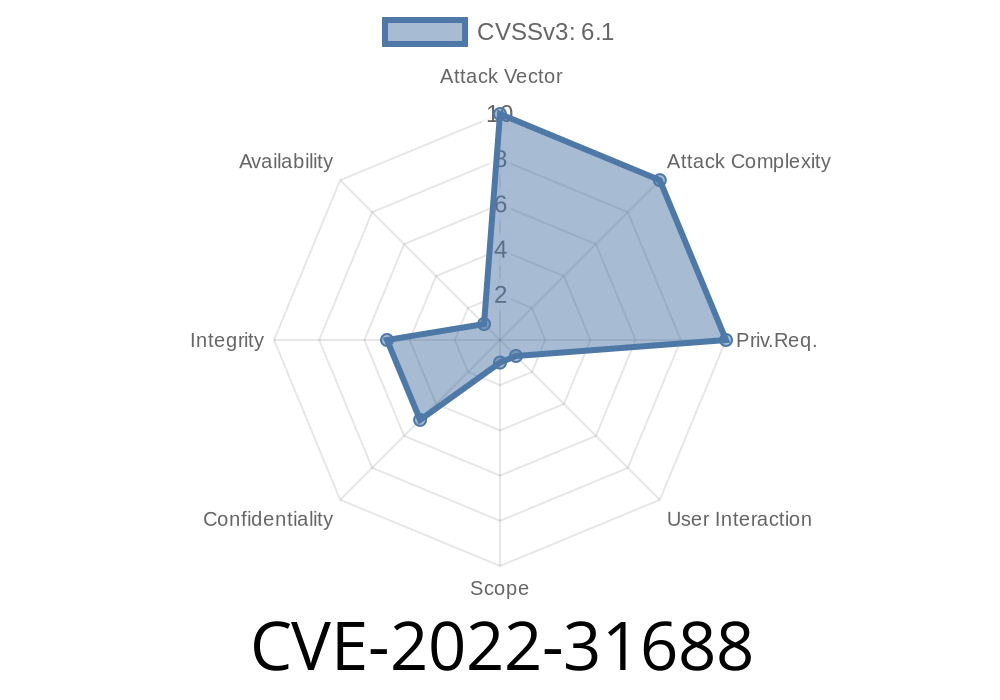
This can lead to the execution of arbitrary code with the privileges of the user who is viewing the malicious webpage.
In order to exploit this vulnerability, an attacker must trick a user into visiting a malicious webpage or launch an attack against the user via a malicious email attachment or web page.
Vulnerability can be exploited by tricking the user into visiting a malicious webpage or launch an attack via a malicious email attachment or web page.
In order to exploit this vulnerability, an attacker must trick a user into visiting a malicious webpage or launch an attack against the user via a malicious email attachment or web page.
Prior to version 22.10, ESXi hosts were not supported.
Prior to version 22.7, hosts were not supported.
Prior to version 22.5, hosts were not supported.
Prior to version 22.4, hosts were not supported.
Prior to version 22.3, hosts were not supported.
Prior to version 22.2, hosts were not supported.
Prior to version 22.1, hosts were not supported.
Prior to version 22.0, hosts were not supported.
Prior to version 21.5, hosts were not supported.
Prior to version 21.4, hosts were not supported.
Prior to version 21.3, hosts were not supported.
Prior to version 21.2, hosts were not supported.
Prior to version 21.
Vulnerability Scenario
An attacker could exploit this vulnerability by tricking a user into visiting a malicious webpage or launching an attack against the user via a malicious email attachment or web page.
Vulnerability Description
Prior to version 22.10, ESXi hosts were not supported.
Timeline
Published on: 11/09/2022 21:15:00 UTC
Last modified on: 11/10/2022 19:51:00 UTC