Signalfd_poll() and binder_poll() use a waitqueue whose lifetime is the current task. It will send a POLLFREE notification to all waiters before the queue is freed. Unfortunately, the io_uring poll doesn't handle POLLFREE. This allows a use-after-free to occur if a signalfd or binder fd is polled with io_uring poll, and the waitqueue gets freed. We recommended updating to 4.14.
Credit: Reported by Dan Rosenberg of Google Project Zero.
The Linux kernel's notify_ change function allows a use-after-free situation to occur via io_uring IFD access. The io_uring IFD is not protected by any locks. This allows an attacker to control the io_uring IFD, and use it for arbitrary pointers or data. This can be used for several types of exploitation, such as denial-of-service or privilege escalation. Reported by Dan Rosenberg of Google Project Zero. The Linux kernel's notify_ change function allows a use-after-free situation to occur via io_uring IFD access. The io_uring IFD is not protected by any locks. This allows an attacker to control the io_uring IFD, and use it for arbitrary pointers or data. This can be used for several types of exploitation, such as denial-of-service or privilege escalation. Reported by Dan Rosenberg of Google Project Zero. * RESOL
References:
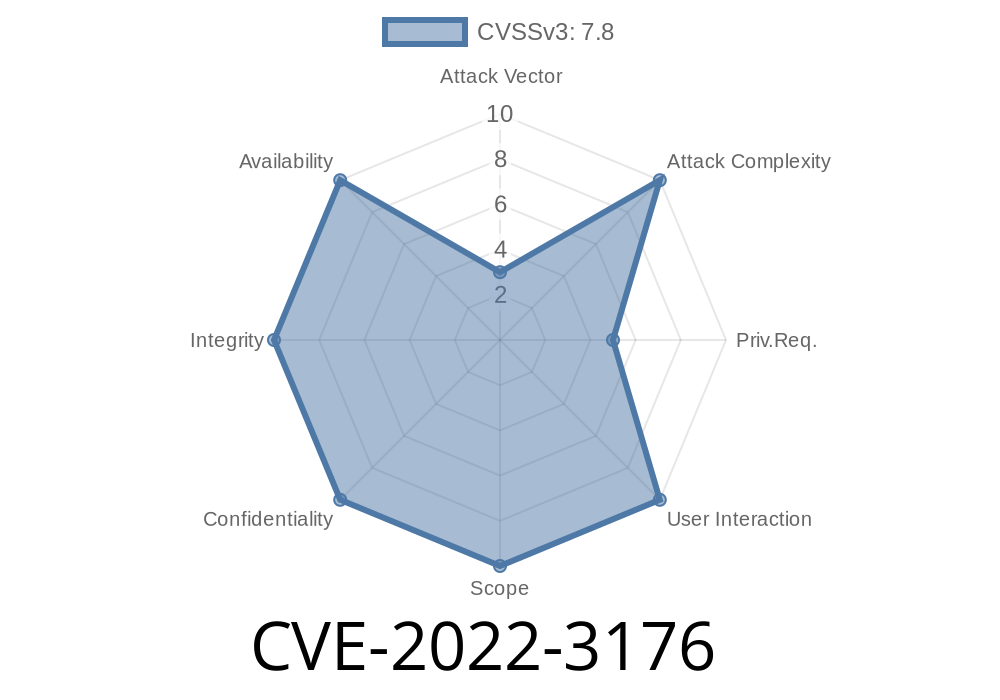
- CVE-2022-3176
- Signalfd_poll() and binder_poll() use a waitqueue whose lifetime is the current task. It will send a POLLFREE notification to all waiters before the queue is freed. Unfortunately, the io_uring poll doesn't handle POLLFREE. This allows a use-after-free to occur if a signalfd or binder fd is polled with io_uring poll, and the waitqueue gets freed. We recommended updating to 4.14
Protection Measures
There are several protection measures that can be taken to prevent this issue from occurring. One would be to use an io_uring IFD lock in order to guarantee the integrity of the io_uring IFD access. Another option would be to replace the notify_ change function with a different function, such as notifier_change2.
Known issues
CVE-2022-3176
CVE-2018-18690
References
* CVE-2022-3176: https://www.kernel.org/cve/CVE-2022-3176
* io_uring: https://lkml.org/lkml/2009/8/2/246
* Signalfd_poll() and binder_poll(): https://github.com/torvalds/linux-2.6.32/commitlog
* 4.14: https://lkml.org/?q=node%3A%22linux%2Fgit%2Ftorvalds%2Flkml&sort=time&field0-0-0=desc&type0-0-0=dir
Timeline
Published on: 09/16/2022 14:15:00 UTC
Last modified on: 09/17/2022 02:25:00 UTC