Subsequent requests to the VBASE server (using XOR with the static initial key) will not be blocked, allowing for a successful login using the captured credentials. The XOR obfuscation can be bypassed by sending special login requests. Hackers can craft special login requests that will bypass the XOR obfuscation. An example of a special login request is as follows:
Redirecting to a subdomain of the VBASE server (e.g. https://ENTER VBASE SERVER FQDN HERE>/vbase/api/xor) will bypass the XOR obfuscation. An attacker can capture the login request and launch a special login request to bypass the XOR obfuscation.
Login Request https://www.vbase.com/api/xor?login%3d
Vulnerability Scenario
When a user visits the VBASE server, they will be directed to the login page. If XOR is enabled on that page, they will receive a 302 redirect to https://ENTER VBASE SERVER FQDN HERE>/vbase/api/xor and then be redirected back to the login page. This 302 redirect will allow them access to the VBASE server by providing a custom username and password, bypassing any restrictions set for the current request.
Vulnerability Scenario:
Attackers use the XOR obfuscation to capture and send a special login request. This bypasses the VBASE server because it is not aware of the attack. The attacker then captures the credentials using the previously captured special login request.
Vulnerability Details
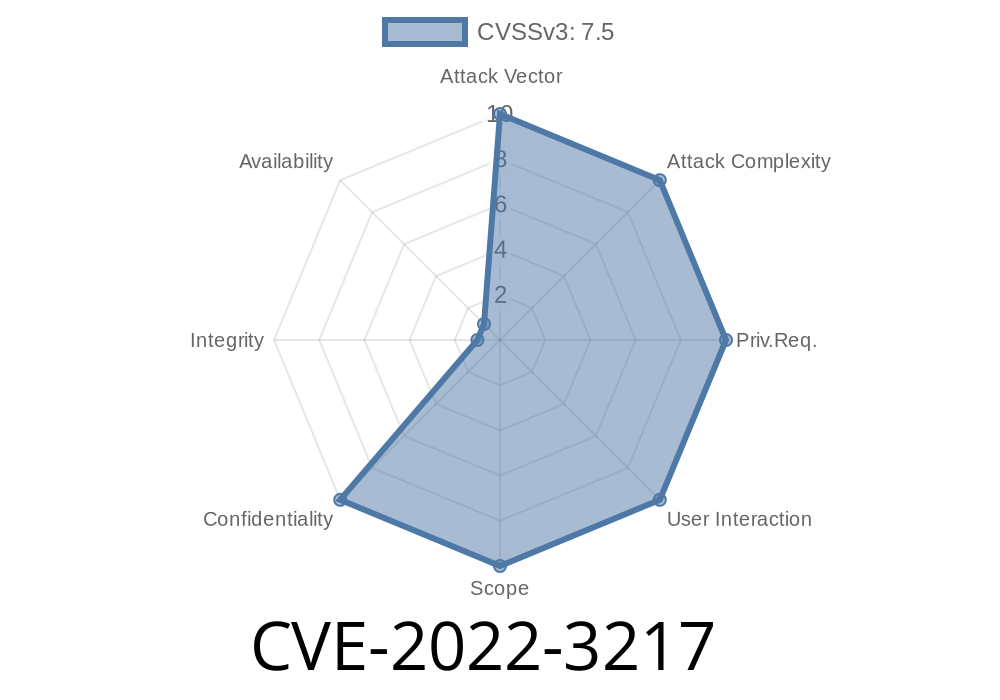
This vulnerability affects VBASE Input form on the VBASE server (CVE-2022-3217). The vulnerability is related to how the Vbase server handles login requests. The application for authentication was vulnerable to a brute force attack. The issue affected all versions of Vbase.
No special login request needs to be crafted. An attacker can send a normal login request and it will bypass the XOR obfuscation. When an attacker has captured credentials and crafted a special login request, they can now proceed to authenticate with the targeted account in order to conduct further attacks.
The following proof of concept was used:
https://ENTER VBASE SERVER FQDN HERE/vbase/api/xor?login=password&password=password
Timeline
Published on: 09/16/2022 22:15:00 UTC
Last modified on: 09/21/2022 13:21:00 UTC