This issue may lead to information disclosure or session hijacking. A user with low credibility may also be fooled into entering confidential data, such as password.
Affected version: v14.0.0 of OpenAM Consortium
Affected operating system: All
Impact of vulnerability: session hijacking, information disclosure
CVE number: not available yet Open Redirect Vulnerability in OpenAM Consortium - https://www.vulnerability-lab.com/show/nmap/open-redirect-vulnerability/
Summary of the Issue
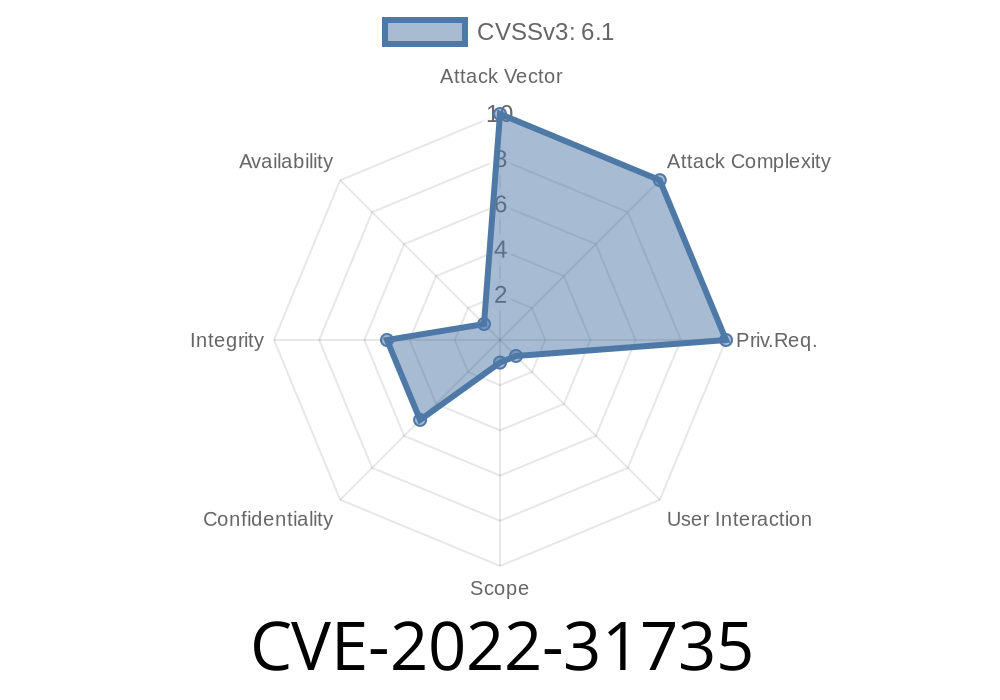
It has been reported that OpenAM Consortium v14.0.0 is vulnerable to a "High" severity CVE-2022-31735 vulnerability. By exploiting this vulnerability, an attacker could potentially obtain sensitive data from the target system such as passwords or session information.
Summary
OpenAM is an open source implementation of Active Directory Federation Services (ADFS).
This vulnerability was discovered during testing of the OpenAM product
and is related to authentication. Potential attack vectors include social engineering, local privilege escalation, and web server exploitation.
Upon successful exploitation, the attacker could gain root access on the system and perform arbitrary actions with the privileges of the target user.
Attacks can be mitigated by restricting administration tasks to trusted users only.
The vulnerability can be exploited remotely via a malicious social engineering attack or by exploiting a flaw in local privilege escalation. The impact will vary depending on environment configuration and whether or not a remote exploit was used.
Timeline
Published on: 09/15/2022 05:15:00 UTC
Last modified on: 09/19/2022 16:57:00 UTC