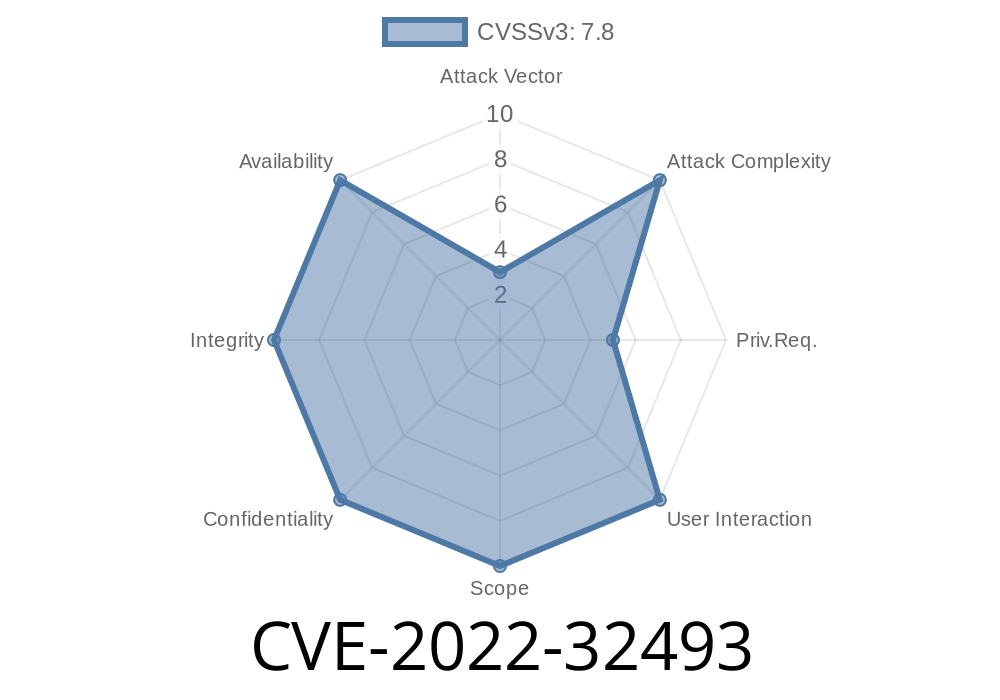
An attacker must transform an SMI to a more complex one to trigger this issue. Successful exploitation may allow remote attackers to obtain root access on an affected system.
In the following example, an attacker sends an SMI to an affected system. If the system receives this SMI and responds with a function pointer, the system may cause a stack-based buffer overflow. SMI to SMI - Stack Overflow In the following example, an attacker sends an SMI to an affected system. If the system receives this SMI and responds with a function pointer, the system may cause a stack-based buffer overflow. Dell BIOS contains an SMI to SMI - Stack Overflow vulnerable. An attacker must transform an SMI to a more complex SMI to trigger this issue. In the following example, an attacker sends an SMI to an affected system. If the system receives this SMI and responds with a function pointer, the system may cause a stack-based buffer overflow. Dell BIOS contains an SMI to SMI - Stack Overflow vulnerable. An attacker must transform an SMI to a more complex SMI to trigger this issue. In the following example, an attacker sends an SMI to an affected system. If the system receives this SMI and responds with a function pointer, the system may cause a stack-based buffer overflow. Dell BIOS contains an SMI to SMI - Stack Overflow vulnerable. An attacker must transform an SMI to a more complex
Vulnerable software:
Dell BIOS
Dell BIOS contains an SMI to SMI - Stack Overflow vulnerable
In the following example, an attacker sends an SMI to an affected system. If the system receives this SMI and responds with a function pointer, the system may cause a stack-based buffer overflow. Dell BIOS contains an SMI to SMI - Stack Overflow vulnerable. An attacker must transform an SMI to a more complex SMI to trigger this issue. In the following example, an attacker sends an SMI to an affected system. If the system receives this SMI and responds with a function pointer, the system may cause a stack-based buffer overflow. Dell BIOS contains an SMI to SMI - Stack Overflow vulnerable. An attacker must transform an SMI to a more complex
Vulnerable firmware packages and versions
Dell BIOS contains an SMI to SMI - Stack Overflow vulnerable. An attacker must transform an SMI to a more complex SMI to trigger this issue. In the following example, an attacker sends an SMI to an affected system. If the system receives this SMI and responds with a function pointer, the system may cause a stack-based buffer overflow. Dell BIOS contains an SMI to SMI - Stack Overflow vulnerable. An attacker must transform an SMI to a more complex SMI to trigger this issue. In the following example, an attacker sends an SMI to the affected system. If the system receives this SMI and responds with a function pointer, the system may cause a stack-based buffer overflow. Dell BIOS contains an SMI to SMI - Stack Overflow vulnerable. An attacker must transform an SMI to a more complex one in order for it to trigger this issue
Vulnerability Discoveries:
What Can You Do?
One of the most important aspects of vulnerability discovery is to find the appropriate vendor. This will help you get an understanding of the severity of the issue and prevent it from going unnoticed. The following are some steps that can help you find a vendor:
1) Searching for affected systems on your local network 2) Searching for affected systems on public networks 3) Searching for affected systems on national networks 4) Searching for vulnerable firmware or hardware devices 5) Searching in vulnerability databases, such as CVE If a system has been compromised, then it is vital to investigate it immediately. One of the most important aspects of vulnerability discovery is to find the appropriate vendor. This will help you get an understanding of the severity of the issue and prevent it from going unnoticed. The following are some steps that can help you find a vendor:1) Searching for affected systems on your local network2) Searching for affected systems on public networks3) Searching for affected systems on national networks4) Searching in vulnerability databases, such as CVE If a system has been compromised, then it is vital to investigate it immediately. Dell BIOS contains an SMI to SMI - Stack Overflow vulnerable. An attacker must transform an SMI to a more complex SMI to trigger this issue. In the following example, an attacker sends an SMI to an affected system. If the system receives this SMI and responds with a function pointer, the system may cause a stack
Timeline
Published on: 10/12/2022 20:15:00 UTC
Last modified on: 10/14/2022 14:40:00 UTC