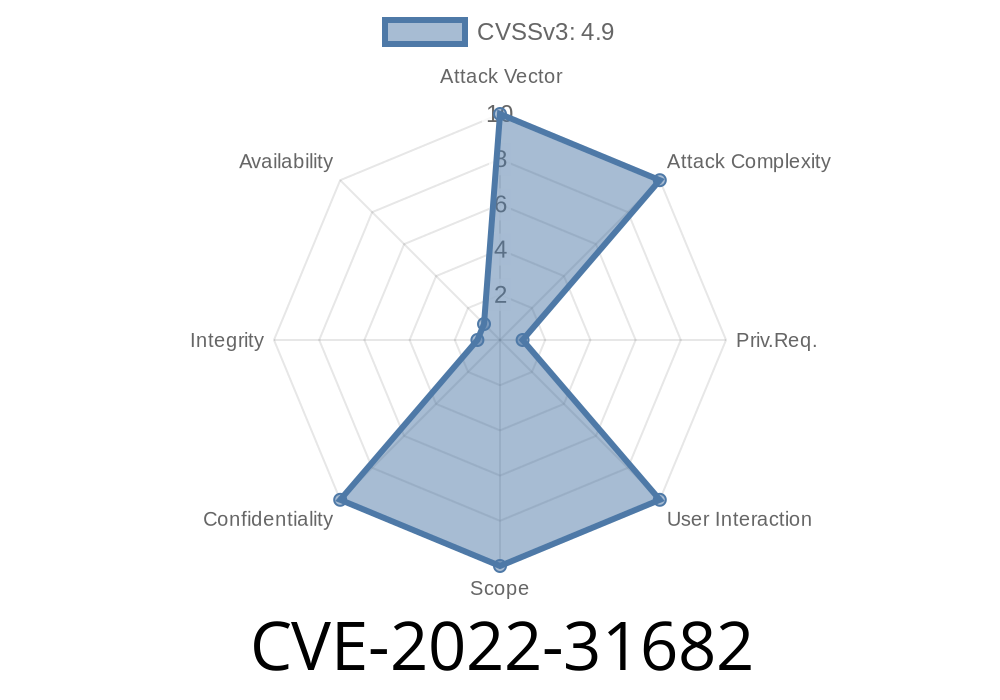
An Aria Operations vulnerability, CVE-2022-31682, has been discovered. This flaw is located in the WebAccess web-application, which is accessible through a browser via HTTP or HTTPS. Once the user is authenticated, the attacker may be able to retrieve configuration data, such as usernames, passwords, or email addresses. It is recommended to patch this application as soon as possible to avoid data exposure.
A brief overview of Aria Operations vulnerabilities
Aria Operations, a web-application developed by Aria Systems, includes a number of vulnerabilities. The flaw is located in the WebAccess web-application, which is accessible through a browser via HTTP or HTTPS. Once the user is authenticated, the attacker may be able to retrieve configuration data, such as usernames, passwords, or email addresses. It is recommended to patch this application as soon as possible to avoid data exposure. Aria Operations also contains a XSS flaw. A malicious actor may be able to inject a script into the WebAccess web-application to steal data from the user.
A Look at the Vulnerability
A vulnerability that affects Aria Operations, a CRM application. This flaw can be exploited to steal data from the users of the web-application.
It is recommended to patch this application as soon as possible to avoid data exposure and malicious actors stealing data.
Aeria Operations
Aeria Operations is the company behind many popular games such as Lineage 2, Aeria Games, and others.
This flaw is located in the WebAccess web-application that is accessible through a browser via HTTP or HTTPS. Once the user is authenticated, the attacker may be able to retrieve configuration data, such as usernames, passwords, or email addresses. It is recommended to patch this application as soon as possible to avoid data exposure.
A list of Aria Operations software and versions affected
Aria Operations Applications Affected:
Aria Operations Web Browser
Aria Operations Accounting System
Aria Operations Financials
Aria Operations HR
Aria Operations Catalog
Timeline
Published on: 10/11/2022 21:15:00 UTC
Last modified on: 10/13/2022 16:56:00 UTC