For Splunk Cloud Platform, update to Splunk Cloud Platform 8.2.2203 or later and Enable TLS host name validation for Splunk-to-Splunk communications (https://docs.splunk.com/Documentation/Splunk/8.2.2203/Cloud/Security/EnableTLSCertHostnameValidation) to enable the remediation. For information about which information that was potentially vulnerable when validated server certificates were disabled by default in Splunk Enterprise versions before 9.0 and Splunk Cloud Platform versions before 8.2.2203, see SECURITY RISK FACTORS (CVE-2019-10267) in the Splunk documentation.
## IMPACT Splunk Enterprise could be vulnerable to server-side cross-site scripting (XSS) attacks when an app or add-on that includes its own custom HTTP library is used. Apps or add-ons that include their own custom HTTP libraries are not affected by this issue. To remediate the issue, update to Splunk Enterprise version 9.0 or later and Enable TLS host name validation for Splunk-to-Splunk communications (https://docs.splunk.com/Documentation/Splunk/9.0.0/Cloud/Security/EnableTLSCertHostnameValidation) to enable validation of server certificates by default.
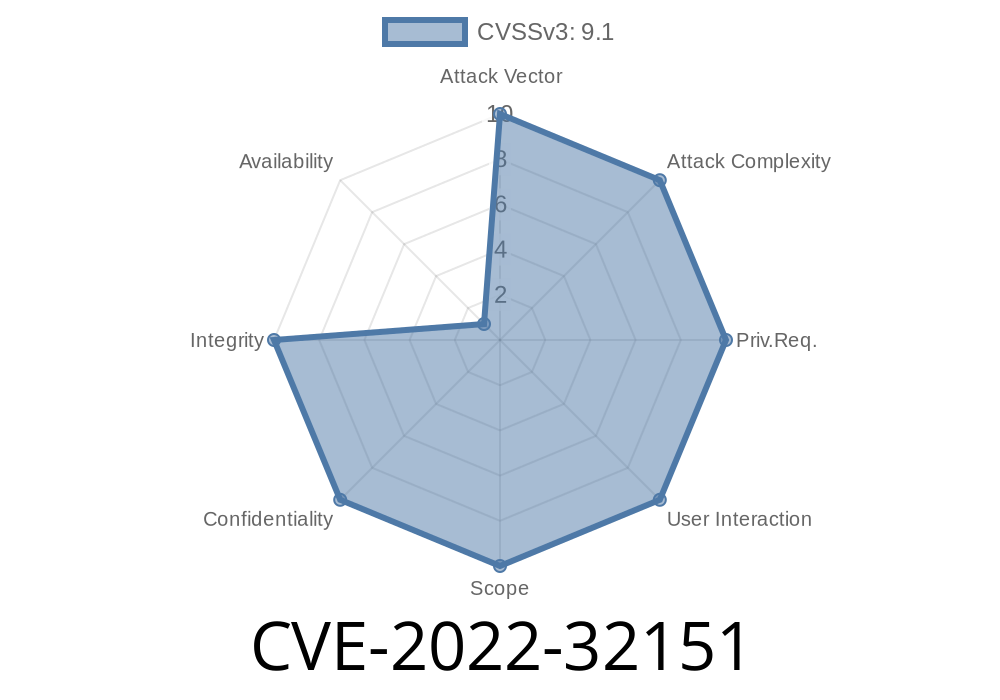
CVE-2019-10268
For Splunk Cloud Platform, update to Splunk Cloud Platform 8.2.2203 or later and Enable TLS host name validation for Splunk-to-Splunk communications (https://docs.splunk.com/Documentation/Splunk/8.2.2203/Cloud/Security/EnableTLSCertHostnameValidation) to enable the remediation. For information about which information that was potentially vulnerable when validated server certificates were disabled by default in Splunk Enterprise versions before 9.0 and Splunk Cloud Platform versions before 8.2.2203, see SECURITY RISK FACTORS (CVE-2019-10267) in the Splunk documentation.
Timeline
Published on: 06/15/2022 17:15:00 UTC
Last modified on: 06/24/2022 01:24:00 UTC
References
- https://www.splunk.com/en_us/product-security/announcements/svd-2022-0601.html
- https://docs.splunk.com/Documentation/Splunk/9.0.0/Security/EnableTLSCertHostnameValidation
- https://research.splunk.com/application/splunk_protocol_impersonation_weak_encryption_simplerequest/
- https://docs.splunk.com/Documentation/Splunk/9.0.0/Security/Updates
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-32151