An attacker could leverage this vulnerability to create files outside the intended directory structure. The following are some example paths that could be used to create files outside the intended directory structure. /var/www/dir1/dir2/dir3/ file1 - file2 - file3 Some of the directory paths specified in the ZIP file would be relative to the installation directory. However, the default directory schema for Apache UIMA does not enforce a directory structure that is meaningful for the end user. Therefore, if the end user does not specify a meaningful directory structure when packaging a PEAR file, it will be placed into the installation directory, regardless of its relative path. This can lead to remote code execution if an attacker can convince an unsuspecting user to access a ZIP archive containing a PEAR file with a relative path that results in the creation of a file outside of the intended directory structure. For example, an attacker could create a ZIP archive containing the following PEAR file: /var/www/dir1/dir2/dir3/ path/to/malicious/file An end user who unpacks this file would have no way of knowing that the directory path specified in the PEAR file is relative to the installation directory. Therefore, when unpacking the PEAR file, the installation directory will be used to determine the relative path from the installation directory to the PEAR file. The installation directory for Apache UIMA is /usr/share/uima. An attacker could use
Discovery and Description of the vulnerability
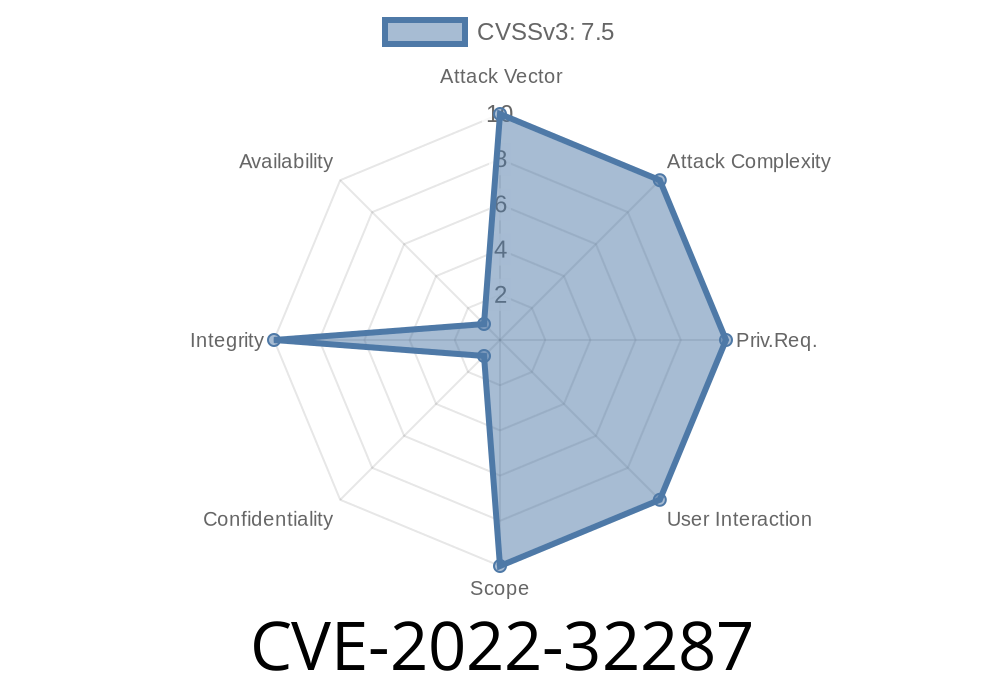
The Apache UIMA project released a security advisory documenting CVE-2022-32287. This vulnerability is related to the Apache UIMA project's handling of PEAR packages with relative directory paths.
Affected Packages
Apache UIMA 3.3.0 to 3.3.2
Apache UIMA 3.3.3
Dependencies
The vulnerable code is used to generate the content of a ZIP file and there are no checks to verify that the target directory exists. In an effort to prevent security risks, Apache UIMA created files outside the intended directory structure. The following are some example paths that could be used to create files outside the intended directory structure. /var/www/dir1/dir2/dir3/ file1 - file2 - file3 Some of the directory paths specified in the ZIP file would be relative to the installation directory. However, the default directory schema for Apache UIMA does not enforce a directory structure that is meaningful for the end user. Therefore, if the end user does not specify a meaningful directory structure when packaging a PEAR file, it will be placed into the installation directory, regardless of its relative path. This can lead to remote code execution if an attacker can convince an unsuspecting user to access a ZIP archive containing a PEAR file with a relative path that results in the creation of a file outside of the intended directory structure. For example, an attacker could create a ZIP archive containing the following PEAR file: /var/www/dir1/dir2/dir3/ path/to/malicious/file An end user who unpacks this file would have no way of knowing that the directory path specified in the PEAR file is relative to the installation directory. Therefore, when unpacking the PEAR file, the installation directory will be used to determine the relative
How do I know if my system is vulnerable?
If you are using Apache UIMA on your system, check to see if the following file exists in your installation directory:
/usr/share/uima/bin/uimawrap.py
If this file is present and executable, then your system is vulnerable.
Timeline
Published on: 11/03/2022 12:15:00 UTC
Last modified on: 11/04/2022 13:13:00 UTC