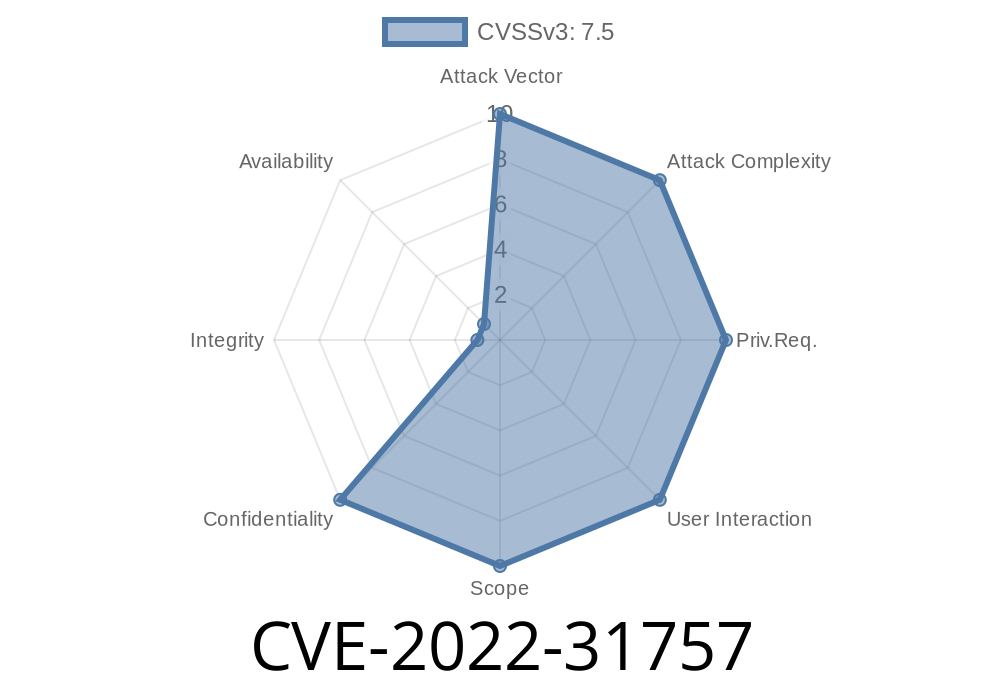
In order to exploit this vulnerability, an attacker must be able to convince an authenticated user to visit a specially crafted website.
It has been reported that the setting module improperly validates user-submitted data. An attacker can exploit this vulnerability to perform cross-site request forgery (CSRF). In order to exploit this vulnerability, the attacker must make a request to the setting page that the victim has access to. If the victim is logged in to the site and visits the setting page, the attacker can submit a request to change data.
An attacker can exploit this vulnerability to perform request tampering. In order to exploit this vulnerability, the attacker must create a request that will cause the setting module to process the request. This can be done by changing the value of a cookie or by submitting a request for data that the setting module does not expect.
It has been reported that the setting module has a vulnerability of improper use of API. Successful exploitation of this vulnerability may result in sensitive information exposure.
In order to exploit this vulnerability, an attacker must be able to convince an authenticated user to visit a specially crafted website.
It has been reported that the setting module improperly validates user-submitted data. An attacker can exploit this vulnerability to perform cross-site request forgery (CSRF)
General Recommendations
If your organization is already using Drupal, there are a few recommendations you can follow to protect against exploits:
- Review your settings. Even if you do not have any custom settings, be sure that the default settings are appropriate for your organization.
- Make sure that the site is not accessible via public Wi-Fi networks.
- Make sure you have installed security updates recently.
Timeline
Published on: 06/13/2022 16:15:00 UTC
Last modified on: 06/27/2022 16:14:00 UTC