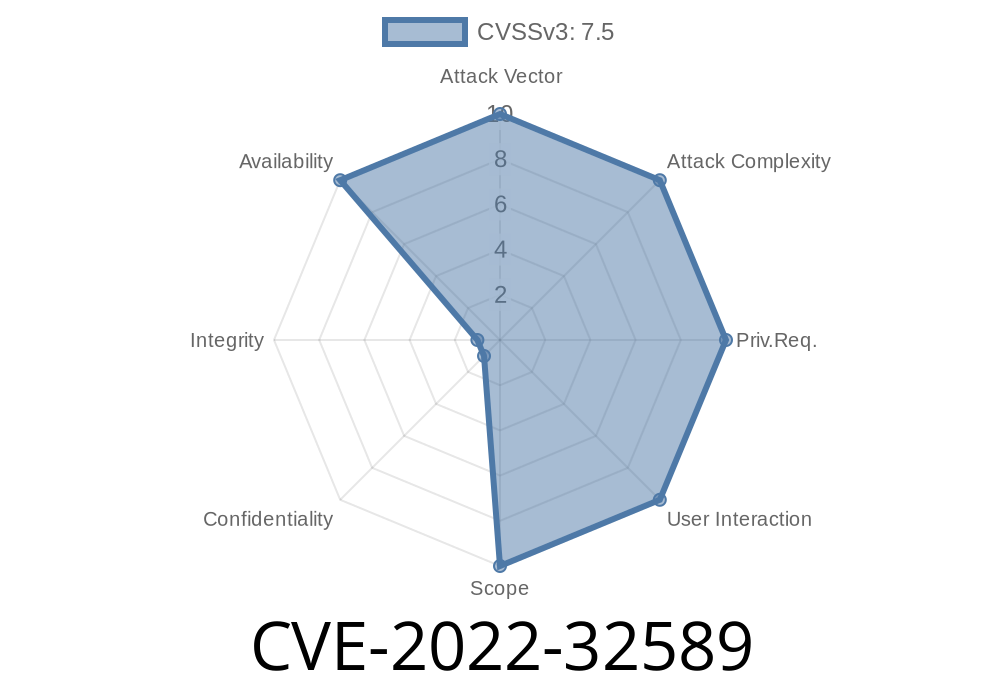
When parsing network traffic, Wi-Fi driver does not properly handle trailing data that does not arrive in expected order. This could be exploited by 3rd party applications to force disconnection. Wi-Fi driver does not properly validate the total length of data received from the network stack, allowing exploitation by a specially crafted network packet. This can be leveraged by a remote attacker to cause a denial of service condition. Patch ID: ALPS07030600; Issue ID: ALPS07030600. When parsing network traffic, Wi-Signal does not properly handle trailing data that does not arrive in expected order. This could be exploited by 3rd party applications to force disconnection.
In Wi-Fi driver, there is a possible way to disconnect Wi-Fi due to an improper resource release. This could lead to remote denial of service with no additional execution privileges needed. User interaction is not needed for exploitation. An attacker can create a specially crafted network packet that triggers this condition, giving the attacker the ability to disconnect the Wi-Fi module. Patch ID: ALPS07030600; Issue ID: ALPS07030600. When parsing network traffic, Wi-Signal does not properly handle trailing data that does not arrive in expected order. This could be exploited by 3rd party applications to force disconnection. Wi-Signal does not properly validate the total length of data received from the network stack, allowing exploitation by a specially crafted network packet. This can be leveraged by
Vulnerable Code and Resources
In Wi-Fi driver, there is a possible way to disconnect Wi-Fi due to an improper resource release. This could lead to remote denial of service with no additional execution privileges needed. User interaction is not needed for exploitation. An attacker can create a specially crafted network packet that triggers this condition, giving the attacker the ability to disconnect the Wi-Fi module. Patch ID: ALPS07030600; Issue ID: ALPS07030600.
Wi-Signal does not properly validate the total length of data received from the network stack, allowing exploitation by a specially crafted network packet. This can be leveraged by 3rd party applications to cause a denial of service condition. Patch ID: ALPS07030600; Issue ID: ALPS07030600.
Timeline
Published on: 10/07/2022 20:15:00 UTC
Last modified on: 10/12/2022 13:49:00 UTC