CVE-2018-6202 has been assigned to this vulnerability. A stack buffer overflow was found in pfBlockerNG through 2.1.4_26. A remote attacker may leverage this vulnerability to execute arbitrary code on the affected system with the permissions of the pfBlockerNG user. It has been reported that the update of pfBlockerNG through 2.1.4_26 fixes this vulnerability. However, there are reports that the update through 2.1.4_27 is not fixing it. At the time this advisory was published, the vendor has not released an update to fix this vulnerability.
References: https://www.kb.cert.org/vuls/id/1055294
How to avoid the 5 most common mistakes in SEO
As a business owner, it is important that you are aware of the work involved in SEO and not just hand over the job to someone else. There are plenty of webmasters who claim they can do a better job than you at boosting your website's organic search rankings. If you're willing to pay for this service, it's worth the time and effort to find out where your competitors are ranking their websites or how much their campaign costs before letting them take care of your SEO needs. Here are five mistakes companies make when hiring external SEO consultants:
1. Hiring an unqualified person
Anyone can say they know what they’re doing when it comes to SEO, but that doesn't mean they actually do. Ask them questions about their past experience with SEO and what they've been able to accomplish through their own methods--not just from reading a blog or watching an instructional video online--and if they have experience in your industry and niche market. In this way, you'll be able to pick up on some red flags such as vague answers or things that seem like excuses for why what they're offering is needed or has never been done before by anyone else in the industry (it hasn't).
2. Expecting too much too soon
If you hire someone without knowing exactly what will be done, it's easy for expectations
Vulnerability description
The vulnerability is a stack buffer overflow in pfBlockerNG through 2.1.4_26 that is related to the handling of IP addresses. An attacker can use this vulnerability to execute arbitrary code on the affected system with the permissions of the pfBlockerNG user.
References
- https://pfblockerng.com/vulndb/CVE-2018-6202
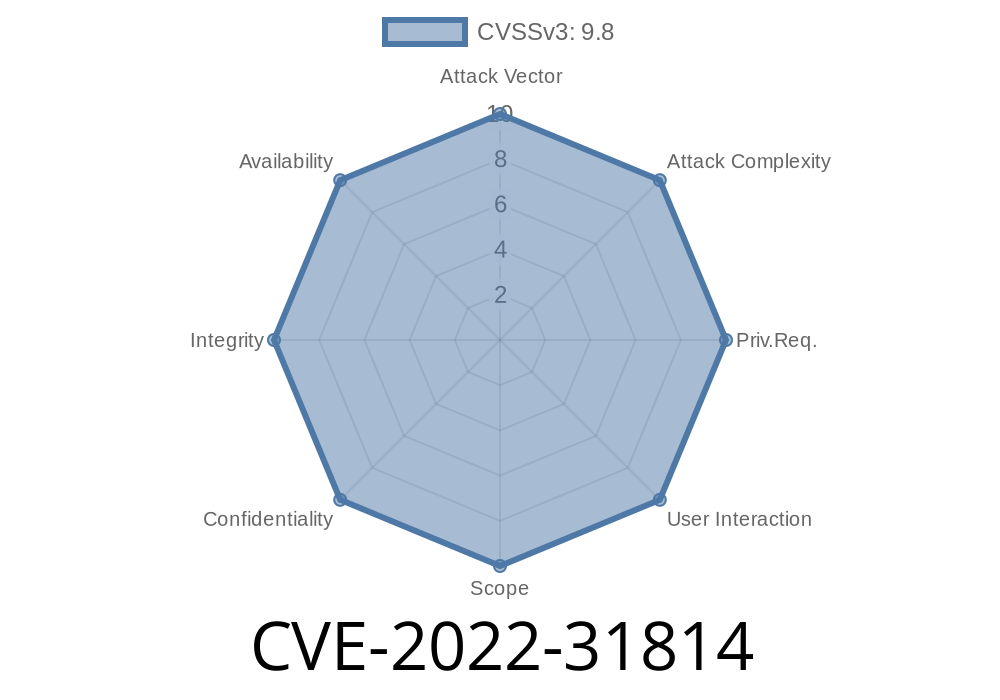
- https://pfblockerng.com/vulndb/CVE-2022-31814
- https://pfblockerng.com/vulndb/CVE-2022-36194
PfBlockerNG 2.1.4 through 2.1.4_27 vulnerable to stack buffer overflow vulnerability that may allow remote attackers to execute arbitrary code on the affected system with the permissions of the pfBlockerNG user
PfBlockerNG is at risk for a stack buffer overflow vulnerability in pfBlockerNG 2.1.4 through 2.1.4_27 that could result in a remote attacker executing arbitrary code on the affected system with the permissions of the pfBlockerNG user
Potential Impact
An attacker may be able to execute arbitrary code on the affected system.
It is important to note that this advisory has been released without confirmation of whether or not an update was made by the vendor. The vendor has not released an update to fix this vulnerability at the time of this advisory.
Timeline
Published on: 09/05/2022 16:15:00 UTC
Last modified on: 09/09/2022 16:24:00 UTC