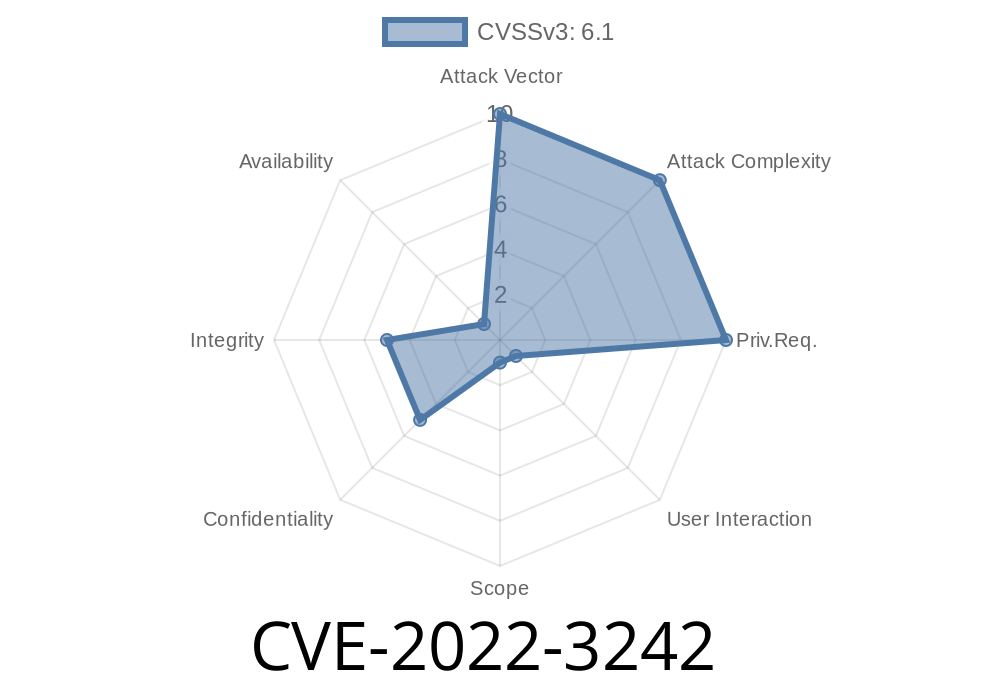
This security issue was fixed in version 1.3.2. There’s a very high risk of getting exploited when working with public repos because anyone can clone a repo, anyone can fork a repo, and anyone can push a repo to the public remote.
Unauthenticated attackers can inject malicious content into a GitHub repo. Unauthenticated attackers can view the content of a GitHub repo without having any permissions to the repo. There’s a very high risk of getting exploited when working with public repos because anyone can clone a repo, anyone can fork a repo, and anyone can push a repo to the public remote.
Red Team practitioners can use GitHub as a source for acquiring sensitive data. Red Team practitioners can clone a repo and use it to launch a reconnaissance or data exfiltration campaign. There’s a very high risk of getting exploited when working with public repos because anyone can clone a repo, anyone can fork a repo, and anyone can push a repo to the public remote.
Red Team practitioners can use GitHub as a source for acquiring sensitive data. Red Team practitioners can clone a repo and use it to launch a reconnaissance or data exfiltration campaign.
What is GitHub?
GitHub is a social coding platform that allows users to store and collaborate on code. It has over 31 million users in more than 100 countries. GitHub provides a convenient way for developers, designers, and businesses to share their work with the world and receive feedback from others.
Timeline
Published on: 09/20/2022 11:15:00 UTC
Last modified on: 09/21/2022 17:04:00 UTC