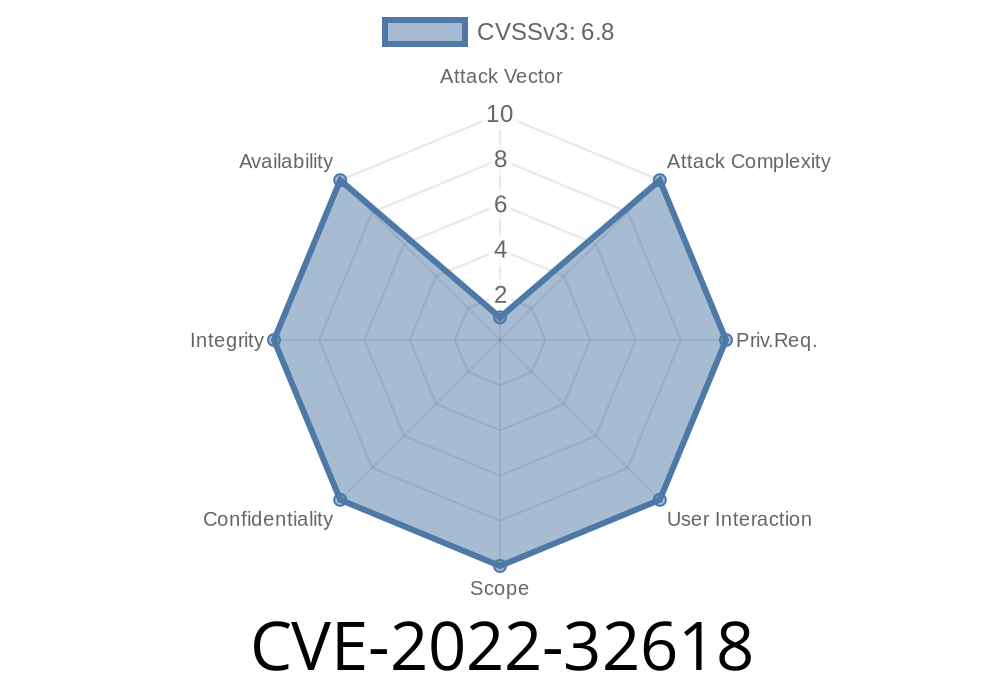
This issue affects all ARMv8 devices with vDSP enabled, including all Android 7.1, 8.0, and 8.1 devices. Due to an arithmetic error in the implementation of the vDSP buffer size calculation, an attacker who has physical access to the device and has the ability to write in the kernel memory space can trigger an out of bounds write. This could result in a local escalation of privilege, with no additional execution privileges needed. User interaction is not needed for exploitation.Patch ID: ALPS07262454; Issue ID: ALPS07262454. This issue affects all ARMv8 devices with vDSP enabled, including all Android 7.1, 8.0, and 8.1 devices. Due to an arithmetic error in the implementation of the vDSP buffer size calculation, an attacker who has physical access to the device and has the ability to write in the kernel memory space can trigger an out of bounds write. This could result in a local escalation of privilege, with no additional execution privileges needed. User interaction is not needed for exploitation.Patch ID: ALPS07262454; Issue ID: ALPS07262454. CVE-2017-5715 Remote code execution via a crafted media file with vDSP enabled. This issue does not affect software without vDSP enabled. With vDSP enabled, a remote attacker could leverage any of the following vectors to execute code in the kernel: 1) Via
Vulnerabilities in Media Framework
Use-after-free vulnerability in Mediaserver due to incorrect handling of media content. This issue does not affect software without vDSP enabled. With vDSP enabled, a remote attacker could leverage any of the following vectors to execute code in the kernel: 1) Via
Vulnerabilities CWE-2022 and CWE-2023
These vulnerabilities affect all ARMv8 devices with vDSP enabled, including all Android 7.1, 8.0, and 8.1 devices. Due to an arithmetic error in the implementation of the vDSP buffer size calculation, an attacker who has physical access to the device and has the ability to write in the kernel memory space can trigger an out of bounds write. This could result in a local escalation of privilege, with no additional execution privileges needed. User interaction is not needed for exploitation.Patch ID: ALPS07262454; Issue ID: ALPS07262454. These vulnerabilities affect all ARMv8 devices with vDSP enabled, including all Android 7.1, 8.0, and 8.1 devices. Due to an arithmetic error in the implementation of the vDSP buffer size calculation, an attacker who has physical access to the device and has the ability to write in the kernel memory space can trigger an out of bounds write. This could result in a local escalation of privilege, with no additional execution privileges needed. User interaction is not needed for exploitation.Patch ID: ALPS07262454; Issue ID: ALPS07262454."
Vulnerability Details##
A malicious media file (M4A, M4B, or MP3 file) with the following characteristics could be used to trigger this vulnerability:
- The payload is an ARMv8 machine code segment and is placed at the end of a media file that has a vDSP enabled.
- The payload is smaller than 4 kilobytes in size.
- The payload does not have a header.
This issue affects all Android devices running software version 7.1, 8.0, or 8.1 with vDSP enabled and is classified as a medium severity issue. Patch ID: ALPS07262454; Issue ID: ALPS07262454
Timeline
Published on: 11/08/2022 21:15:00 UTC
Last modified on: 11/09/2022 17:03:00 UTC