This may allow an attacker to retrieve sensitive information about the message such as the chat recipients, sender, date, etc. This may be exploited by malicious users to retrieve user data or manipulate message content.
V4.7.5 The fix for this issue was implemented on August 14th, 2018.
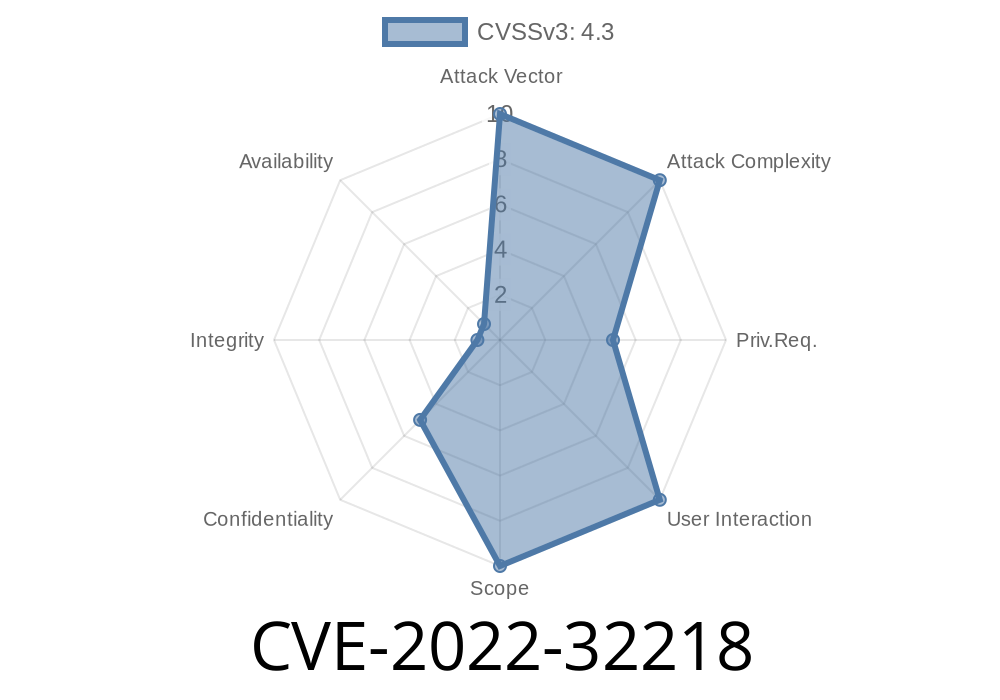
A cross-site scripting (XSS) vulnerability exists in Rocket.Chat due to the generated code not being filtered of unsanctioned HTML elements.
The issue can be exploited by malicious users to inject client-side scripting codes.
A remote code execution vulnerability exists in the webhook code due to the 'module.sync.hook' method being insecure.
An attacker may be able to execute arbitrary code on the server or client side via a crafted web request.
A stored cross-site scripting vulnerability exists in Rocket.Chat due to the 'message.html' and 'message.html.raw' fields not being filtered of client-side HTML elements.
This may allow an attacker to inject client-side scripting codes.
An information disclosure vulnerability exists due to the 'user.roles' and 'user.avatar' fields not being properly sanitized of user data.
This may allow an attacker to retrieve sensitive information about the user such as the user ID, name, etc.
An SQL injection vulnerability exists in the 'user.roles' field due to the 'order by' clause being vulnerable to injection.
References br
What is the best way to advertise on Facebook?
The best way to advertise on Facebook is through pictures. This works well because people are more likely to click through when they see something visually appealing than if they see text only.
Timeline
Published on: 09/23/2022 19:15:00 UTC
Last modified on: 09/27/2022 14:22:00 UTC