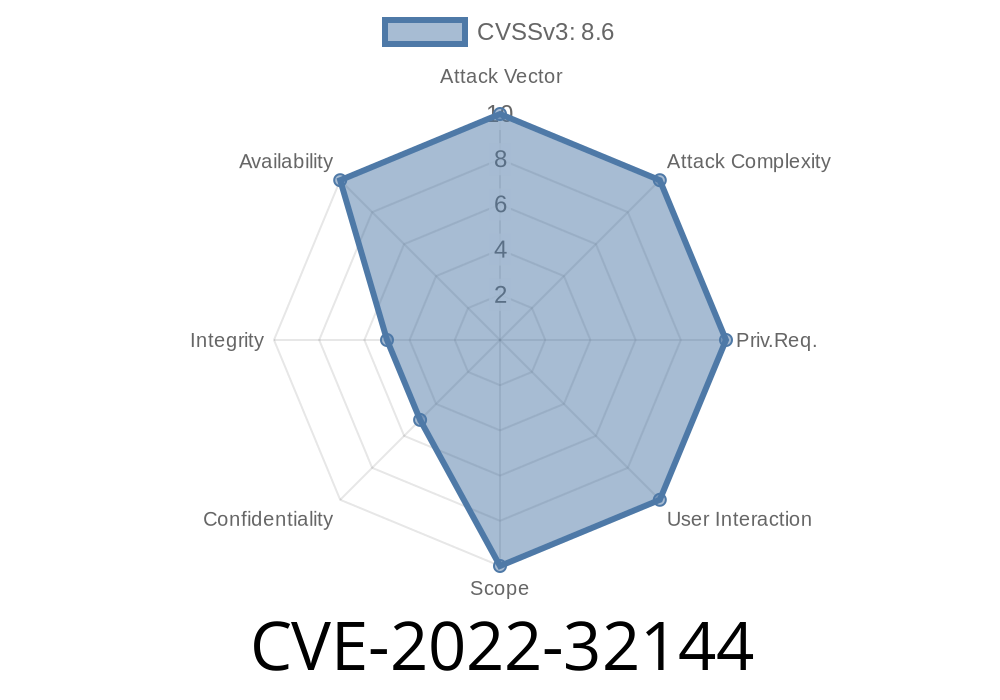
Security vulnerabilities in tech hardware can put both businesses and users at risk. One such vulnerability is CVE-2022-32144, officially identified by Huawei as HWPSIRT-2022-76192. This flaw relates to insufficient input verification and may result in service disruption if exploited successfully. In this article, we’re going to break down how this vulnerability works, look at possible exploit scenarios, and offer actionable advice.
What is CVE-2022-32144?
CVE-2022-32144 is a vulnerability discovered in some Huawei products, caused by improper validation of user input. If an attacker sends specially crafted data, the affected service may behave abnormally or even crash.
- CVE: CVE-2022-32144 entry
- Vendor Advisory: Huawei HWPSIRT-2022-76192
Where is the vulnerability?
The flaw is in the way certain Huawei software processes incoming data. Instead of carefully checking that the input matches expected formats or sizes, the software may accept and process incorrect or malicious data, leading to unexpected behavior.
For example, imagine a web service that expects a username no longer than 20 characters. If a user sends a string of 100 characters and the service does not verify the input size, the program’s behavior is unpredictable. This is the root cause of CVE-2022-32144.
Vulnerable Products
Huawei’s security advisory lists the affected versions and models. Please check their official advisory to see if your device is vulnerable.
Here’s a generic Python example to help understand the issue
# Example code with insufficient input verification
def process_username(username):
# Vulnerable: Does not check input size or content
print(f"Welcome, {username}!")
# Attacker sends a very large string
attacker_input = "A" * 100000
process_username(attacker_input)
The function process_username prints whatever string it receives, regardless of its content or size. This could cause service crashes or make logs unreadable.
Patched Version
# Secure code with input verification
def process_username(username):
if not username or len(username) > 20 or not username.isalnum():
print("Invalid username!")
return
print(f"Welcome, {username}!")
# Now, oversized or invalid inputs are rejected
Probe: The attacker sends malformed or oversized input to a service endpoint.
3. Crash: The device or service becomes unresponsive or throws errors, causing denial of service for legitimate users.
This kind of attack is often automated using simple scripts.
Below is a demonstration using curl (for illustration only)
curl -X POST http://target-device.local/api/login -d "username=$(python3 -c 'print("A"*100000)')"
Disclaimer: Do not use this code on devices you do not own or have explicit permission to test.
Mitigation & Fix
Huawei recommends upgrading to the fixed version as soon as possible. Their patch ensures strict input validation, preventing attackers from sending malicious requests.
Check your product’s firmware or software version.
- Visit the Huawei PSIRT Advisory for exact versions and patch information.
Where patching isn’t possible, restrict network access to the device.
To add additional security, network firewalls and input validation at the application layer are also best practices.
References
- Huawei Official Advisory HWPSIRT-2022-76192
- CVE-2022-32144 NIST Details
- General Input Validation Guidance (OWASP)
Summary
CVE-2022-32144 is a significant reminder of why input validation is critical in software and hardware products alike. By understanding the risk, following patch advisories, and applying strong validation practices, organizations can reduce the chances of a service outage caused by this kind of vulnerability.
Timeline
Published on: 12/20/2024 02:15:05 UTC