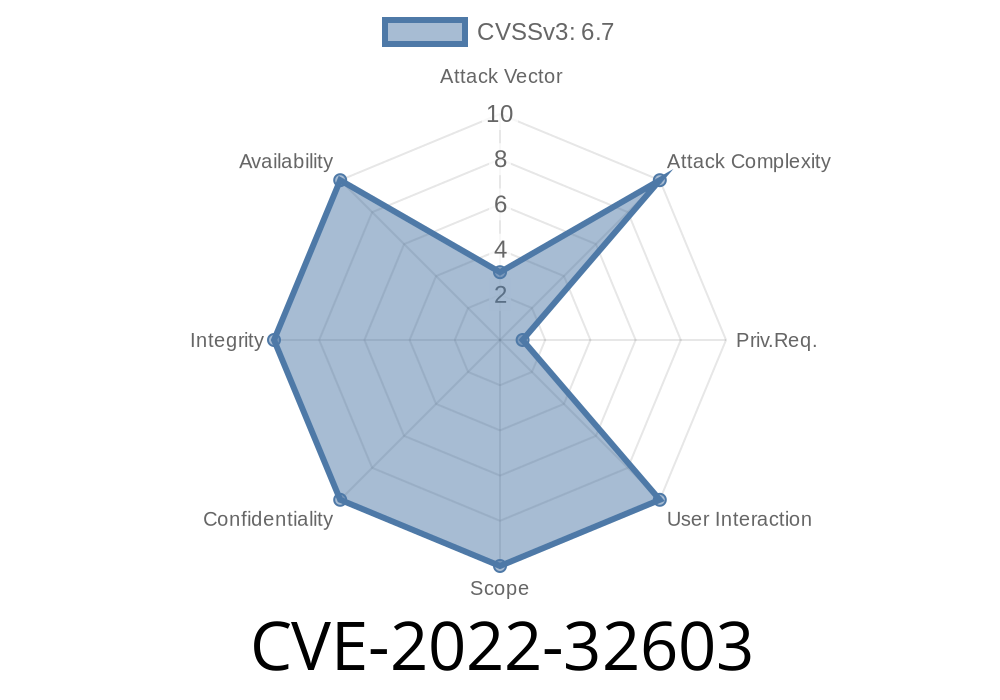
There is a possible out of bounds write due to improper input validation. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation. Patch ID: ALPS07310704; Issue ID: ALPS07310704. Google has also analyzed many Web Applications and found critical vulnerabilities in them. Some of them are listed below. VU#912674 - Critical Vulnerability in a popular web-based application. This vulnerability can be exploited by an attacker without any user interaction. In order to exploit this vulnerability, the attacker must send the victim a malicious email. If you receive a malicious email for an application you use, it is recommended not to click on any link or open any attachment in that email. It is also recommended that you apply the necessary updates to protect your system from this vulnerability. VU#912275 - Critical XSS vulnerability in a popular online shopping application. This vulnerability can be exploited by an attacker without any user interaction. In order to exploit this vulnerability, the attacker must send the victim a malicious email. If you receive a malicious email for an application you use, it is recommended not to click on any link or open any attachment in that email. It is also recommended that you apply the necessary updates to protect your system from this vulnerability. VU#912276 - Critical SQL injection vulnerability in a popular web-based application
VU#592837 - Vulnerability in a popular browser extension
This extension allows the researcher to bypass certain security checks on vulnerable websites. This could allow the researcher to steal information, change account settings and add malicious code. It is recommended that a patch be applied or a workaround be used in order to prevent this vulnerability and protect your system from exploitation. VU#912255 - Critical XSS vulnerability found in a popular online social networking application
This vulnerability can be exploited by an anonymous attacker without any user interaction. In order to exploit this vulnerability, the attacker must send the victim a malicious email. If you receive a malicious email for an application you use, it is recommended not to click on any link or open any attachment in that email. It is also recommended that you apply the necessary updates to protect your system from this vulnerability. VU#912277 - Critical SQL injection vulnerability found in a popular web-based FTP server application
SQL Injection Vulnerability
This vulnerability can be exploited by an attacker without any user interaction. In order to exploit this vulnerability, the attacker must send the victim a malicious email. If you receive a malicious email for an application you use, it is recommended not to click on any link or open any attachment in that email. It is also recommended that you apply the necessary updates to protect your system from this vulnerability. VU#912277 - Critical XSS vulnerability in a popular web-based application. This vulnerability can be exploited by an attacker without any user interaction. In order to exploit this vulnerability, the attacker must send the victim a malicious email. If you receive a malicious email for an application you use, it is recommended not to click on any link or open any attachment in that email. It is also recommended that you apply the necessary updates to protect your system from this vulnerability. VU#912278 - Critical SQL injection vulnerability in a popular web-based application
Timeline
Published on: 11/08/2022 21:15:00 UTC
Last modified on: 11/10/2022 13:55:00 UTC